- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- NXP Tech Blogs
- :
- NXP Tech Blog
- :
- MCUXpresso Secure Provisioning v2 Now Available
MCUXpresso Secure Provisioning v2 Now Available
MCUXpresso Secure Provisioning v2 Now Available
- RSS フィードを購読する
- 新着としてマーク
- 既読としてマーク
- ブックマーク
- 購読
- 印刷用ページ
- 不適切なコンテンツを報告
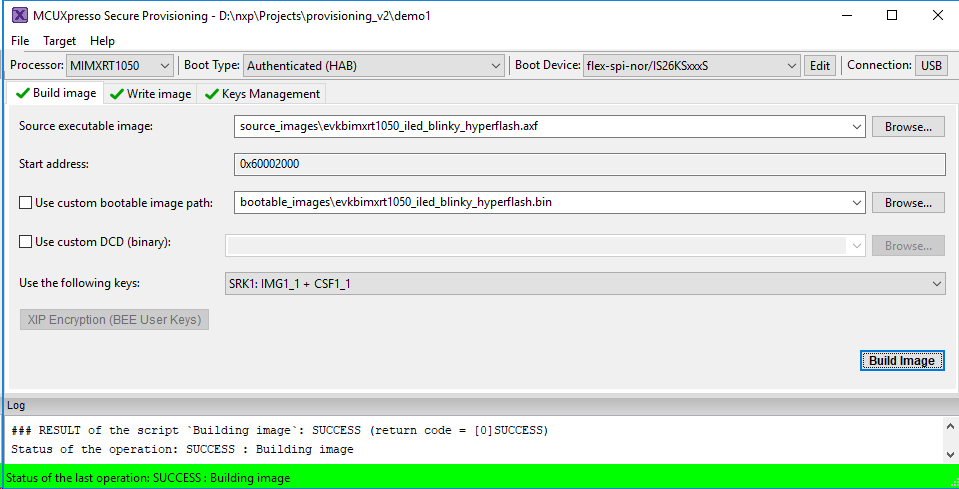
Features
- Support for i.MX
- RT1020, RT1050, RT1060 and RT1064
- Support for LPC
- LPC55S6x, LPC55S2x and LPC55S1x
- Unsigned, HAB signed and HAB encrypted Secure Boot modes
- Conversion of ELF executables, SREC and raw binaries into bootable images files
- Generation and management of keys, signatures and certificates associated with the image
- Connectivity to the target via UART, USB-HID.
- Writing FlexSPI NOR or SD card boot device including configuration of the boot device parameters
- Use of DCD configuration enabling booting into SDRAM images
- Programming eFuses per image and use case requirements
- Optional generation of batch scripts usable later without the GUI
- Streamlined operation for general users
Downloads
- To download the installer, please login to our download site via:
Revision History
- 2.0
- Added support for i.MX RT1020 and i.MX RT1064
- Added support for LPC55S6x, LPC55S2x and LPC55S1x
- Unsigned, Unsigned CRC and Signed boot modes
- TrustZone support (bin + json)
- Key Management – Secure Boot, Generation of ROT keys
- BEE boot for i.MX RT10xx
- OTPMK
- SW-GP2/GP4
- Import/Export Keys between workspaces
- Improved connection dialog, it supports UART test connection, improved processor detection and detection of fuses status
- 1.0.1
- Added support for Mac OS X Catalina (10.15) + Ubuntu 18.04
- Fixed termination of sub-processes of long-running tasks.
- 1.0
- Initial version
Known problems and limitations
- General
- On Windows platform make sure the windows FIND utility is found first on the PATH (GNU findutils could break the functionality)
- On Linux platform the USB and/or Serial device files has to be readable and writable by current user. See resources/udev/99-secure-provisioning.rules installed into /etc/udev/rules.d/99-secure-provisioning.rules that solves this issue. On user's machine can be conflicting rule with higher priority. In case of conflict, update the conflicting rule or make this rule file with higher priority by renaming the file with lower number at beginning.
- Application has to be installed into location where the user has write access.
-
Workspace cannot contain space in the path
-
Secure Provisioning Tool does not burn all possible security features that are available. Only those required by the selected boot type are configured.
-
Mac OS X
-
Closing application using App Menu "securep | Quit securep" doesn't save the workspace setting. Either save settings using menu "File | Save Settings" or use "File | Exit" or use Close button on title bar, which saves the workpsace settings automatically.
-
Selection of wrong UART in connection dialog may cause the test connection operation takes too long and hang up. Killing sdphost and blhost processes will shorten the dialog freeze.
-
-
Windows
-
Workspace cannot be placed on different disk drive letter then the application is installed.
-
-
i.MX RT10xx
-
BT_FUSE_SEL is not burned so the boot device is based on corresponding GPIO pins.
-
Parameter "enable_encrypted_XIP" in write script is not properly supported and might not work; this feature is not used in GUI.
-
-
LPC Signed Boot Type:
-
Write requires keys selected on Build tab
-
Confirmation dialog for enabling security is displayed even security is already enabled
-
Write scripts requires the cmpa.bin and cfpa.bin files exist on the disk; on CLI it is necessary to manually modify write script to create them
-
-
LPC Trust Zone
-
CLI does not allow to set/override the Trust Zone Settings. If Trust Zone has to be configured and applied in CLI,
workspace has to be configured with Trust Zone settings in GUI in advance. -
Configuration of Trust Zone is not supported for Unsigned image
-
ここにコメントを追加するには、ご登録いただく必要があります。 ご登録済みの場合は、ログインしてください。 ご登録がまだの場合は、ご登録後にログインしてください。
-
101
7 -
Automotive Ethernet
3 -
communication standards
11 -
General Purpose Microcontrollers
31 -
i.MX RT Processors
50 -
i.MX Processors
76 -
Interface
12 -
introduction
32 -
LPC Microcontrollers
73 -
MCUXpresso
42 -
MCUXpresso Secure Provisioning Tool
1 -
MCUXpresso Conig Tools
31 -
MCUXpresso IDE
51 -
MCUXpresso SDK
35 -
MCX
12 -
Model-Based Design Toolbox
6 -
Motor Control
2 -
MQX Software Solutions
2 -
PMIC
12 -
QorIQ Processing Platforms
1 -
QorIQ Devices
8 -
S32N Processors
5 -
S32Z|E Processors
7 -
Security
12 -
Sensor
5 -
SW | Downloads
17 -
Technology Focus
12 -
日本語ブログ
74
- « 前へ
- 次へ »