- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- 本人確認とセキュリティ
- :
- セキュア認証
- :
- SE050 ECKeySessionInternalAuthenticate 6a80
SE050 ECKeySessionInternalAuthenticate 6a80
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I am using OMSE050ARD, i'm trying to start an eckey session but i seem to be getting 6A80 whenever i try to call ECKeySessionInternalAuthenticate.
Select Applet: 00a4040010a000000396545300000001030000000000
Response: 0301006fff010b9000
Create Session: 8004001b0641047fff020108
Response: 4182000801124e0147cc788a 9000
ECKeySessionGetECKAPublicKey (wrapped in processSessionCmd):
8005000017100801124e0147cc788a410b84cabf2106a60483020000
Response: 7f4946b041045c687ea7258d61a43b7a8255ad7102cb17377b1ff253f3504ca23028edd9a5df76e6645f85cd9e206a27d87eeffddcd9417c772271e373689065c302771c7d0ff001035f37473045022032279f5688fd0d0dfa25d46c3fc99db5d5b156932516fb52749c5fb22d0a91f1022100c2e11a115ac529bb7b281cecf49cb8cb5769b29c2afd577eeee016b70c5c0e35 9000
Host Ephemeral PublicKey: 0427cefa0865a912cc36a733d659fc4077abb5faa25029d7ed0f4521ff1ba715ff6af976b6ebd6c5f3c0f62dace1859fa64e9116aa7cc8ba4d2659709881fdcb4a
Host Signature: 3045022100ecc7d866b6d1425ab7d7d0ab8c84297e98a1a968d7ece420f0236f9e37c274b702200a73f417b980976b2ef6425364258a86bfbab9a691b2ddc17e4505073b6dbb8e
ECKeySessionInternalAuthenticate (wrapped in processSessionCmd): 80050000c4100801124e0147cc788a4181b784880000b2a61d4f10a00000039654530000000103000000009003ab01408001888101107f4946b0410427cefa0865a912cc36a733d659fc4077abb5faa25029d7ed0f4521ff1ba715ff6af976b6ebd6c5f3c0f62dace1859fa64e9116aa7cc8ba4d2659709881fdcb4af001035f37473045022100ecc7d866b6d1425ab7d7d0ab8c84297e98a1a968d7ece420f0236f9e37c274b702200a73f417b980976b2ef6425364258a86bfbab9a691b2ddc17e4505073b6dbb8e
Response: 6a80
- The documentation specifies that the TLVs (0xA6 and 0x7F49) must be signed with the S_RMAC key.
- However, the S_RMAC key cannot be derived until after the secure session is established, which happens later in the process.
- Should the host ephemeral private key be used for signing instead of the S_RMAC key?
解決済! 解決策の投稿を見る。
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
No problem! Please kindly refer to the attachment for details.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
Maybe there is some misunderstanding here. I found you created the ECKey session with ID of 7fff0201, which is provisioned as ECKA pair at SE for EC key Session Authentication, but from my understanding, this session should be created with the ID to store the PK.Host.ECDSA . so the host side should generate Host.ECDSA at first and write PK.Host.ECDSA as authentication object in SE with a non-reserved ID (e.g. 0x00001000), then create the ECKey session with this ID instead.
Hope that makes sense,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
This figure has been confirmed as a doc issue, the public key from the host and provisioned in SE shall be referenced there.
Hope that makes sense,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Does it mean i need to write a new key to the secure element each time a new host is interacting with the secure element?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
What would be the most efficient way to establish a secure session each time a new smartphone initiates communication with the secure element?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
For such case, the NFC phone needs to generate the Host.ECDSA key pair natively and writes the PK.Host.ECDSA into SE from the beginning and then starts to establish an ECKey session with SE, and as writing PK.Host.ECDSA into SE causes NVM writes , so the key ID to store PK.Host.ECDSA in SE has to be created as transient object and please reserve multiple objects for back up so that the NFC phone may have a list of them all and select either of them as an Auth Object.
Hope that makes sense,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
Sorry, my bad! The authentication object must be persistent, but as writing ECKey pair always cause NVM writes, so you better let the hosts have the key pair used for authentication after they are registered.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
This brings me back to the same issue: how can I establish an EC key session? Is it possible to do so using the pre-provisioned key 7FFF0201?
It would be extremely helpful if you could provide an APDU example demonstrating how to establish a secure EC key session.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
The authentication object can be trust provisioned out of factory with a secure service, such as edgelock2go secure service , and you may refer to the https://www.nxp.com/products/security-and-authentication/secure-service-2go-platform:SECURE_SERVICE_... for details.
To have an APDU command example regarding how to establish a secure EC key session, you may simply enable ECKey Auth type for the MW and enable the verbose log, so you may have the APDU log when you run any MW example after rebuilding the MW.
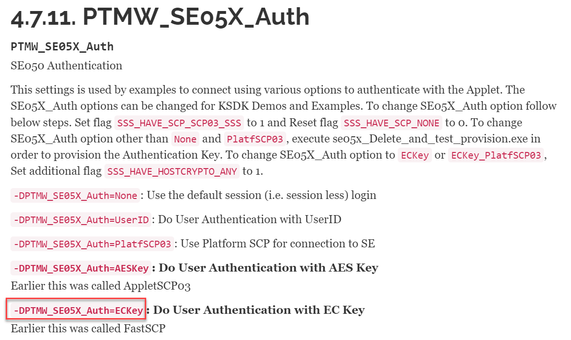
Please kindly refer to the following for details.
Hope that helps,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @jychab ,
No problem! Please kindly refer to the attachment for details.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------