- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
CSEc for storing keys
Can someone please explain in detail summary what below functions will do in csec_keyconfig example project.
/* Initialize Flash for CSEc operation */
initFlashForCsecOperation();
/* Load the MASTER_ECU key with a known value, which will be used as Authorization key (a secret key known by the application in order to configure other user keys) */
setAuthKey();
/* Load the selected key First load => counter == 1 */
keyLoaded = loadKey(CSEC_KEY_1, key, 1);
CSEC_DRV_EncryptECB();
Sorry for asking this questions blindly. Though in debug mode by single stepping the source code, I could understand it theoretically.
But I want to program my own security keys to CSEc module in our products before releasing it to market.
So it would be of great help if someone explains it with S32K144 context and how it works.
Hi Veronica,
Thanks for the reply. I shall investigate more from my side.
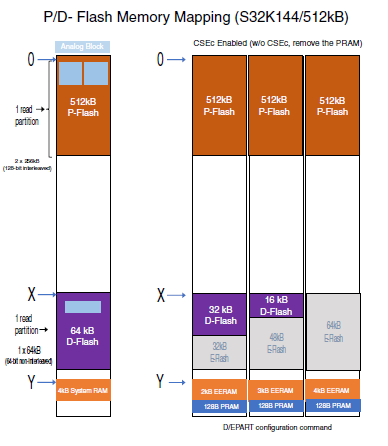
From Data spec of S32K144, I only understand there is 512 KB of flash and 64 KB of system RAM.
But from one of reference manual of S32K144, I got below screenshot which I am not able to interpret. Can you please provide more information if you can please ?
Referring to below screenshot, I know PRAM is of 128 Bytes.
Thanks
Mohan
Hello Mohan,
Please find below an explanation for each of the functions mentioned by you.
initFlashForCsecOperation(void):
- checks if the Flash was partitioned for CSEc operation;
- if not, partition the Flash and select the number of user keys - FLASH_DRV_DEFlashPartition(&flashSSDConfig, 0x2, 0x4, 0x3, false, true);
- the 0x3 parameter specifies that there will be 24 available user keys; for more details, please see the documentation of the FLASH_DRV_DEFlashPartition function.
setAuthKey(void):
- this function sets the MASTER_ECU key with the value of g_authIdKey (in the csec_utils.c source file);
- in order to be able to configure a non-volatile key, a secret (the value of the key) must be known; in this case, we will use the MASTER_ECU key (which can be used for updating any of the keys) as our secret when setting up the user keys;
- this function will compute the M1-M3 values according to the SHE specification and then load the key by passing the computed values to the CSEC_DRV_LoadKey function;
- in order to compute the values, the computeM1M2M3 function is used, receiving as first parameter g_emptyKey, as the first time we load the MASTER_ECU key, coming from a clean state, the slot will be empty.
loadKey(CSEC_KEY_1, key, 1):
- this function will load the first user key with the value specified by the key parameter;
- the last parameter, the counter, needs to be incremented each time you update the key; the CSEc module will not update the key if the counter is <= the previous counter used when storing the key;
- this function will also compute the M1-M3 values according to the SHE specification and then load the key by passing the computed values to the CSEC_DRV_LoadKey function;
- the first parameter of computeM1M2M3 will be g_authIdKey, as we are using the value of MASTER_ECU as the secret needed when updating the key.
CSEC_DRV_EncryptECB(CSEC_KEY_1, plainText, 16, cipherText):
- this function will encrypt the plainText using the user key loaded previously and output the result into the cipherText parameter;
- the plain text will be encrypted using AES-128 with the ECB mode of chaining.
Please note that if you plan to use another MASTER_ECU key, you should first erase the keys by updating the value of the ERASE_ALL_KEYS macro to 1.
I hope this answers your question. If not, let me know and I will go into more detail.
Best regards,
Veronica
Hi
ERC_KEY_UPDATE_ERROR occurs when I use setAuthKey to read the error bit. The manual explains ERC_KEY_UPDATE_ERROR. Example: key update authentication failed; for
LOAD_KEY : M3 =! M3* or UID is empty and AuthID isn't the same key slot, how can I determine the specific cause, I guess AuthID isn't the same key slot, how can I solve this problem.
Hi Veronica,
Thanks a lot.
This is the information I was looking for. Its very clear.
I need couple of clarifications if you don't mind:
1. Assume we are going to release 100 products with S32K144 MCU. Should we be programming same security keys(to CSEc module) in all 100 products ?
2. Assume product has Application processor(Qualcomm snapdragon) and S32K144 MCU communicating over UART. How I can use CSEc module of S32K144 to validate messages received from application processor and vice versa.
3. When messages are exchanged between two S32K144 EVB over CAN. How CAN message is protected from intruders. How CSEc module works in this case ?
Hello Mohan,
Unfortunately I cannot answer the three questions, as it depends on the application and how exactly it uses the keys. These questions should probably be answered by a security architect, having a complete overview of the system.
In terms of CSEc features which could be used for providing confidentiality and authentication, the module provides:
- AES-128 encryption using ECB and CBC chaining modes
- AES-128 CMAC calculation and authentication
Best regards,
Veronica