- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- i.MX フォーラム
- :
- i.MX RT クロスオーバーMCU
- :
- Re: Enable OTFAD function , then jump to application code will failure
Enable OTFAD function , then jump to application code will failure
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
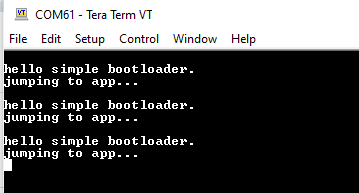
Hi All
The customer build bootloader by himself, but encounter some issue.
Disable OTFAD function, application code address start from 0x60020000.
bootloader can jump to application.
Enable OTFAD function, encryption application code address start from 0x60020000.
bootloader can't jump to application.
Enable OTFAD function, encryption application code address start from 0x60021000.
bootloader can jump to application.
Could you tell us how to do can fix this issue? or the first 4K bytes of the application code can't be encrypted.
attached file is the customer sample code.
Bootloader (evkmimxrt1010_dev_hid_generic_bm): 0x60000000
Application(evkmimxrt1010_flexspi_nor_polling_transfer): 0x60020000
Thanks.
解決済! 解決策の投稿を見る。
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Omar_hong
Thank you for your reply, we have a suggestion, please try on your side and let me know your results.
Change clock init as below:
CLOCK_InitSysPfd(kCLOCK_Pfd3, 19);
CLOCK_SetMux(kCLOCK_PrePeriphMux, 2);
We found that ENET PLL have an impact for OTFAD decryption when both bootloader and application did ENET PLL initiation.
This is a special case for your test environment and the one I created.
Looking forward to hear from you.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Felix_ar
Thank you for reaching out!
I understand that the customer can use OTFAD to decrypt automatically code, but to achive this they had to increase by 1K the offset of their application ( from 0x6002_0000 to 0x6002_1000) and they want to know why.
I quickly checked the customer bootloader source code, but it is not clear for me how are they enabling/setting the OTFAD prior to jump to the application, could you describe this?
Did they configured OTFAD only for the application or for the bootloader or both? How ?
Another question is : can we reproduce this with our MIMX RT1010 -EVK?
Thank you!
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thank you reply.
1. The customer use MCUXpresso Secure Provisioning Tool v9 to enable OTFAD function.
2. Only encryption application code.
3. MIMX RT1010 -EVK can reproduce this issue.
below is Secure Provisioning Tool v9 setting screenshot.
Fail
Pass
Thank you.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Felix_ar
Thank you for letting me know, I am working to see if I can replicate this on my end.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Felix_ar
Thank you very much for your patience, I appreciate.
I was able to get application working in plain mode.
But I am still diagnosing why you can not setup OFTAD at 0x6002_0000 and boot.
Just a question, how are you creating and loading the secondary application?
With the SPT is easy to program the bootlaoder and the flexSPI application as an additional image. but I do not know the process you are following.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Omar_hong
I just want to maintain you updated.
I have been testing further by elaborating more tests on own ( for example by encrypting both both bootloader and app together and still I am getting failures to boot to the application. Everything works well with boot to plain mode
I do apologize for the inconvenience, as the investigation still goes on.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thank you for your reply. If there are any details or questions you want to know, please let me know as soon as possible.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Omar_hong and @Felix_ar
I want to maintain you updated.
I think I managed to replicate your issue on my end, I thank you for your files and code, they help me as reference. But this still work in progress ( see last paragpraph ). Please take a look at my testing.
I created my own bootloader image at 6000_2000 and led_blinky image at 0x6002_0000, then I merged together to create a single binary. Easiest way I found to create a single binary with both bootloader and application was write both applications and export the memory contents of the flash using Segger's J-MEM. I created a single binary to use the SPT to encrypt the image with ease.
Below my test results.
1 If I set OTFAD Region 0 to 0x6002_1000 ( 4 KB offset from entry of led_blinlky application), which is after the application entry, I can successfully boot the application.
Below application memory details.
Below evidence.
2 If I set OTFAD region 1 to 0x6002_0000, encrypting the vector table, main function and a bit of the first part of the application, I can NOT boot the application. .
You can see the resets I made, jump can not be achieved.
3 If I set OTFAD region 0 to 0x6000_2000, or 0x6000_1000 , encrypting the vector table, main function and and a bit of the first part of the bootloader. I can boot the bootloader and the application
So far, boot of the application at 0x6002_0000 works if OTFAD is set to 0x6002_1000. You are not loosing any space, but the first 4 KB of the application are in plain. So what is next? I where able to replicate the problem on the bench, so I am discussing this internally, to provide you a clarification.
I appreciate your patience and disposition.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thank you for your response. I look forward to your further results.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Omar_hong and @Felix_ar
Just to maintain you updated, I just need more additional time, as I am waiting for feedback, internally.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Felix_ar and @Omar_hong
I have more updates on this after, thanks to my internal discussion.
After some debugging by following the test environment I created (based on yours) the problem is mostly caused by same clock reconfiguration twice in both simple bootloader and app image. If we compile app image with clock_config.o and fsl_clock.o in RAM, then we could encrypt the whole app image starting from 0x6002_0000.
We are trying to analyze the root cause with designer for clock tree.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thank you for your prompt response. I look forward to your root cause analysis of this issue.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Omar_hong
Thank you for your reply, we have a suggestion, please try on your side and let me know your results.
Change clock init as below:
CLOCK_InitSysPfd(kCLOCK_Pfd3, 19);
CLOCK_SetMux(kCLOCK_PrePeriphMux, 2);
We found that ENET PLL have an impact for OTFAD decryption when both bootloader and application did ENET PLL initiation.
This is a special case for your test environment and the one I created.
Looking forward to hear from you.
Diego
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @diego_charles ,
This initially seems to have resolved the issue. I will try it out more in other board. Thank
you very much for your assistance.
If there are no further problems, I will close this issue.
Thank you once again for your great assistance !
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @Omar_hong
We are very glad to know that the problem is solved, we appreaciate your interested ( and patience during our testing and troubleshooting )
Diego