- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- 本人確認とセキュリティ
- :
- セキュア認証
- :
- Verify attestation in practice
Verify attestation in practice
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I populate the SE05x with a bunch of data and keys. One of the keys is considered to be the primary device key and can be used for attestation. Now I read back some of those properties and ask for attestation with said key, after which all of the data is transferred to the back office.
According to AN12543, there's a bunch of low level inputs being used as inputs for signature with the selected secure object:
It's clear that none of these inputs cannot be easily generated offline in order to be able to verify the attestation signature. So, the question is, how to verify this in practice? What is the recommended way?
解決済! 解決策の投稿を見る。
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @bboozzoo ,
Actually attestation is mainly to avoid the man-in-the-middle attack, Maybe the following AN gives some use case on this topic, SE05x is able to act as I2C master to connect with some sensor and attestation operation can be used to protect the data out of the sensor. Please kindly refer to https://www.nxp.com.cn/docs/en/white-paper/SE050-USE-CASE-WP.pdf for more details.
Hope that makes sense,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @bboozzoo ,
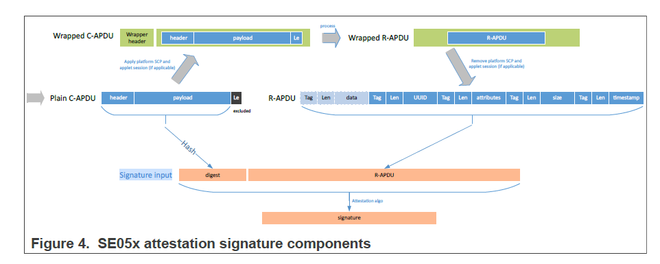
There is no need to generate all of the signature input, you may have them from the APDU command as well as the command response. if you refer to Fig 4 in the same AN, you may find as shown below:
So now you have the signature input as well as the signature which is also a part of the response if the secure object's policy allows attestation, then you may verify them on the host with the public key from the attestation secure object , for example, https://cryptobook.nakov.com/digital-signatures/ecdsa-sign-verify-examples
Hope that helps,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thanks. I get that. The problem I have is with practical aspects of implementation and I'm really wondering how folks use that in the field.
In a case when a remote system needs to verify that some data provided by the device really comes from SE05x attached to that device, having the command PDU and response PDUs as inputs means that either you'd have to attach both to the message (impractical) or the remote system needs to be able to recreate both PDUs (impossible?). So, I'm not entirely sure of the attack vector this is trying prevent. Perhaps a rouge device attached to I2C pretending to be SE? Perhaps it's only useful when SE operates as I2C master, say in contactless card reader implementation?
Is there a way to to snoop the APDUs when using the MW libraries in order to collect the raw bytes of the command and response PDUs?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @bboozzoo ,
Actually attestation is mainly to avoid the man-in-the-middle attack, Maybe the following AN gives some use case on this topic, SE05x is able to act as I2C master to connect with some sensor and attestation operation can be used to protect the data out of the sensor. Please kindly refer to https://www.nxp.com.cn/docs/en/white-paper/SE050-USE-CASE-WP.pdf for more details.
Hope that makes sense,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------