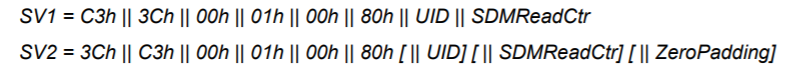- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- RFID / NFC
- :
- NFC
- :
- Re: How to verify the CMAC myself?
How to verify the CMAC myself?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to verify the CMAC myself?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Intro/Goal:
Hi, my name is Manuel and I am software engineer. Recently I bought some of your NTAG 424 DNA, that I want to use for a product authenticity solution.
Documents/Material:
I read through some documents but mainly the following two:
https://www.nxp.com/docs/en/data-sheet/NT4H2421Gx.pdf
https://www.nxp.com/docs/en/application-note/AN12196.pdf
Hardware:
I bought a Identiv u Trust 3700 F CL reader that is connected to my MacBook Pro and i am running the NXP TagXplorer.
Configuration:
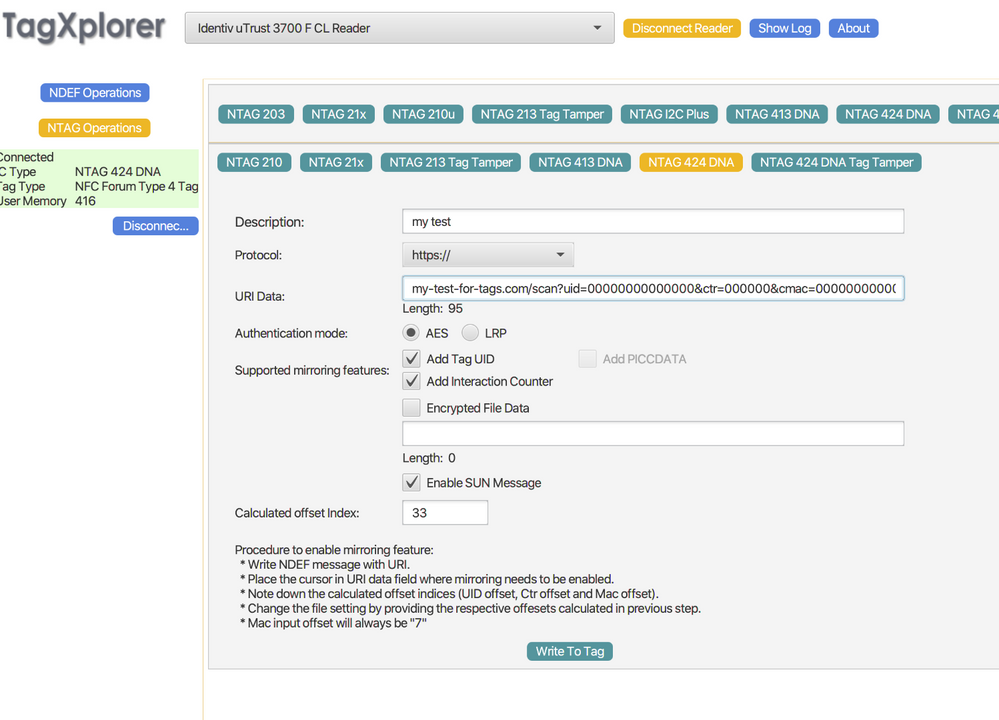
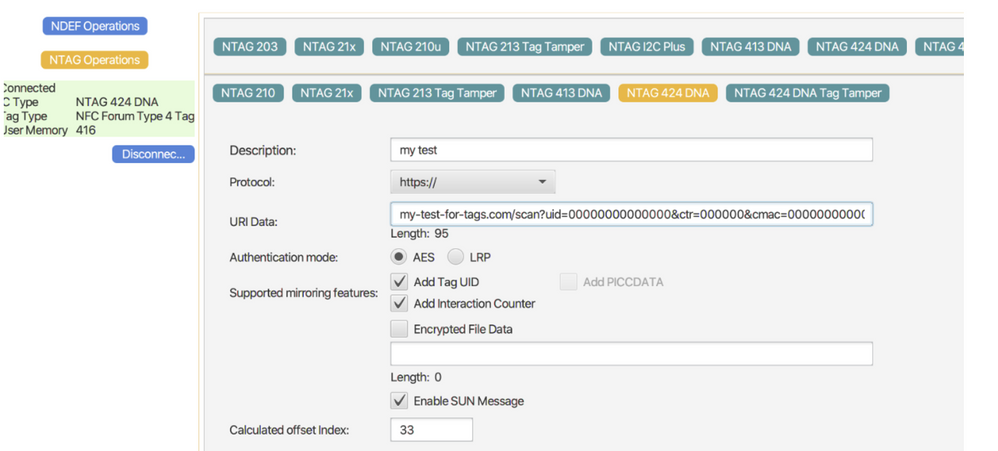
Using this as an example URL, where I have 3 custom params at the end, "n", "t", "p":
my-test-for-tags.com/scan?uid=00000000000000&ctr=000000&cmac=0000000000000000&n=2&t=1&p=3
I activated "ADD TAG UID", "ADD INTERACTION COUNTER" and "ENABLE SUN MESSAGE". I also set the calculated offset Index at 33 which is right after the questionmark in the URL (i hope this is correct?!)
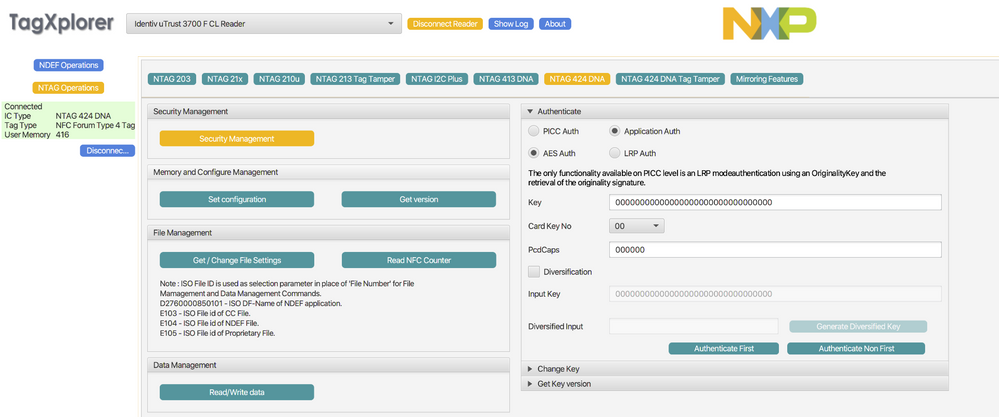
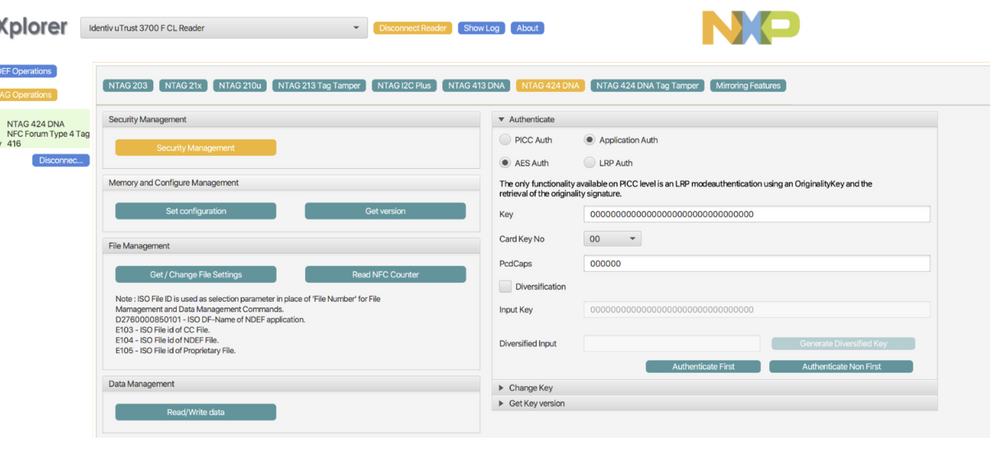
after writing this information to the tag i am going to NTAG 424 DNA Secruity settings where i hit "Authenticate First"
(for this first try i dont want to change any of the default keys on the chip, that would be my next step once i get this simple example working)
After being successfully authenticated
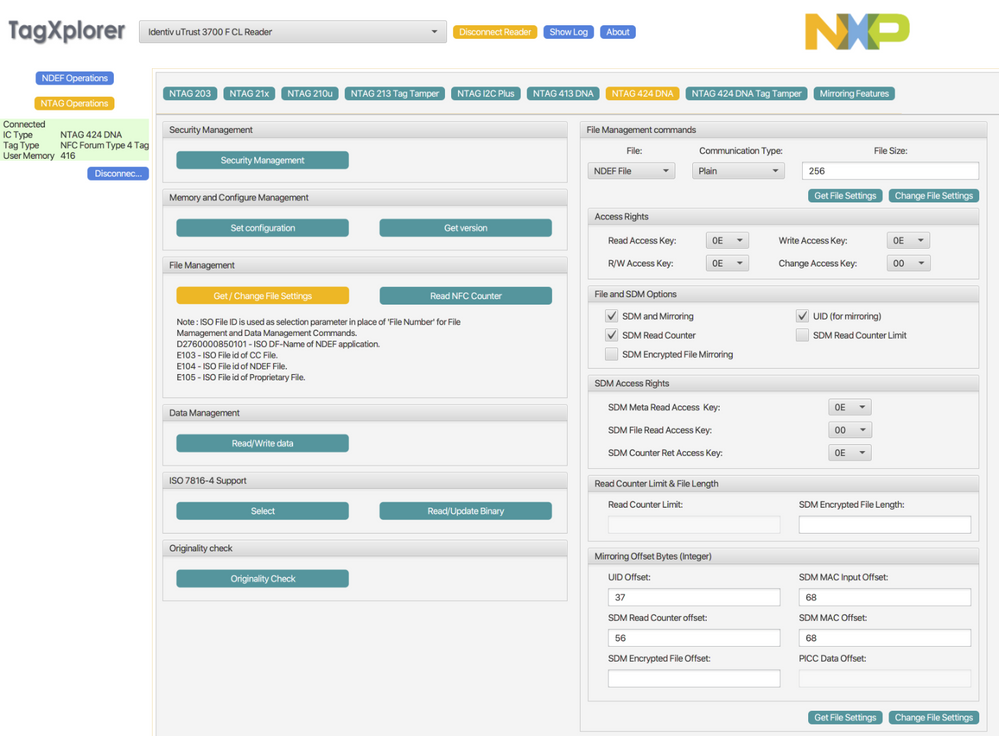
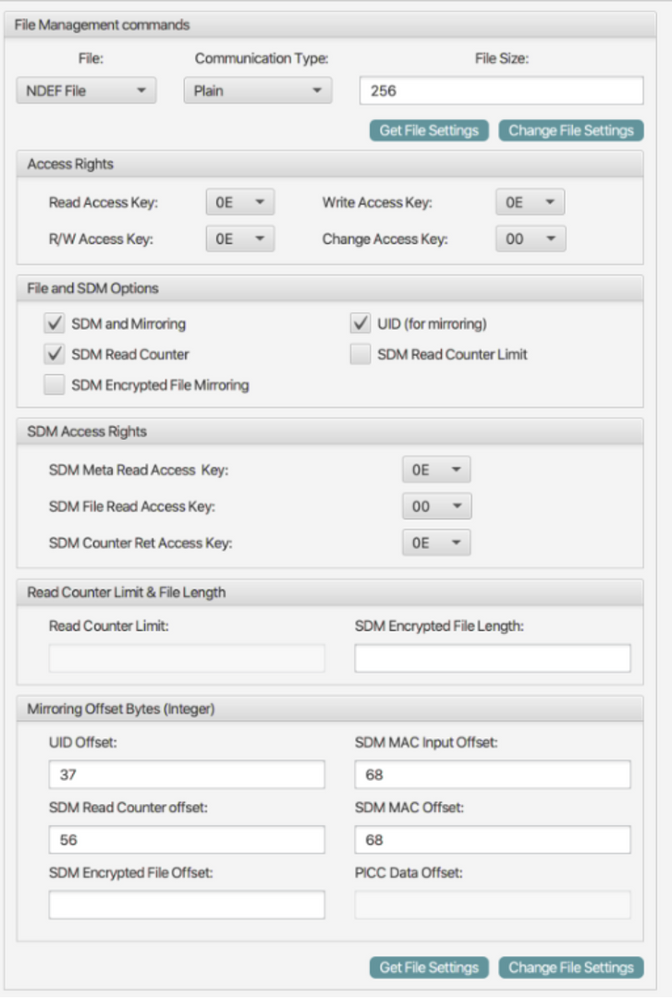
I am going to the "File Management" options and set the following data:
Problem:
When i go now to NDEF Operations and click on READ NDEF button, it will give me for example this URI here:
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000021&cmac=3E12626CBBFB3FB9&n=002&t=1&p=3
if i click the Read from Tag button again it gives me:
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000022&cmac=211167FD30F03BEA&n=002&t=1&p=3
which gives me the same uid, but an incremented counter and a new cmac which i guess is correct.
This data is now being sent to the backend, but how can i now recalculate the cmac(3E12626CBBFB3FB9) given in the URI from the two params uid(044B6A4A4E6880) and ctr(000021) in my backend?
I guess I also need to know the key that was used to encrypt it also on the backend, correct?
I guess in this default case the key is just 16bits of zero like this 0000000000000000, correct?
But how exactly would this calculation now work? I cant figure it out with the two documents above.
Can you please give me a step by step example for this cmac calculation on my backend with my values given here?
Thanks for your help in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The CMAC calculation algorithm shall be implemented manually if not included in a library you are using. Fortunately, it is perfectly explained in following app note, chapter 4.4.4.2: https://www.nxp.com/docs/en/application-note/AN12196.pdf
Hope it helps!
BR,
Ivan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Ivan!
Thanks for your reply, but I already looked at the example from chapter 4.4.4.2 here (https://www.nxp.com/docs/en/application-note/AN12196.pdf )
4.4.4.2 shows the following Java Method:
calculateMFCMAC(byte[] key, byte[] valueToMAC)
1)
which values from the example do i have to use for "key" and for "valueToMAC" to receive the value 94EED9EE65337086 for the CMAC?
2)
and which values would i have to use from my example up there to receive the value 3E12626CBBFB3FB9 for the cmac?
I am really having a hard time here getting this to work :smileysad:
Best,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Do not worry, it is a bit confusing at a first glance, but it is more understandable if you refer to the flow followed in table 5, and referring to the SUN mapping format example of chapter: 4.4.4.1.
BR,
Ivan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI, Ivan!
Sorry, still no change to get it running - tried everything by now.
Given table 5 which two values do i use from table 5 and feed to byte[] key and the byte[] valueToMac parameters for the function calculateMFCMAC below?
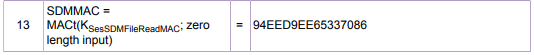
I assume this calculateMFCMAC should return me the SDMMAC? so should give me the value 94EED9EE65337086 ?
I am really having a very hard time working with this NFC-tags...
Is there maybe some chat here, where i can directly communicate with someone of the NXP technicians?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Manuel Mertl,
Hope you are doing great, I believe the issue you are having is with the "Zero length input" Mac, for this I believe there is a pseudo code in the AN mentioned before, please check the following:
this step
translates to the following.
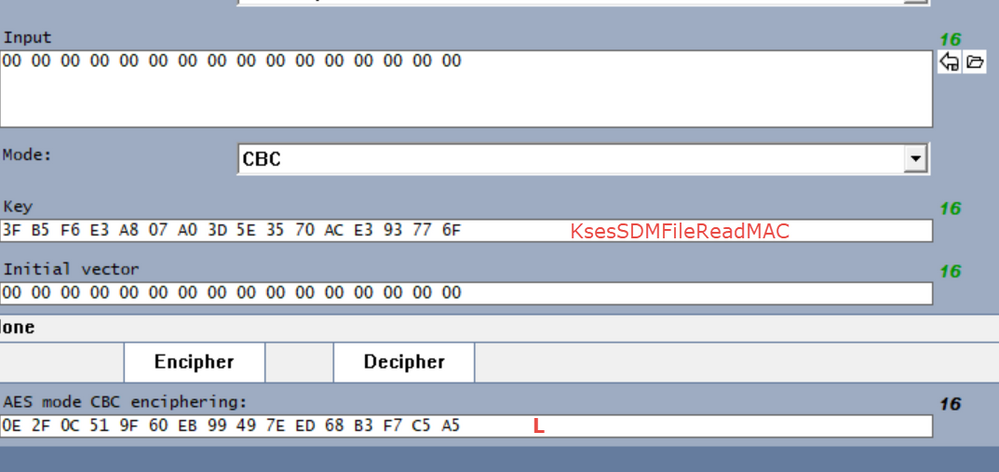
in this case you first need to calculate the mac on only 00's. so first you are going to do the following:
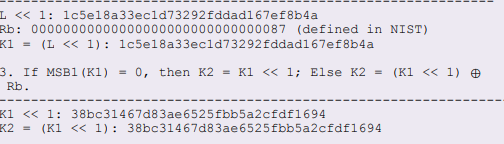
once you have this value you need to get the K1 and K2 values:
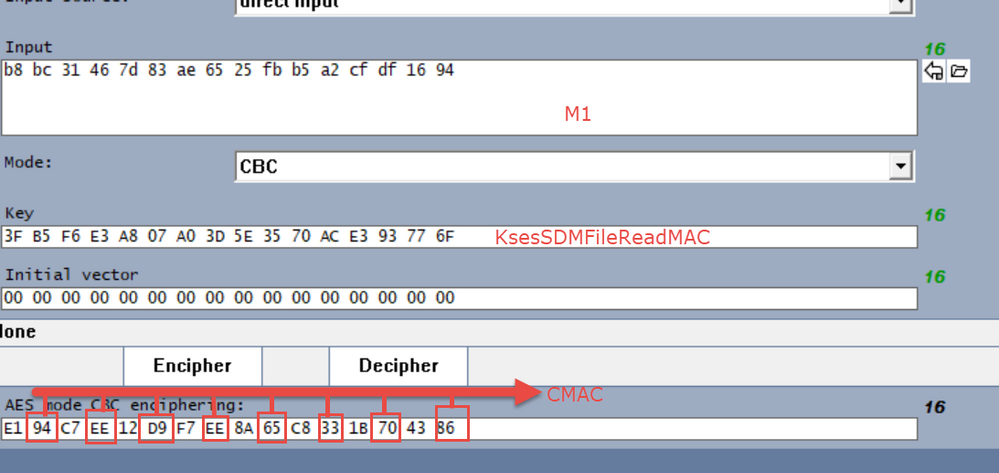
this are going to be used in the next step which is getting the M1 Value,
then you are going to calculate the MAC I used AES CBC 128,
Hope this is better, and help you understand this process, some calculators and software for this support the zero length input Mac so you only need to set some flag or just send the mac in 00s and they do it but it all depends on the sw used.
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @manuel_mertl @Jonathan_Iglesias @IvanRuiz
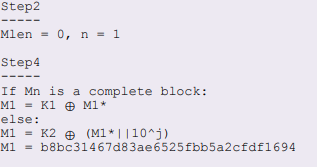
I am following this guide and i have coded all the parts correctly except for the bit where you calculate m1 value.
I am using the url in the example above so i can verify that the values are correct at each step.
in my server code (i am using nodejs) I have calculated so far that
K2 = 38bc31467d83ae6525fbb5a2cfdf1694
Then in the docs it says
If Mn is a complete block:
M1 = K1 ⊕ M1*
else:
M1 = K2 ⊕ (M1*||10^j)
_________________
Therefore
M1 = b8bc31467d83ae6525fbb5a2cfdf1694
I can see that the 3 from K2 has been replaced with a b in M1, but i dont understand where the b has come from.
before this step i am able to calculate all values correctly. and if i hard code the swap for the 3 to b, then it continues to calculate the final CMAC value correctly. however, the hard code only works for this example of course, when i use a real tag (with a default private key of all 0) and the uid/ctr values are different, it doesnt work anymore, which is expected.
Please could you explain the M1 calculcation step?
Thanks
Aamir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Jonathan!
Still having troubles getting the correct output.
Please see my post above.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Manuel Mertl,
Hope you are doing great, as we discussed in our private messages please check this :
in the application note you can check 4.4.4.2 this should work for you let me explain how, there are different ways to do the SUN I will show the first two figures showed in AN.
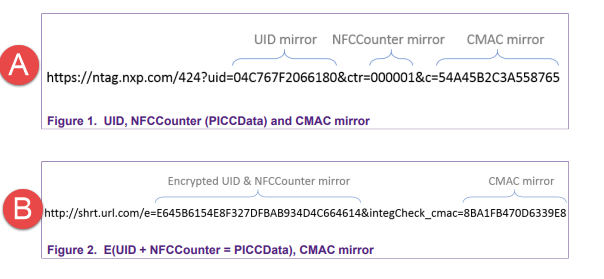
A.- is the way you are working
B.- is explained in the 4.4.4.2 example.
in this case the UID and CTR are encrypted and sent as "e" Variable.
since you are sending the information in plain you can skip some steps of table 5.
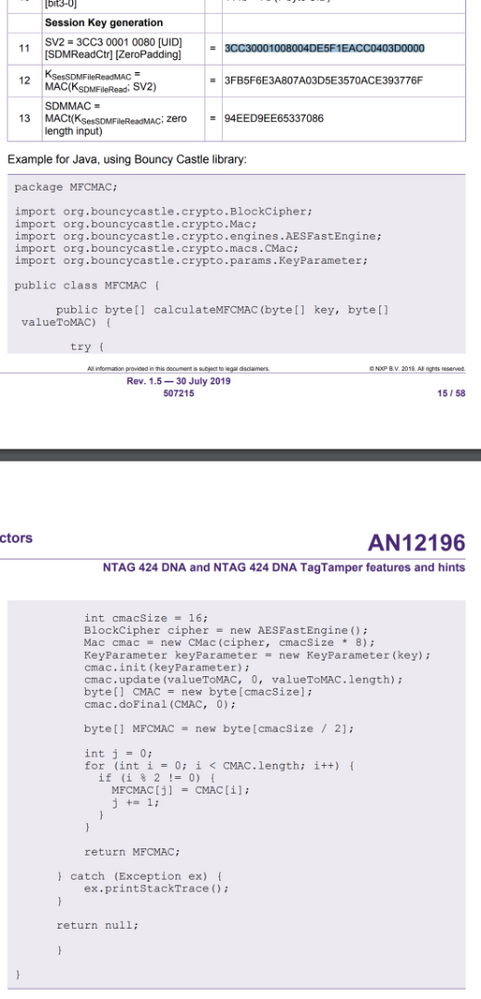
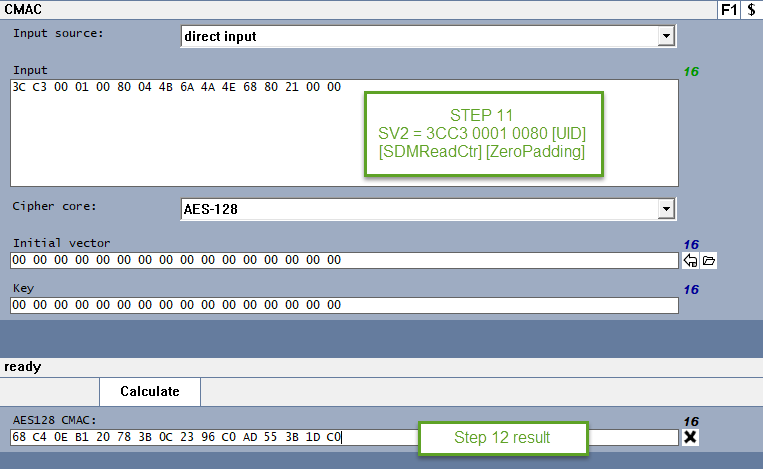
so basically you can go directly into step 11 because the previous steps Decrypt the information and get the UID, CTR, etc. in this case you already have that data because is in plain, so first you will do the SV2, as explained in step 11
the you will need to create the session key for MACing like in step 12
which translates to this
then you will proceed to do the step 13
which I explained in the previous post.
please let me know if this is clear to you or if you have any questions.
Have a nice day !
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer, but i have some follow up questions to that:
1) is the start of the SV2 value always: 3CC3 0001 0080 no matter what UID and Counter etc. i use? (so can i hard code this part?)
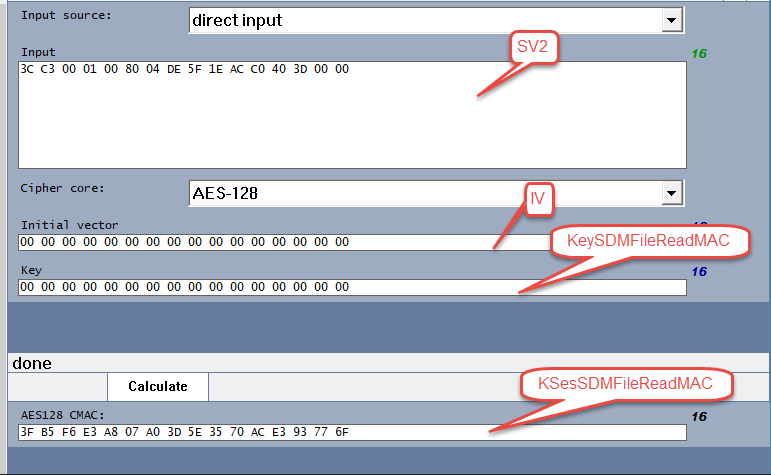
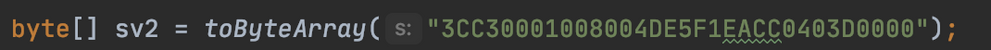
2) When calculating the KsesSdmFileReadMAC ... is this using the calculateMFMAC Java Function?
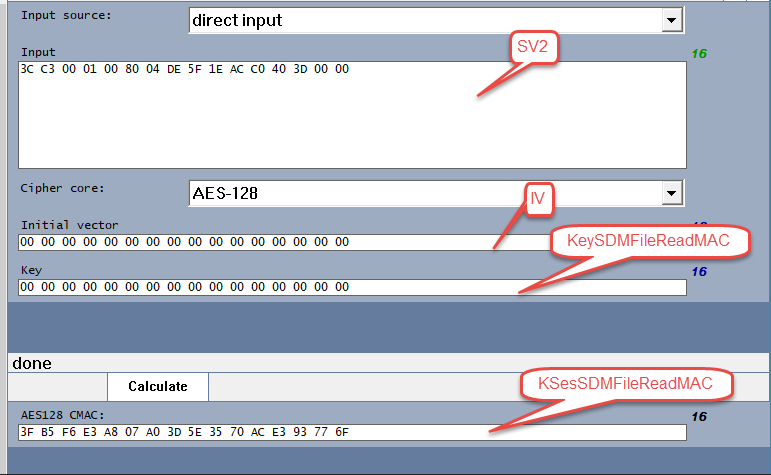
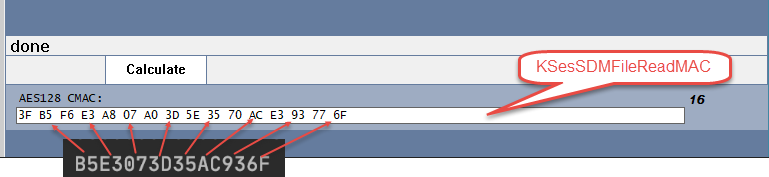
If so then the key-paramter would be 00000000000000000000000000000000 and the valueToMac-paramter would be 3CC30001008004DE5F1EACC0403D0000 ?
I tried it like this, but it gives me a different value:
I get B5E3073D35AC936F instead of 3FB5F6E3A807A03D5E3570ACE393776F
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Manuel Mertl,
for your first question, the basic answer is yes, this is defined in the DS section 9.3.9.1
this is the previous step to session keys calculation, the SV1 is used for the session encryption and the SV2 is used for session MACing, this is not the MAC this is used to generate the key to MAC data during a session. for example next time a customer taps on the tag the SV will change due to the ctr changes, so each tap will generate a different key therefore a different key for encryption and MAC.
for your second question the calculation should be correct, as you can see in my procedure for step 12 I see your calculations are correct,
as you can see here you split the key into odd bytes, the odd bytes are correct so the entire key should be correct, please dont do this here:
that is done at the end of step 13, not here, because you need the 16 bytes here for the step 13 calculations as you can see the values on step 12 are used as key on step 13. then the result of 13 is split into odd bytes to have 8 bytes of data.
Hope I am being clear here if you still have questions let me know. I would highly recommend checking the process on the DS and AN.
Hope you are doing great.
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much for your explanation jonathaniglesias, we are nearly there :smileygrin:
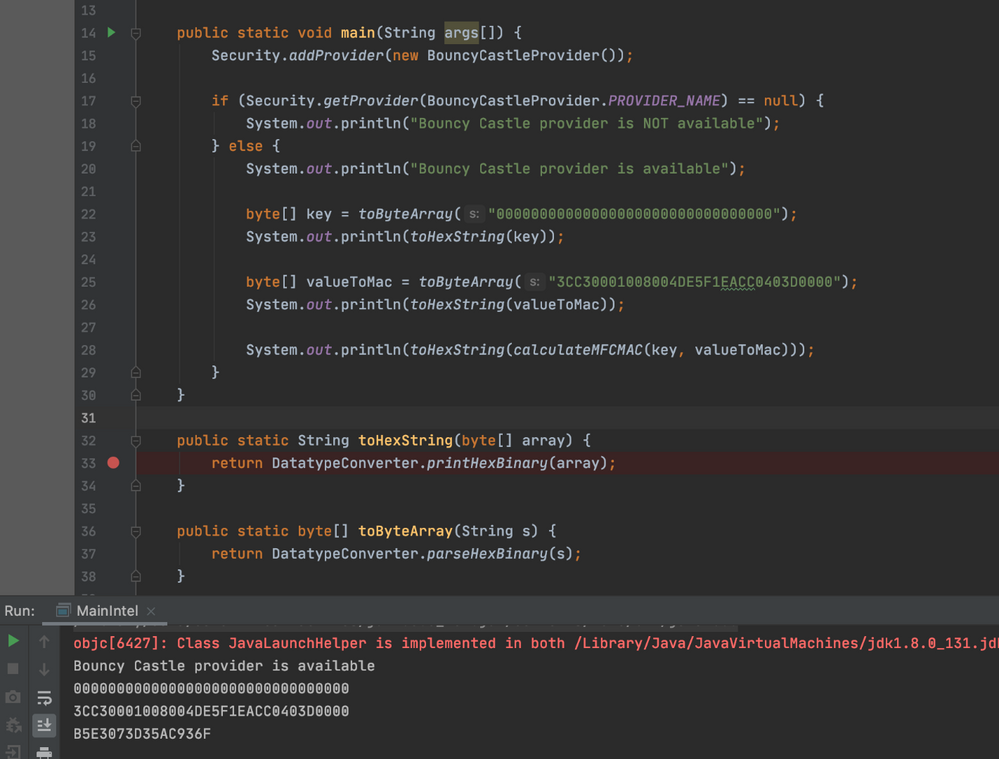
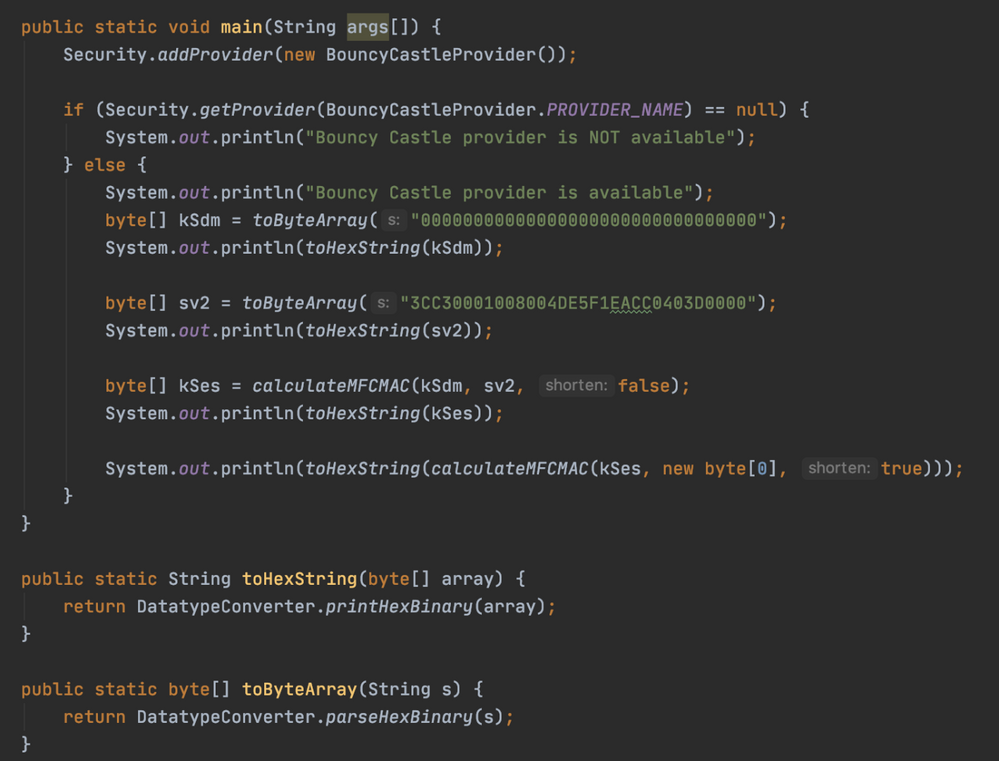
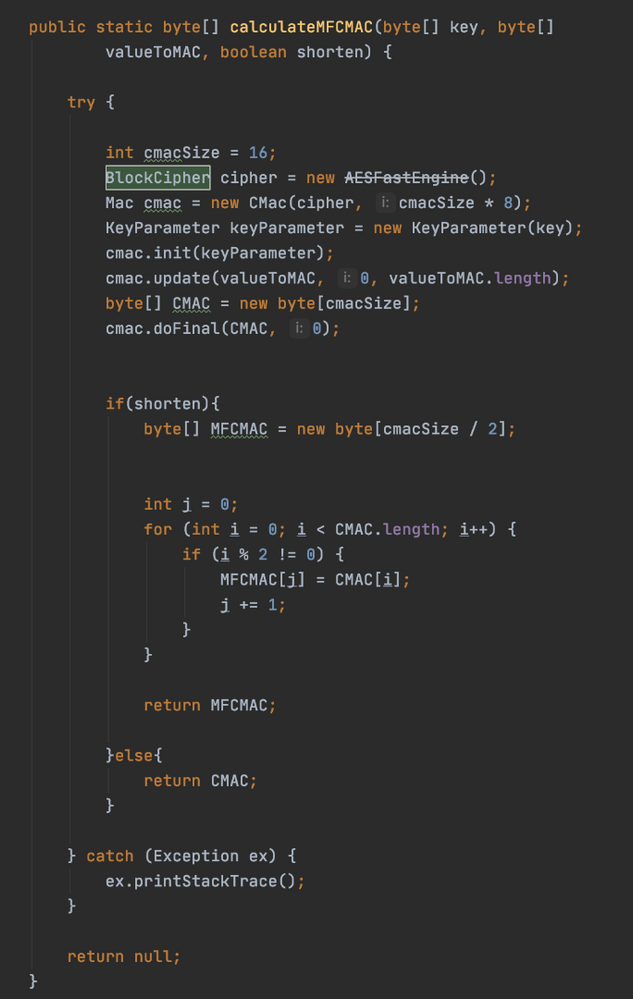
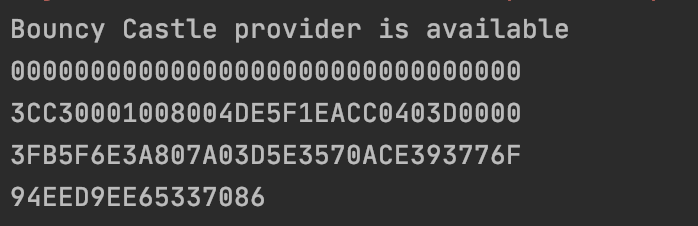
I was finally able to recalculate the values from the document using this code below (for anyone interested):
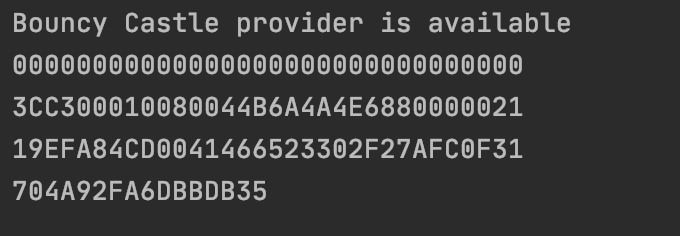
receiving the folllowing output:
-------------------------------------------------
but I tried now to change my value for SV2 according to my first post all the way up here:
so instead of using the following value from the example:
i used the uid(044B6A4A4E6880) and ctr(000021) from my example up there, leaving the other code the same:
which gave me the following result when i scanned the tag itself:
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000021&cmac=3E12626CBBFB3FB9&n=002&t=1&p=3
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000021&cmac=3E12626CBBFB3FB9&n=002&t=1&p=3
but my java app outputs the following:
so 3E12626CBBFB3FB9 != 704A92FA6DBBDB35
:smileysad:
Do you see any mistakes in my configuration screenshots from the first post? Like Offset numbers, wrong keys, etc?
Please find here again the screenshots:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well in this case specifically I do not know how to calculate this because I dont have the actual data, as you know every time you tap into your tag, there is some dynamic data that will be generated, so each tap there should be a different session key and I do not know the keys you have stored internally in the tag and please do not share them here since this is a public forum you dont want your keys posted here, the best would be that you apply this process to the tag or if you want you can do a dummy test where you do all the process with dummy data and keys but the best would be that you know your keys and apply the process that I have explained in my previous post here.
just take the ctr and UID and apply step 11, then step 12 to get the session mac key then the step 13 to get the mac, it is important that you do this with the correct keys the ones in the app note are just for demonstration.
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
for testing purposes, i have not configured any of the keys yet on the tag.
if i understood correctly everytime i tap the tag in my case only the ctr-value and the cmac-value changes, correct? (since the UID stays the same), see my URL strucutre below
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000021&cmac=3E12626CBBFB3FB9&n=002&t=1&p=3
then i am creating the SV2 value by concat: "3CC3 0001 0080" + UID + CTR
which gives me: 3CC300010080044B6A4A4E6880000021
and then i am using my code from above calling:
calculateMFCMAC(byte[] key, byte[] valueToMAC);
where the key equals the 32 zeros and the valueToMac equals my SV2 as byte arrays
so if the default key on the tag is 32-zeros then it should work, correct? ( -> but it doesnt)
maybe you can see some of my configuration problem in the above screenshots?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Manuel,
Hope you are doing great, well I think the problem is you are using the CTR in the wrong way I just followed your data like this
After Step 13 I get :
683e8e12a962a26c5ebb0afb343f90b9
68 3e 8e 12 a9 62 a2 6c 5e bb 0a fb 34 3f 90 b9
cmac = 3e 12 62 6c bb fb 3f b9
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000021&cmac=3E12626CBBFB3FB9&n=002&t=1&p=3
Which is equal to your calculation.
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, jonathaniglesias
I think I see now where my mistake is:
My uid is 044B6A4A4E6880 and my ctr is 000021
Then i am creating the SV2 value by concat: "3CC3 0001 0080" + UID + CTR
Which gives me: 3CC300010080044B6A4A4E6880000021
but instead of using this value, your value looks like this:
3CC300010080044B6A4A4E6880210000
so you remove the leading zeros and add them at the end.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
:smileygrin: let us know here in the community if in the future you have more questions.
Have a nice day !!
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
will do.
Thank you once again jonathaniglesias for your help :smileyhappy:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Jonathan!
Thanks for your detailed answer.
What i would need is a step by step calculations manual how i get from this URL:
https://my-test-for-tags.com/scan?uid=044B6A4A4E6880&ctr=000021&cmac=3E12626CBBFB3FB9&n=002&t=1&p=3
by using 044B6A4A4E6880 (as uid) and 000021 (as ctr) to cmac(3E12626CBBFB3FB9)
The PDFs show examples with PICC_data
what are the operations that i have to do, and in which order to get to 3E12626CBBFB3FB9 with 044B6A4A4E6880 and 000021.
I hope I explained my problem in a clear way.
I have here hundreds of 424 DNA Tags next to me that are waiting to be configured :smileywink:
Thank you :smileyhappy: