- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- Identification and Security
- i.MX Processors
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- CodeWarrior
- Wireless Connectivity
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
-
Hi,
My group is currently trying to access an MPC5777C device that we've censored. We know for sure that the JTAG password is programmed, as well as the password for PASS Group 0 and possibly Group 1, however it's my understanding that we can gain access with only one password.
The life cycle of the device is set to OEM Production.
We are using the Greenhills MULTI environment. We've successfully been able to reset and halt the device by writing to the jtag_password_hi and jtag_password_lo registers.
We can read flash memory at this point using the "memory view" window. However, when we try to download a program over the debugger, it seems to fail to read memory at all (i.e. the probe thinks a block is erased when it is actually populated).
Additionally, we're having trouble accessing the CIN0-7 registers. We've successfully written to the PASS_CHSEL register and have seen it change to acknowledge a new master, but writing the password to the CIN area has no effect.
Can someone help us better understand how to gain access to the device?
Thanks,
Jeff Campbell
P.S. We figured this out for the most part, turned out it was a matter of having every password group loaded.
The question now, though, is exactly how password words map into CIN0-7. The manual says that CIN0 matches with the MSB of the password. Does this mean, for instance, that for Group 0, CIN0 corresponds to the value at 0x00400160?
Thanks again!
已解决! 转到解答。
Hello,
I am not familiar with GHS debugging tools (only with compiler).
However there is no known issue when you unlock memory with programmed JTAG password to censored device.
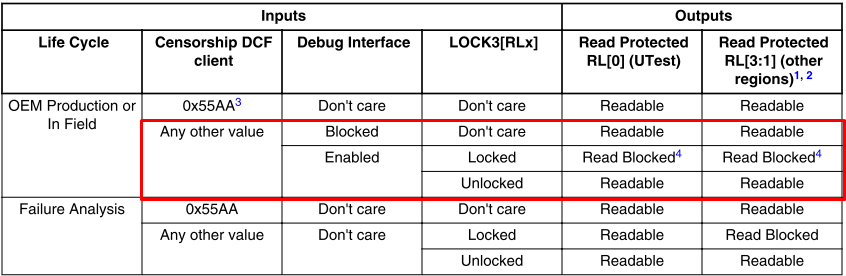
You are now in OEM production or in field life cycle with programed DCF censorship client (JTAG Password).
As you can see from above table the device is always read protected. Never only write protected. So without correct password you are not able even to read flash.
Before we can proceed further:
We can read flash memory at this point using the "memory view" window. However, when we try to download a program over the debugger, it seems to fail to read memory at all (i.e. the probe thinks a block is erased when it is actually populated).
Did you tried to use different debuggers? Like Lauterbach or PEMicro? Or just GHS probe?
Peter
Hello,
I am not familiar with GHS debugging tools (only with compiler).
However there is no known issue when you unlock memory with programmed JTAG password to censored device.
You are now in OEM production or in field life cycle with programed DCF censorship client (JTAG Password).
As you can see from above table the device is always read protected. Never only write protected. So without correct password you are not able even to read flash.
Before we can proceed further:
We can read flash memory at this point using the "memory view" window. However, when we try to download a program over the debugger, it seems to fail to read memory at all (i.e. the probe thinks a block is erased when it is actually populated).
Did you tried to use different debuggers? Like Lauterbach or PEMicro? Or just GHS probe?
Peter