- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- MCUXpresso Software and Tools
- :
- MCUXpresso Secure Provisioning Tool
- :
- Re: How to create a signed image for serial boot with MCUXpresso secure provisioning tool
How to create a signed image for serial boot with MCUXpresso secure provisioning tool
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a setup with two rt600 processors, where only one has a flash connected.
I want to boot one processor from flash and then this processor sends the image via a serial connection to the other processor.
Both images need to be Authenticated. I have managed to create an image for the first processor, whihc boots form flash, with the SPTv6.0, however I don't see how an image bootable via serial could be created with the SPT.
Is there a different tool or a document which describes how to build an image like that?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since the whole anwser to the question is split over several answers in this thread, I want to summarize it briefly.
The SPT does not support building images for serial boot. However one can select SD card as boot device and build the image this way.
Since serial boot and booting from SD card both load to image to RAM the generated image works for serial boot.
The image alone does not guarantee secure boot. The OTP configuration (respectifly their shadow register furing development) must be done correctly in order for the signature to be checked at boot.
One can use the SPT for this even though it does not support serial boot as follows:
Is there a way to use the SPT for this even though I don't write the image with the SPT?
- You have to have the workspace to be configured to "Development" life-cycle (on the toolbar). This you should already have, just for completeness.
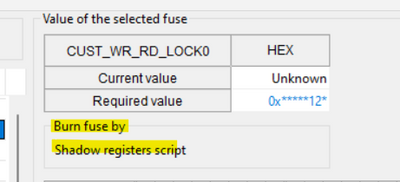
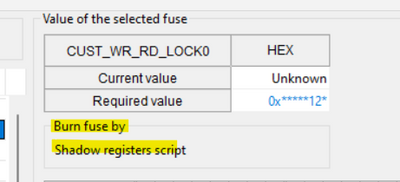
- On Build tab in the "OTP Configuration" configure the fuses. You can check if the fuse can be written into the shadow register:
- Click on the "Build" button, it is required intermediate step
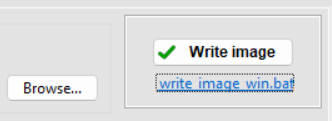
- Go to Write tab and click on the label "write_image_win.bat" (On Linux/Mac it will be *.sh).
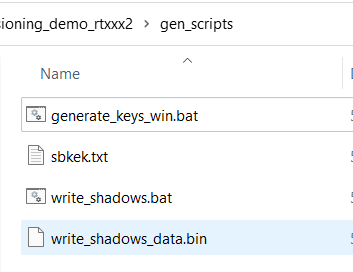
This will update all necessary files, including the write script and also the write_shadows.bat script that can be found in the gen_scripts\ folder - double check the content of the script.
In order to verify that the signature check actually works, flipping one bit in the image and tring to boot it is sufficient. If secure boot works the image is loaded over the serial interface but is not executed and the chip is locked up. To check wether the chip is really locked one can try to reupload the shadow register config. It should fail with the following error:
### Execute application, that will configure shadow registers ###
blhost -t 5000 -u 0x1FC9,0x0020 -j -- execute 0x00080159 0x00080000 0x00200000
{
"command": "execute",
"response": [],
"status": {
"description": "10006 (0x2716) Unsupported Command.",
"value": 10006
}
}
blhost failed
### RESULT of the script `Writing shadow registers`: FAILURE (return code = [2]ERROR)
Hope this saves someone else some time
Thank you Marek and Libor for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David,
it is nice to hear your application is working now. We'd be more than happy if you send a short summary, how to enable Serial Boot via MCUXpresso Secure Provisioning tool into this thread. I suppose you built the bootable image in MCUXpresso Secure Provisioning tool (image executed in internal RAM) and then you just wrote the image into RAM and jump to the image start address (?)
Thank you and have a nice day
Marek
NOTE: If you find the answer useful, kindly click on [ACCEPT AS SOLUTION] button
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Marek,
I have written a summary already. It is the marked solution.
Once you have the OTP configured and a signed image which executes from RAM, you can load that image via serial boot and the bootloader automatically verifies the signature and if the check is successfull it jumps to the startaddress specified in the image and executes.
regards,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since the whole anwser to the question is split over several answers in this thread, I want to summarize it briefly.
The SPT does not support building images for serial boot. However one can select SD card as boot device and build the image this way.
Since serial boot and booting from SD card both load to image to RAM the generated image works for serial boot.
The image alone does not guarantee secure boot. The OTP configuration (respectifly their shadow register furing development) must be done correctly in order for the signature to be checked at boot.
One can use the SPT for this even though it does not support serial boot as follows:
Is there a way to use the SPT for this even though I don't write the image with the SPT?
- You have to have the workspace to be configured to "Development" life-cycle (on the toolbar). This you should already have, just for completeness.
- On Build tab in the "OTP Configuration" configure the fuses. You can check if the fuse can be written into the shadow register:
- Click on the "Build" button, it is required intermediate step
- Go to Write tab and click on the label "write_image_win.bat" (On Linux/Mac it will be *.sh).
This will update all necessary files, including the write script and also the write_shadows.bat script that can be found in the gen_scripts\ folder - double check the content of the script.
In order to verify that the signature check actually works, flipping one bit in the image and tring to boot it is sufficient. If secure boot works the image is loaded over the serial interface but is not executed and the chip is locked up. To check wether the chip is really locked one can try to reupload the shadow register config. It should fail with the following error:
### Execute application, that will configure shadow registers ###
blhost -t 5000 -u 0x1FC9,0x0020 -j -- execute 0x00080159 0x00080000 0x00200000
{
"command": "execute",
"response": [],
"status": {
"description": "10006 (0x2716) Unsupported Command.",
"value": 10006
}
}
blhost failed
### RESULT of the script `Writing shadow registers`: FAILURE (return code = [2]ERROR)
Hope this saves someone else some time
Thank you Marek and Libor for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David,
MCUXpresso Secure Provisioning GUI tool does not support all security settings, the tool supports only most typical use cases. Unfortunately booting via serial is not supported.
I also do not have any practical experience with serial boot, but I suppose the image will be executed from RAM, so you can build the image executed from RAM (select SD card as boot device) and then use serial boot to upload the bootable image to the RAM.
You should be able to find related information in reference manual for RT6xx processor.
Marek
NOTE: If you find the answer useful, kindly click on [ACCEPT AS SOLUTION] button
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank for your answer.
selecting SD card as boot device kind of worked. I could build an image and was able to boot it via serial boot. However I think the image was not authenticated, because the OTP, respectivly the shadow register were not setup to authenticated the image.
How can I configure the shadow registers to authenticate the serial boot image? Is there a way to use the SPT for this even though I don't write the image with the SPT?
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello David,
Is there a way to use the SPT for this even though I don't write the image with the SPT?
- You have to have the workspace to be configured to "Development" life-cycle (on the toolbar). This you should already have, just for completeness.
- On Build tab in the "OTP Configuration" configure the fuses. You can check if the fuse can be written into the shadow register:
- Click on the "Build" button, it is required intermediate step
- Go to Write tab and click on the label "write_image_win.bat" (On Linux/Mac it will be *.sh).
This will update all necessary files, including the write script and also the write_shadows.bat script that can be found in the gen_scripts\ folder - double check the content of the script.
Regards,
Libor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for your answer, this is very helpful!
I was able to write the shadow registers with the generated script and it executes successfully.
I then loaded a signed image via serial boot and it booted. So far so good.
To verify that secure boot works, I then loaded a different image, signed with a different ROT key and it booted as well.
I am confused by this. I have only used a sofreset (reset button SW3 on the mimxrt685-evk) between loading the two images and it is my understanding, that the shadow registers are not cleared by this. secure boot is enabled in the OTP config, so the second image should not have booted.
Do you know where I went wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David,
I tried similar use case, I used signed image located in external flash, executed in internal RAM. I used SEC tool to build and write the image.
If I wrote the same image signed with different keys, it was rejected, the image was not started, and processor remains in ISP mode.
Looking to documentation, Fig 186. Top-level boot process, the image authentication is same for "Serial Boot" and "FlexSPI boot".
After your failure, can you try switch your processor to ISP mode using soft reset and try to upload the shadow registers again? If the processor is secured (using shadow registers), it should fail with the following error:
### Execute application, that will configure shadow registers ###
blhost -t 5000 -u 0x1FC9,0x0020 -j -- execute 0x00080159 0x00080000 0x00200000
{
"command": "execute",
"response": [],
"status": {
"description": "10006 (0x2716) Unsupported Command.",
"value": 10006
}
}
blhost failed
### RESULT of the script `Writing shadow registers`: FAILURE (return code = [2]ERROR)
Marek
NOTE: If you find the answer useful, kindly click on [ACCEPT AS SOLUTION] button
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Marek,
I have tried your suggestion and an additian step and was able to verify that secure boot actually works.
In my first approach, where two images were booted with different keys and both booted, I used ROT1 and ROT2 of the same PKI. I guess for this to work I would have had to rewoke one of the keys.
Next I tried with ROT1 of two different PKI's. The one with from the PKI were the OTP config was made booted and the other one already faild during loading the image via UART. I guess the bootloader rejected the image right away since the PKI did not match, without even checking the signature.
Then I tried again with the image with the right key and signature but I corrupted the image by flipping 1 bit in the image to verify that the signature is checked. The whole image was transfered via UART but the image did not boot.
I then tried to reupload the shadow registers like you suggested and it failed with the same value: "10006"
Thank you very much for your help!