- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
Hi,
Environment
Board: LPC55s69
SDK version: 2.12.0
SW: MCUXPresso IDE
I was trying to exploit ECDSA sign/verify functions in secure memory, so I ported "lpcxpresso55s69_mbedtls_benchmark" project in SDK 2.12.0 to my TZ project.
I found that when I use those functions in applications in secure world, it was always stuck in 'hashcrypt_sha_finalize' or 'hashcrypt_sha_process_message_data' functions, specifically in this while loop,
while (0U == (base->STATUS & HASHCRYPT_STATUS_DIGEST_MASK))
{
}The status here was set to 5 when I tried in secure world, but it was 3 when I tried in normal work, where the code worked fine.
To clarify why this happens, I changed the MEMADDR where the message was given to any non-secure RAM and it worked well, which probably means that this is not the configuration issue, but the hardware/software bug using secure RAM.
// base->MEMADDR = HASHCRYPT_MEMADDR_BASE(message);
base->MEMADDR = 0x2001bd4c;
Would anybody help me to figure this out in more detail?
Here is the original question I posted a few days before.
Thanks!
已解决! 转到解答。
Hello @mat1024
How about add code
HASHCRYPT->LOCK = HASHCRYPT->LOCK | ((0x0A75<<4) | 0x1);
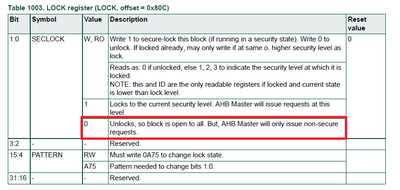
Because the HASH-AES engine is unlocked by default. That means it will issue non-secure requests as AHB master, as shown below.
So we cannot use it at secure state when it is unlocked. We must lock it at secure state if we want to use it at secure state.
BR
Alice
Hello @mat1024
How about add code
HASHCRYPT->LOCK = HASHCRYPT->LOCK | ((0x0A75<<4) | 0x1);
Because the HASH-AES engine is unlocked by default. That means it will issue non-secure requests as AHB master, as shown below.
So we cannot use it at secure state when it is unlocked. We must lock it at secure state if we want to use it at secure state.
BR
Alice
Hi @Alice_Yang ,
Thanks for your comment!
After adding code right next to resetting the peripheral in HASHCRYPT_Init() function, it works perfectly!
void HASHCRYPT_Init(HASHCRYPT_Type *base)
{
#if !(defined(FSL_SDK_DISABLE_DRIVER_CLOCK_CONTROL) && FSL_SDK_DISABLE_DRIVER_CLOCK_CONTROL)
CLOCK_EnableClock(kCLOCK_HashCrypt);
#endif /* FSL_SDK_DISABLE_DRIVER_CLOCK_CONTROL */
RESET_PeripheralReset(kHASHCRYPT_RST_SHIFT_RSTn);
// From NXP forum
HASHCRYPT->LOCK = HASHCRYPT->LOCK | ((0x0A75<<4) | 0x1);
}
Hope this snippet of code would be helpful to those who want to use cryptographic functions in a secure world.
Thanks!