- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- 汎用マイクロコントローラ
- :
- LPCマイクロコントローラ
- :
- Re: LPC55S69 Secure Boot Failing
LPC55S69 Secure Boot Failing
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello, I am trying to configure a LPC55S69-EVK to demonstrate the secure bootloader and secure update via SB2 loading and I'm not able to get anything to boot when the secure boot option is enabled (boot signed images via elftosb-gui) even when using the included example self-signed certificate and private key found in SDK_2.6.3_LPC55S69\middleware\mcu-boot\bin\Tools\workspace\keys_and_certs
I follow these steps:
1. Generate signed secure image (signed_secure.png attached)
2. Generate signed non-secure image (signed_nonsecure.png attached)
3. Program both images:
..\..\..\Tools\Programming\BLHost\blhost.exe -V -p COM14,115200 -- flash-erase-region 0x00000 0x34000 ..\..\..\Tools\Programming\BLHost\blhost.exe -V -p COM14,115200 -- flash-erase-region 0x78000 0x4000 ..\..\..\Tools\Programming\BLHost\blhost.exe -V -p COM14,115200 -- write-memory 0 hello_world_test_sec.bin ..\..\..\Tools\Programming\BLHost\blhost.exe -V -p COM14,115200 -- write-memory 0x78000 hello_world_test_nonsec.bin
4. Program configuration for puf keystore (puf_cfg.png attached)
5. Program configuration for secure bootloader (secureboot_cfg.png attached)
6. Read CFPA page (0x9DE00) and set byte @ 0x9DE18 to 0x01, write modified page back to 0x9DE00
7. Reset, connect to serial port to monitor output from secure/nonsecure simple application--no activity found, application is not booting.
If I change the secure boot configuration in elftosb-gui (Device->Security->Secure Boot) from 'Boot signed images' to 'Boot plain images' I can see the code is running from the serial port output and there is no issue. I'm not sure what I could be doing wrong but the information seems to point to there be an issue with the self-signed certificate/private key or signature--how can that be if I am using the included example self-signed cert and private key and followed the directions above?
Attempting to update via SB2 file also fails. I follow these steps:
1. Create SB2 file:
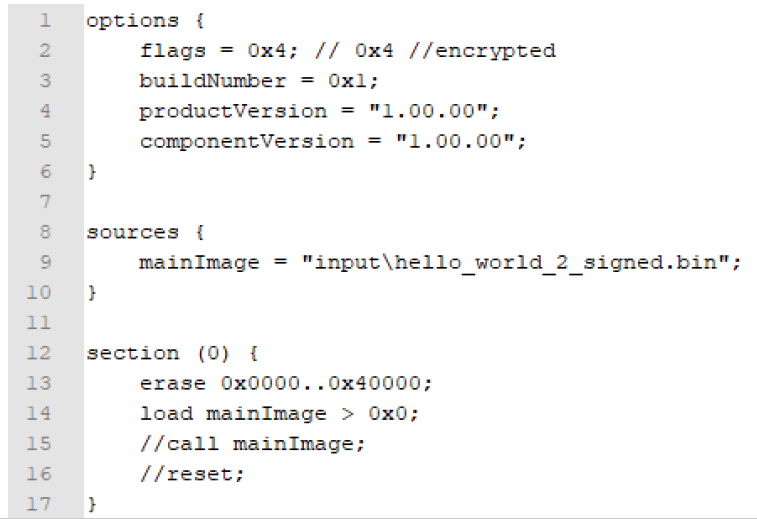
BD cfg file:
options { flags = 0x04; buildNumber = 0x01; productVersion = "1.00.00"; componentVersion = "1.00.00"; }
sources { secImage = "hello_world_test_sec.bin"; nonSecImage = "hello_world_test_nonsec.bin"; }
section (0) { erase 0x00000000..0x00034000; load secImage > 0x00000000; erase 0x78000..0x88000; load nonSecImage > 0x78000; }
SB2 generation:
@echo off set SB_KEK="D:\ENCRYPTION\BIO\SECURE_BOOT\SBK.txt" set SB_CFG=hello_world_test_cfg_sb2.bd set SB_OUT=hello_world_test_sb2.sb2 @echo on ..\..\..\Tools\Programming\elftosb_gui\elftosb\win\elftosb.exe -V -f lpc55xx -k %SB_KEK% -c %SB_CFG% -o %SB_OUT%
2. Load SB2 file:
..\..\..\Tools\Programming\BLHost\blhost.exe -V -p COM14,115200 -- receive-sb-file hello_world_test_sb2.sb2
3. Error result:
Ping responded in 1 attempt(s) Framing protocol version = 0x50010300, options = 0x0 Inject command 'receive-sb-file' Preparing to send 218848 (0x356e0) bytes to the target. Successful response to command 'get-property(max-packet-size)' Successful generic response to command 'receive-sb-file' Data phase write aborted by status 0x2712 kStatus_AbortDataPhase Possible JUMP or RESET command received. - took 0.290 seconds Response status = 10101 (0x2775) kStatusRomLdrSignature Wrote 0 of 218848 bytes.
Please let me know if I can provide any more information to help diagnose this issue. Thank you
解決済! 解決策の投稿を見る。
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Derek,
thanks for your reply.
In previous post I had .bd file content for SB2.0, right now below is .bd for SB2.1.
There is additional option secureBinaryVersion. Please test updated .bd file with this option.
Secure_FW_version and NS_FW_version checker is new functionality. It will be available from elftosb version 5.1.16 and higher. It is not released yet in SDK2.7.0 for LPC55S69. Example usage of this functionality is below in .bd file. You will be able to check version and SB file will process only when checker will return true (version_check sec 0x2 >= Secure_FW_version)
Example of use (Encrypted + Signed SB):
1 root key
elftosb.exe -f lpc55xx -k "sbkek.txt" -c "commandFile.bd" -o "output.sb2" -s selfsign_privatekey_rsa2048.pem" -S "selfsign_v3.der.crt" -R "selfsign_v3.der.crt" -h "RKTH.bin" "input.bin"
4 root keys
elftosb.exe -f lpc55xx -k "sbkek.txt" -c "commandFile.bd" -o "output.sb2" -s private_key_1_2048.pem -S certificate_1_2048.der.crt -R certificate_1_2048.der.crt -R certificate_2_2048.der.crt -R certificate_3_2048.der.crt -R certificate_4_2048.der.crt -h "RHKT.bin" "input.bin"
SB2.1 .bd file content
options {
flags = 0x8; // 0x8 encrypted + signed, 0x4 encrypted
buildNumber = 0x1;
productVersion = "1.00.00";
componentVersion = "1.00.00";
secureBinaryVersion = "2.1";
}
sources {
inputFile = extern(0);
}
section (0) {
version_check sec 0x2;
version_check nsec 2;
erase 0x0..0x40000;
load inputFile > 0x0;
}I hope this can help your issue.
Regards,
Tomas
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Derek,
Could you please confirm if Tomas's answer helps?
Have a nice day!
Regards
Soledad
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Derek,
I tested attached certificates in SDK and all works. Hopefully I found your issues.
1) Issue with secure boot
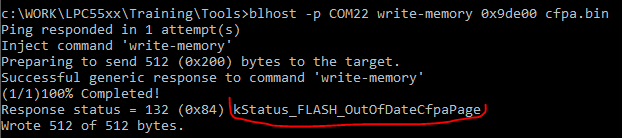
I expect your issue for secure bootloader is due to incorect CFPA page modification.
"6. Read CFPA page (0x9DE00) and set byte @ 0x9DE18 to 0x01, write modified page back to 0x9DE00"
I tested your modification and ROM will not accept this CFPA page. (see screen below)
CFPA page has at offset 0x4 Version register. Each time when you load new CFPA page Version has to be incremented for loading new CFPA page.
2) SB file issue
I expect that you are using 1B silicon. The 0A version of the LPC55S6xx silicon supports version 2.0 and the 1B version of the LPC55S6xx supports version 2.1 of the SB image format. SB 2.0 is encrypted and SB2.1 is encrypted + signed.
As you posted you are generating SB2.0 which is not valid for 1B silicon.
@echo off
set SB_KEK="D:\ENCRYPTION\BIO\SECURE_BOOT\SBK.txt"
set SB_CFG=hello_world_test_cfg_sb2.bd
set SB_OUT=hello_world_test_sb2.sb2
@echo on
..\..\..\Tools\Programming\elftosb_gui\elftosb\win\elftosb.exe -V -f lpc55xx -k %SB_KEK% -c %SB_CFG% -o %SB_OUT%Example of use (Encrypted + Signed SB):
1 root key
elftosb.exe -f lpc55xx -k "sbkek.txt" -c "commandFile.bd" -o "output.sb2" -s selfsign_privatekey_rsa2048.pem" -S "selfsign_v3.der.crt" -R "selfsign_v3.der.crt" -h "RKTH.bin" "input.bin"4 root keys
elftosb.exe -f lpc55xx -k "sbkek.txt" -c "commandFile.bd" -o "output.sb2" -s private_key_1_2048.pem -S certificate_1_2048.der.crt -R certificate_1_2048.der.crt -R certificate_2_2048.der.crt -R certificate_3_2048.der.crt -R certificate_4_2048.der.crt -h "RHKT.bin" "input.bin".bd file content
options {
flags = 0x8; // 0x8 encrypted + signed, 0x4 encrypted
buildNumber = 0x1;
productVersion = "1.00.00";
componentVersion = "1.00.00";
}
sources {
inputFile = extern(0);
}
section (0) {
erase 0x0..0x40000;
load inputFile > 0x0;
}where
-f = family lpc55xx
-k = path to KEK file (SBKEK)
-c = path to command file to be processed
-o = path to output file
-s = path to private key of certificate used for signing
-S = path(s) to certificates in certificate chain, each certificate in chain must be specified with new -S switch in order of how was chain created (root certificate first)
-R = path(s) to root certificate(s), 1-4 root certificates can be specified, each root certificate must be specified with new -R switch, one of the root certificates must be first certificate specified by -S switch
-h = path and name of output binary file generated by elftosb, which contain hash of hashes of all root certificates (RKTH), which must be uploaded to the device register
I hope this can help your issue.
Regards,
Tomas
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Tomas,
Sorry for getting back to you so late, I wasn't able to work on this again until today. Yes I am using rev 1B chips and I did try the changes you suggested but I am still getting a failure to boot and SB2 loading failure:
Ping responded in 1 attempt(s) Framing protocol version = 0x50010300, options = 0x0 Inject command 'receive-sb-file' Preparing to send 153888 (0x25920) bytes to the target. Successful response to command 'get-property(max-packet-size)' Successful generic response to command 'receive-sb-file' (1/1) 0%Data phase write aborted by status 0x2712 kStatus_AbortDataPhase Possible JUMP or RESET command received. - took 0.374 seconds Response status = 10101 (0x2775) kStatusRomLdrSignature Wrote 1024 of 153888 bytes.
The only difference I am seeing between your steps and mine is the addition of TrustZone support in my setup. Is it possible for the above error to occur with an improper TrustZone setting in the elftosb-gui tool? I have TZ-M mode set to 'From image header' as seen in the secureboot_cfg.PNG attachment and TZM is enabled for the secure image and disabled for the nonsecure image.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I did also notice this in the user manual regarding the CFPA page in section 7.3.2.1.2:
Secure_FW_version: Used during SB2 file loading. The value written in this configuration word must be always lower or equal to secure FW version specified in elftosb .bd file used for creating SB2 file. Otherwise the SB file load will be rejected. NS_FW_version: Used during SB2 file loading. The value written in this configuration word must be always lower or equal to non-secure FW version specified in elftosb .bd file used for creating SB2 file. Otherwise the SB file load will be rejected.
I don't see secure FW version or NS FW version mentioned in the elftosb manual at all. Could this be what I am missing? I did not encounter any errors in programming the CFPA page to enable the ROTK.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Derek,
thanks for your reply.
In previous post I had .bd file content for SB2.0, right now below is .bd for SB2.1.
There is additional option secureBinaryVersion. Please test updated .bd file with this option.
Secure_FW_version and NS_FW_version checker is new functionality. It will be available from elftosb version 5.1.16 and higher. It is not released yet in SDK2.7.0 for LPC55S69. Example usage of this functionality is below in .bd file. You will be able to check version and SB file will process only when checker will return true (version_check sec 0x2 >= Secure_FW_version)
Example of use (Encrypted + Signed SB):
1 root key
elftosb.exe -f lpc55xx -k "sbkek.txt" -c "commandFile.bd" -o "output.sb2" -s selfsign_privatekey_rsa2048.pem" -S "selfsign_v3.der.crt" -R "selfsign_v3.der.crt" -h "RKTH.bin" "input.bin"
4 root keys
elftosb.exe -f lpc55xx -k "sbkek.txt" -c "commandFile.bd" -o "output.sb2" -s private_key_1_2048.pem -S certificate_1_2048.der.crt -R certificate_1_2048.der.crt -R certificate_2_2048.der.crt -R certificate_3_2048.der.crt -R certificate_4_2048.der.crt -h "RHKT.bin" "input.bin"
SB2.1 .bd file content
options {
flags = 0x8; // 0x8 encrypted + signed, 0x4 encrypted
buildNumber = 0x1;
productVersion = "1.00.00";
componentVersion = "1.00.00";
secureBinaryVersion = "2.1";
}
sources {
inputFile = extern(0);
}
section (0) {
version_check sec 0x2;
version_check nsec 2;
erase 0x0..0x40000;
load inputFile > 0x0;
}I hope this can help your issue.
Regards,
Tomas
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Tomas,
Adding the following line to the BD config file fixed everything for me:
secureBinaryVersion = "2.1";
The two lines below were not recognized and resulted in errors from elftosb so I removed them from the config:
version_check sec 0x2;
version_check nsec 2;
Thanks for your help in resolving this.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
I suggest you check the following application note, this appnote describes the various types of non-secure and secure boot options.
https://www.nxp.com/docs/en/application-note/AN12283.pdf
I hope this helps,
have a nice day
Regards
Soledad
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi soledad, I have been following the Secure Boot documentation to the letter to create this example. The application note has been the starting point to get to where I created this example. Can you share what information I may have missed or am not following from the application note? Thank you
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
SB2 file issymetrically encrypted. For decryption of the file, the key has to be loaded into device. The key size for
SB2 file is 256 bits. During boot, the SB key is used with AES to decrypt the SB2 file. The SB key input for
ELFTOSB GUI is .txt file with plain text key. This key is loaded into PUF key store of LPC55Sxx.
SB2 file creation
Run elftosb command line tool with arguments below:
elftosb.exe -V -f lpc55xx -k "keys\sbkek.txt" -c "commandFile.bd" -o "output.sb2"
•-k <path to SB key for encryption(.txt)>
•-c <path to SB file config(.bd)>
•-o <path to output file(.sb2)>
SB file config file contains configuration commands that will be processed after SB2 file is loaded in the device.
In part sources is our new signed image.
The SB2 file created with the updated binary image can be loaded into the device through ISP command handler
with command receive sb file:
blhost -p COMxx receive-sb-file <path to the secured binary(.sb2)>
After successfully loading the SB2 file it is executed as configured in SB configuration file (.bd file).
When the file is executed, the internal flash address from 0x0 to 0x40000 is erased.
After flash erase operation, the image mentioned in the mainImage parameter is loaded to address 0x0.
Reset the device after these operations:
Press reset pin or run BLHOST tool blhost -p COMxx reset
The updated image loaded into internal flash starts to execute.
I hope this helps,
have a nice day
Regards
Soledad
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Soledad,
I'm not sure if I'm missing anything but did you see the step #4 I listed in my original post where I state I program the PUF keystore (with SBKEK) and the creation of the SB2 file below that?
The attachment puf_cfg.png shows where I load the PUF keystore with the SBKEK 256bit AES key in plain text. I followed the example to create the key in the Secure Boot application note.
I then use that same key for the creation of the SB2 file below in my original post. I am posting it here again in case you missed it:
1. Create SB2 file:
BD cfg file:
options { flags = 0x04; buildNumber = 0x01; productVersion = "1.00.00"; componentVersion = "1.00.00"; }
sources { secImage = "hello_world_test_sec.bin"; nonSecImage = "hello_world_test_nonsec.bin"; }
section (0) { erase 0x00000000..0x00034000; load secImage > 0x00000000; erase 0x78000..0x88000; load nonSecImage > 0x78000; }
SB2 generation:
@echo off set SB_KEK="D:\ENCRYPTION\BIO\SECURE_BOOT\SBK.txt" set SB_CFG=hello_world_test_cfg_sb2.bd set SB_OUT=hello_world_test_sb2.sb2 @echo on ..\..\..\Tools\Programming\elftosb_gui\elftosb\win\elftosb.exe -V -f lpc55xx -k %SB_KEK% -c %SB_CFG% -o %SB_OUT%
2. Load SB2 file:
..\..\..\Tools\Programming\BLHost\blhost.exe -V -p COM14,115200 -- receive-sb-file hello_world_test_sb2.sb2
Maybe I am missing something from your reply but I don't see how I did not follow the steps you copied from the Secure Boot application note. Can you share where in my list of steps the problem could be? To me, it looks correct.