- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- i.MX Forums
- :
- i.MX RT Crossover MCUs
- :
- Re: Firmware update with iMXRT1021 + BEE encryption
Firmware update with iMXRT1021 + BEE encryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
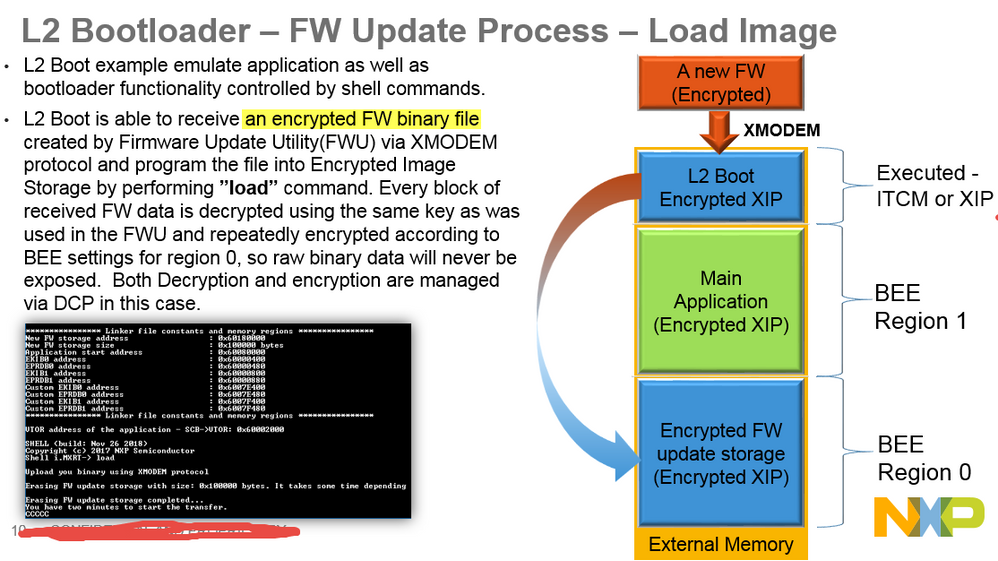
Firmware update with iMXRT1021 + BEE encryption
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry,
We have our 1021 product running in encrypted mode using BEE.
That is, BEE_KEY0_SEL, EncryptedXIP and SRK fuses all active.
Using an ethernet port, the image will be updated, writing to an inactive (but part of encrypted region) bank in flash. After a power cycle the new image will be executed.
What is the recommended process for updating the firmware to maintain the BEE encryption?
Can the BEE be used to encrypt a plain image+csf as it is written to flash?
Or does the image have to be encrypted+csf, then downloaded and written to flash without the BEE?
There won't be any type of proprietary flashloader, just whatever methods are needed for receiving blocks of data and writing to the required areas of flash.
br,
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tony Thurgood,
I am very glad to hear your RT1021 product running in encrypted mode using BEE.
What's the key you are using now? Master key or the user key?
From the flashloader process, before download the image to the flash, the image should already be secured, not the plain image+csf, then secure it when download the code.
Anyway, I will double check it on my side.
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI kerryzhou
I am using "Fixed Otpmk Key".
This is not about the flashloader, just updating firmware on a product that is running in encrypted mode, similar to "over-the-air", but we are using ethernet lan.
What is the recommended process for updating the firmware to maintain the BEE encryption?
Can the BEE be used to encrypt a plain image+csf as it is written to flash?
Or does the image have to be encrypted+csf, then downloaded and written to flash without the BEE?
br,
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tony Thurgood,
Today, I checked our internal OTA bootloader with secure, you can find it also download the encrypted FW directly:
So, I think even you use the ethernet, you also can receive the encrypted FW, and write it to the related flash area.
Wish it helps you!
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi kerryzhou
Thanks for the explanation.
Is there an NXP document for the L2 Bootloader?
Where can I find the L2 Bootloader code?
br,
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tony Thurgood,
You are welcome!
Yes, we have, but we can't share it directly in the public community.
Do you already sign the NDA with NXP side?
If not, you can sign the NDA with NXP at first, after the NDA is approved, then you can request it from the technical support case:
Request NDA also can create the above case channel.
Wish it helps you!
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI kerryzhou
Ok, we are sorting out the NDA, thanks.
I have another question related to F/W update.
If the new image is built (using the position independent compiler option), that can be located anywhere in unused flash memory. How are the Interrupts managed?
The interrupt table @ 0x60002000 would need to be updated with the new code position/offsets before the POR reset. But this is not known at build time.
What is the NXP advice for this?
br,
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tony Thurgood,
So normally, you need to use the the secondary bootloader, you define the specific address as your app, then after the app is updated, use the secondary bootloader jump to your new app area.
Your secondary bootloader is located from 0X60002000.
About the detail flow, I suggest you refer to the RT1060 OTA_bootlaoder in the SDK, it seems the RT1020 SDK still don't have it, please download the RT1060 SDK from this link:
Welcome | MCUXpresso SDK Builder
SDK_2.7.0_EVK-MIMXRT1060\boards\evkmimxrt1060\bootloader_examples\ota_bootloader
SDK_2.7.0_EVK-MIMXRT1060\boards\evkmimxrt1060\lwip_examples\lwip_httpssrv_ota
ota_bootloader is the secondary bootloader located from 0X60002000, the lwip_httpssrv_ota is used to upload the firmware through the http.
You can refer to it.
Wish it helps you!
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------