- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
Hi every one,
I would like to know if it is possible to read the Authentication attempts counter of an AESKey authentication object.
From what I understand this is not possible as the only way to read such a value would be to perform an attested read which actually always returns 0x6985 when trying to read an AESKey.
Can someone confirm that it is not possible?
Thank you
已解决! 转到解答。
Unfortunately, i'm still not able to read attempts counter. Read object command fails with a CONDITION_NOT_SATISFIED status word. It seems that AESKey authentication object attributes cannot be read just like normal AESKey. I used the attestation key with ID 0xF0000012 and attestation algorithm EC_SHA_512.
I tried to configure the authentication object with policy ALLOW_READ but key creation fails with the status word WRONG_DATA.
EDIT: Ok, it works. I was using Se05x_API_ReadObjectAttributes() instead of Se05x_API_ReadObject_W_Attst(). However i does not understand why this function could not be used while its purpose seems to be to read object's attributes. As explained above Se05x_API_ReadObject_W_Attst() cannot be used as is because it expects TAG1 which is actually not returned when reading an AESKey object.
Hi @m_grand ,
Sorry, I misunderstood the policies to be validated during secure objects creation as the policies to be allowed on these objects, SW_CONDITIONS_NOT_SATISFIED is returned when you attempt to read a private key or a symmetric key or a userID with the command of "ReadObject", just as specified in AN12413, but you can do an attested read on an AES key (attestation key needs to be an ECDSA key like you wrote) – secure element will not return any key data, but it will return with the object attributes and sign them.
The current MW I think still has an bug which makes this combination of an attested read of an symmetric key still not usable as the MW expects data coming back, but on the IoT Applet it has to work.
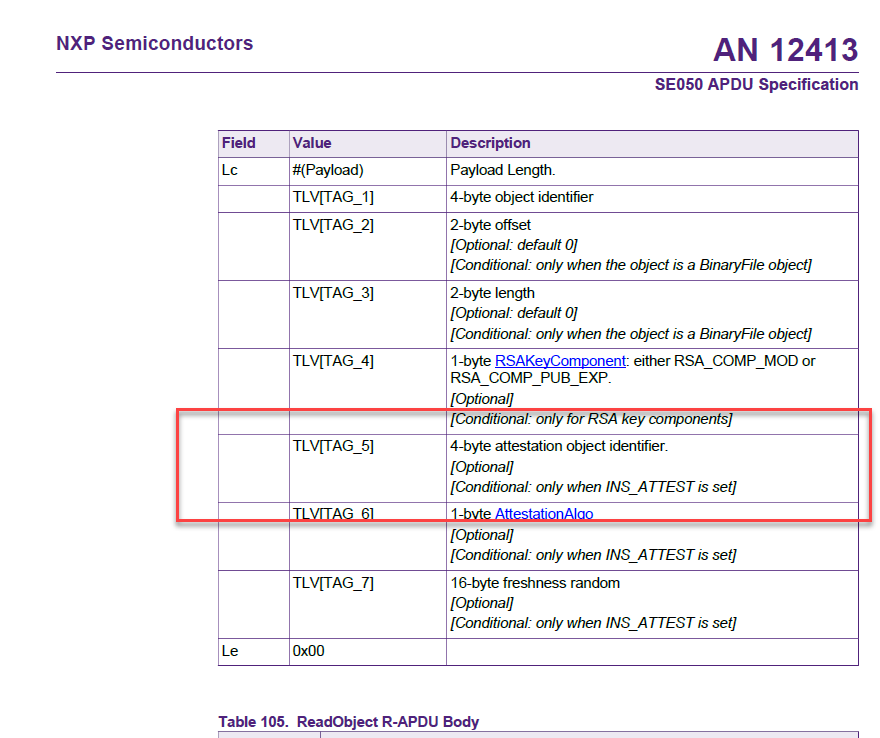
Please also note the TLV_TAG5 is the identifier which specifies the key which is used to sign the data/attributes which are returned by the attested read. Please kindly refer to the following for details.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
Unfortunately, i'm still not able to read attempts counter. Read object command fails with a CONDITION_NOT_SATISFIED status word. It seems that AESKey authentication object attributes cannot be read just like normal AESKey. I used the attestation key with ID 0xF0000012 and attestation algorithm EC_SHA_512.
I tried to configure the authentication object with policy ALLOW_READ but key creation fails with the status word WRONG_DATA.
EDIT: Ok, it works. I was using Se05x_API_ReadObjectAttributes() instead of Se05x_API_ReadObject_W_Attst(). However i does not understand why this function could not be used while its purpose seems to be to read object's attributes. As explained above Se05x_API_ReadObject_W_Attst() cannot be used as is because it expects TAG1 which is actually not returned when reading an AESKey object.
Hello @m_grand ,
You are welcome! Please kindly let me know if there is any further issue.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
Hi @m_grand ,
No, it is not possible as only the asymmetric keys have the policy of POLICY_OBJ_ALLOW_ATTESTATION. Please kindly refer to the page 27 of https://www.nxp.com/docs/en/application-note/AN12413-SE050_APDU_specification.pdf for more details.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------