- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- Identification and Security
- :
- Secure Authentication
- :
- Re: Cannot import RSA public exponent
Cannot import RSA public exponent
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cannot import RSA public exponent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm working with an SE050c (on a OM-SE050ARD board) and a bare metal MCU not supported by the MW, so I am left with implementing my own protocol with APDUs relying on AN12413 APDU specification application note.
When I import an 2048 bit RSA key pair, whith public exponent set to 65537 i.e. {0x01, 0x00, 0x01} the import seems to be successful, at least I receive SW_NO_ERROR at every APDU. However, when I would like to read back the public key, I can read the modulus, but the public exponent returns with SW_CONDITIONS_NOT_SATISFIED. Likewise, all operations (verify, encrypt), which needs the public key returns SW_CONDITIONS_NOT_SATISFIED, while operations requiring the private key (e.g. sign) completes with SW_NO_ERROR, as if the exponent is not actually saved.
If I generate a 2048 bit RSA key on the SE050, all is fine: I can read the public exponent, it returns {0x01, 0x00, 0x01} and all public and private key operations are executed as expected.
What am I doing wrong?
Below is an example:
--- Import RSA key
C-APDU: 80 01 62 00 00 00 9a 11 09 08 00 00 00 00 1b 7c 80 00 41 04 00 00 00 05 42 02 08 00 43 82 00 81 00 f5 97 bb c0 c3 85 81 b9 5b a4 7c 1a d3 49 b3 58 c2 d6 e3 bc dd b6 b5 79 c7 b1 63 88 51 f2 58 bc a9 0c 66 55 95 23 6d e2 47 67 b2 95 fa 57 e0 f4 b5 43 68 86 fe 72 8f c7 d6 14 b2 a9 d6 8e 5a 4c 05 75 6c a5 b9 12 15 f6 3c 9c 35 25 ea 48 02 4a cc f2 f0 05 7c 43 a8 d4 55 5f 2e e3 38 9a f9 88 af b0 16 12 5e 33 c1 ae 51 84 d8 72 8e b4 2d 54 ab 07 c7 f3 f9 1c 39 fc a1 72 22 ee 22 94 6b 3f
R-APDU: 90 00
C-APDU: 80 01 62 00 00 00 8a 41 04 00 00 00 05 44 82 00 80 e4 fe 9f 8d 32 5d 9f ce 62 cf b7 eb 8e a4 e4 f8 fc cb fd 0d f3 62 fb 84 8c 32 9d f6 f6 36 2b 15 d3 e7 6e 2d 2a 74 b2 c4 7d c2 94 0f 8f d5 fb fd 5d 28 94 47 f8 b4 9b 54 e3 83 4b b1 8a ff e2 8c 50 50 f3 92 e2 0f a6 3e b0 94 55 d9 8e 26 c5 f5 ec df f2 2f d1 6c c8 b3 49 e7 d9 11 cb 50 5d 5a 99 00 61 d8 8f a8 d4 11 6e cf c2 d1 0f a6 bd 98 b0 b2 e3 00 be d1 22 b7 4a 51 7d 4f d3 8e cd 01
R-APDU: 90 00
C-APDU: 80 01 62 00 00 00 8b 41 04 00 00 00 05 45 82 00 81 00 db 5a 7d d8 ab 09 c8 96 ec f2 59 e2 7f ca f9 04 13 6a 69 98 5c 12 ff bd d8 8d 68 cf ee 19 5e 06 8b 9a c6 a0 34 07 a3 f2 92 42 5d 70 b5 5b de 51 d2 c0 75 50 f5 5d 0f 6c b6 9a 60 05 6f dc 4f 6c 4d 07 d7 55 a1 9a 34 c1 6c db 3c 61 34 02 c3 01 5a 52 b5 ec c0 53 92 2c ac 5f ca 7a 2a 29 c9 2c bb 76 b4 10 0d d1 7e 71 1a e0 63 8e d6 44 b9 a4 40 ea 3f 3e 7a c6 2a 48 a9 4e 4f 42 90 e2 2d 73
R-APDU: 90 00
C-APDU: 80 01 62 00 00 00 8a 41 04 00 00 00 05 46 82 00 80 1b e8 58 23 8a 16 d4 e9 ff 2a d7 7c 52 b7 0f dc b4 5a 5b ed be 52 ba da 6d 87 a1 ae be 54 dd ad 5c 54 e1 1d 8a 06 0c df 5b 80 42 31 1f 53 71 d1 6f f0 09 1a 38 5a 32 70 07 06 32 4c 61 e7 4b 81 d4 2b f9 73 56 2f 98 10 1d cf 06 23 6c 6a 97 47 a0 65 ae 8b 5b 57 89 a2 28 08 a4 70 c1 b9 7a 97 16 fc 6f f0 47 99 c8 b6 93 2d a8 cd 77 bd d7 6f 6b 61 71 be de 82 78 5b a4 28 08 40 99 44 d7 01
R-APDU: 90 00
C-APDU: 80 01 62 00 00 00 8b 41 04 00 00 00 05 47 82 00 81 00 e7 1a a8 68 01 24 ad 40 a2 41 49 91 e0 0f 49 06 63 b7 70 1b 41 49 2b fc 2a f0 40 24 53 9a fd 44 c5 e8 f0 c6 fe 38 9d f3 cc a6 32 f5 28 c3 e7 9e f3 44 74 6f df 5b 11 77 30 33 df bd f7 4b d7 19 8b 34 3b c9 e6 15 16 5c 7d c7 1a 7e 5c b0 04 dc 8f 6a b3 9f 0a 19 78 58 90 56 d6 56 2e c7 f0 f2 8f 98 17 68 58 0f 19 a0 d0 68 28 e3 7b 14 9f dd 3c bc fc e4 c1 58 03 d6 ce 02 df 1a e6 d6 35 13
R-APDU: 90 00
C-APDU: 80 01 62 00 00 00 0e 41 04 00 00 00 05 48 82 00 04 00 01 00 01
R-APDU: 90 00
C-APDU: 80 01 62 00 00 00 06 41 04 00 00 00 05
R-APDU: 90 00
C-APDU: 80 01 62 00 00 01 0a 41 04 00 00 00 05 4a 82 01 00 db af 68 d4 a9 e5 7c b5 7f 5a 44 23 4c c4 ee 45 59 f3 e0 ff c4 74 fe 1c 42 2b 07 96 b6 6b f2 39 0b 3e 7e c4 b7 99 71 98 fb 33 00 35 44 d9 48 94 38 a4 41 06 8e 09 68 bc 5a 50 a3 e7 04 e3 85 4b 6c 45 d6 fd 75 fb 68 f1 7d aa 21 0a 95 44 67 aa 85 00 a8 05 45 49 0a cc 4e a4 91 29 18 99 1f 74 ab ea 42 77 47 33 67 96 2e 81 50 78 b9 15 04 38 1d c9 b1 6f 8c 5b 54 7a ab 03 6e 3f 39 53 ae 31 39 e8 5a a8 0e 16 6b f3 36 e6 6e 23 89 25 f1 ad 61 d7 bd 93 cc 78 42 61 d5 fe 7c 56 af fa c6 e5 2d 68 44 45 0b 6a 35 11 da 3b 63 e7 a2 87 ca 6e 4d 5f a8 4e d5 38 c2 1f 26 af d5 2c 62 43 4a 88 63 ba 15 21 1d f8 76 1f 91 dd 3e b8 7a 30 63 0b d6 cf 0b 09 2e f3 14 3b 16 a4 db 53 38 e6 38 cb ee e4 30 72 ca 5d 5a b6 df 9c 4d e8 5a 9a 05 2a 3d a2 c3 7a 26 23 15 bc f7 1c 32 c8 66 67 de 3f
R-APDU: 90 00
--- ret: 0
--- Read modulus
C-APDU: 80 02 00 00 00 00 09 41 04 00 00 00 05 44 01 00 00 00
R-APDU: 41 82 01 00 db af 68 d4 a9 e5 7c b5 7f 5a 44 23 4c c4 ee 45 59 f3 e0 ff c4 74 fe 1c 42 2b 07 96 b6 6b f2 39 0b 3e 7e c4 b7 99 71 98 fb 33 00 35 44 d9 48 94 38 a4 41 06 8e 09 68 bc 5a 50 a3 e7 04 e3 85 4b 6c 45 d6 fd 75 fb 68 f1 7d aa 21 0a 95 44 67 aa 85 00 a8 05 45 49 0a cc 4e a4 91 29 18 99 1f 74 ab ea 42 77 47 33 67 96 2e 81 50 78 b9 15 04 38 1d c9 b1 6f 8c 5b 54 7a ab 03 6e 3f 39 53 ae 31 39 e8 5a a8 0e 16 6b f3 36 e6 6e 23 89 25 f1 ad 61 d7 bd 93 cc 78 42 61 d5 fe 7c 56 af fa c6 e5 2d 68 44 45 0b 6a 35 11 da 3b 63 e7 a2 87 ca 6e 4d 5f a8 4e d5 38 c2 1f 26 af d5 2c 62 43 4a 88 63 ba 15 21 1d f8 76 1f 91 dd 3e b8 7a 30 63 0b d6 cf 0b 09 2e f3 14 3b 16 a4 db 53 38 e6 38 cb ee e4 30 72 ca 5d 5a b6 df 9c 4d e8 5a 9a 05 2a 3d a2 c3 7a 26 23 15 bc f7 1c 32 c8 66 67 de 3f 90 00
--- ret: 0
--- Read public exponent
C-APDU: 80 02 00 00 00 00 09 41 04 00 00 00 05 44 01 01 00 00
R-APDU: 69 85
--- ret: -6
--- Generate RSA key
C-APDU: 80 01 62 00 00 00 0a 41 04 00 00 00 0a 42 02 08 00 00 00
R-APDU: 90 00
--- ret: 0
--- Read modulus
C-APDU: 80 02 00 00 00 00 09 41 04 00 00 00 0a 44 01 00 00 00
R-APDU: 41 82 01 00 ac 8e 78 cd 16 f3 78 44 37 89 53 06 14 ca b6 81 b5 ff 69 4b 5a 7c 59 56 30 16 85 42 a3 03 41 c7 73 dd dd aa 51 89 cb df d1 88 4f dd 4b 4d f5 5a 4e a7 8c e9 70 69 3d 27 75 fd 8f d5 9d 16 6f 1f e6 32 ad 8a b4 84 be 5e f7 0e b0 81 2b 91 da 77 ce fc d4 5c ff 07 ac e8 f2 2c e2 4e ec d3 96 4e 42 50 f6 09 05 bd 93 65 70 27 d5 b3 20 fa 94 6a 36 79 62 77 1a bf db 62 cd 62 ae c8 40 24 7d a8 e9 31 5a 8a 37 9f c8 d9 d3 07 be 0e 97 6b 4c 16 f0 fc b5 b5 98 6b b2 9c ee e8 07 ad cc d2 bf 9e b3 23 22 54 ae 99 73 b2 5c 8f d3 64 93 cf 63 3d 47 03 a5 35 7a b4 8d 59 85 2a 48 2b 50 01 26 52 77 dd 5d 8d 50 98 c5 00 69 2d 5c ad 7d fc c0 1f 9d c5 76 33 11 99 3a 0b 43 90 fc 0e 94 e7 71 45 00 99 d6 fa ef 5a 36 3c 2b 56 e7 00 5d ac bc 9c 95 06 d9 c5 72 a8 36 69 b8 73 d5 f9 5b ec 25 11 90 00
--- ret: 0
--- Read public exponent
C-APDU: 80 02 00 00 00 00 09 41 04 00 00 00 0a 44 01 01 00 00
R-APDU: 41 82 00 03 01 00 01 90 00
--- ret: 0
Note, that above I'm importing the public exponent in {0x00, 0x01, 0x00, 0x01} format, and as can be seen it does not generate error but seemingly not saved. It is the same if I use the {0x01, 0x00, 0x01} format.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @krisztian_stancz ,
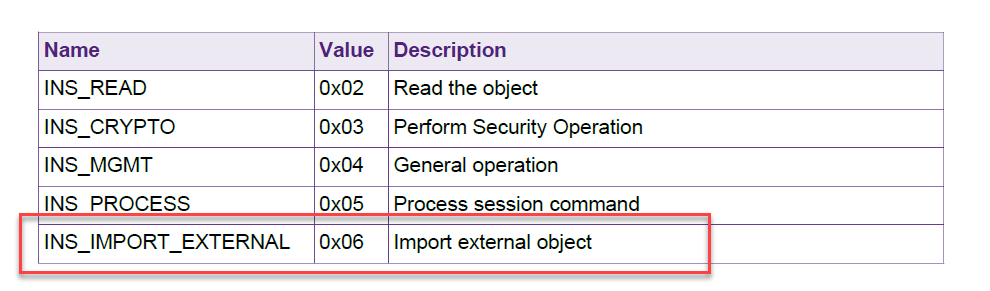
The INS code for import external object is 0x06 instead of 0x01. Please kindly refer to the following for details.
Also as mentioned in AN12413,
Note: The APDU “ImportExternalObject” must not be used without first contacting
NXP to avoid potential problems. If you have used or plan to use the APDU
“ImportExternalObject,” please make sure you contact your NXP representative.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Kan_Li,
Thanks, I appreciate the time you took on answering this! We are importing the key in a secure environment, so wrapping it is not necessary and for us only complicates things. A simple WriteRSAKey operation with a key pair would be sufficient.
Finally I managed to do it, and I see now where my mistake was, but this brought up two problems, which you might be able to forward to the right people.
1.) The issue was caused by the APDU "80 01 62 00 00 00 06 41 04 00 00 00 05" (see the example above) which I sent in between the APDUs with TAG8 and TAG10. Essentially I have initiated a write RSA key pair operation for object #5 with set values, I have filled in the private key data and the public exponent, then by mistake I generated an entirely new key pair in #5 with this APDU, then continued to update the public modulus. This knocked out or corrupted the public exponent.
Although this is clearly not the way it should be used, I think at the point when I set the modulus, either the SE050 should have given an error message (it did not: see the example posted above), because I was updating a public key, but only its second component (after the generate APDU only the modulus, without the exponent), or it should have not deleted the exponent. Either way this seems to me a bug.
2.) The reason APDU "80 01 62 00 00 00 06 41 04 00 00 00 05" got into the code is becasue the wording of the specification is quite ambigous. AN12413 (Rev. 2.12) on page 60 writes:
"TLV[TAG_9] must only contain a value it the key is to be set in raw mode to a known
value and P1KeyType is either P1_KEY_PAIR or P1_PRIVATE; otherwise the value
must be absent and the length must be equal to 0."
This sounds like the TLV length field should be set to 0, and not followed by any value, so: "0x49, 0x00". But sending this gives SW_WRONG_DATA. So I ended up sending an "empty" APDU without TLV[TAG9], which turned out to be command in its own.
It would be more clear to say the TLV[TAG9] "must be absent" in the "otherwise" case. Also on the same page Table 95 should be updated, because TLV[TAG8]...TLV[TAG10] are actually not mandatory, but conditional elements, depending on what the user is trying to achieve. This would also help clarifying the point above.
Kind reagrds,
Krisztian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @krisztian_stancz ,
Please kindly have my comments as below:
1) Indeed the APDU "80 01 62 00 00 00 06 41 04 00 00 00 05" is correct according to the spec, "For key pairs, if no component is present (TAG_3 until TAG_9), the key pair will be generated on chip;" so I don't think SE050 should return an error code for this case, it is the user application's task to construct the right APDU commands, and we recommend building your own application based on the latest MW to not only prevent such kind of issue but also obtain the most updated function as well as better support on bug fixing.
2) Thanks for the suggestion regarding the AN12413, I will share with the expert team.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content