- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- Product Forums
- :
- S32K
- :
- about secure boot of CSEc model
about secure boot of CSEc model
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi everyone
I have some questions about secure boot.
After the step 5, what will happened if the MAC is not matched? Should I do anything else to complete the sequence of secure boot?
P.S.: I want to achieve the function that the bootloader won't start when MAC's verification fails.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Keane,
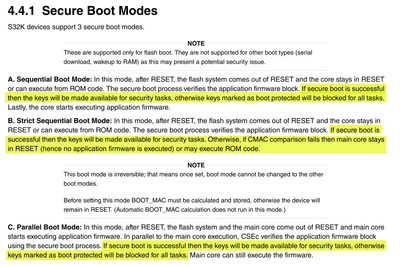
you can find this description two pages above in AN501:
So, in case of sequential and parallel boot mode, the only consequence is that you won't be able to use boot protected keys.
In case of strict sequential boot mode, the device will stay in reset forever. There's no way to recover, the device must be replaced. Also once this mode is enabled, it cannot be changed anymore. So, my recommendation is to enable this feature once all your development is finished.
Don't be confused by note "or may execute ROM code". This is a general description taken from SHE specification, it does not apply to this device.
There are two additional commands: CMD_BOOT_OK and CMD_BOOT_FAILURE. It's not mandatory to use them but the commands can be used to check additional blocks after the autonomous secure boot finishes (i.e. you can create chain of trust).
For example: you can configure CSEc to cover a bootloader by autonomous secure boot. The bootloader then can initiate calculation of MAC over application. If the MAC is correct, the bootloader should execute CMD_BOOT_OK to confirm the secure boot (including this additional checking) was OK. If the MAC is wrong, it can execute CMD_BOOT_FAILURE which will finish this secure boot process and which will disable access to boot protected keys.
Notice that it's not important to execute CMD_BOOT_OK after successful autonomous secure boot. Boot protected keys will be available now anyway. But it's recommended. The commands can't be executed second time, so it helps to avoid hacker attack.
Hope this helps.
Regards,
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Keane,
you can find this description two pages above in AN501:
So, in case of sequential and parallel boot mode, the only consequence is that you won't be able to use boot protected keys.
In case of strict sequential boot mode, the device will stay in reset forever. There's no way to recover, the device must be replaced. Also once this mode is enabled, it cannot be changed anymore. So, my recommendation is to enable this feature once all your development is finished.
Don't be confused by note "or may execute ROM code". This is a general description taken from SHE specification, it does not apply to this device.
There are two additional commands: CMD_BOOT_OK and CMD_BOOT_FAILURE. It's not mandatory to use them but the commands can be used to check additional blocks after the autonomous secure boot finishes (i.e. you can create chain of trust).
For example: you can configure CSEc to cover a bootloader by autonomous secure boot. The bootloader then can initiate calculation of MAC over application. If the MAC is correct, the bootloader should execute CMD_BOOT_OK to confirm the secure boot (including this additional checking) was OK. If the MAC is wrong, it can execute CMD_BOOT_FAILURE which will finish this secure boot process and which will disable access to boot protected keys.
Notice that it's not important to execute CMD_BOOT_OK after successful autonomous secure boot. Boot protected keys will be available now anyway. But it's recommended. The commands can't be executed second time, so it helps to avoid hacker attack.
Hope this helps.
Regards,
Lukas