- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- QorIQプロセッシングプラットフォーム
- :
- QorIQ
- :
- Re: P5020 Secure Boot
P5020 Secure Boot
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
P5020 Secure Boot
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I am attempting to secure boot a P5020 and so far my attempts have not been successful.
I am reading in the SDK documentation, it sounds like a HASH has to be program in the SFP fuse. It also looks like the fuse can only be programed two times. Is there anyway to perform secure boot without programing the fuse?
I am very new to all of this, any help is appreciated.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello Ana Lim,
You could set SB_EN bit to 1 in RCW to enable secure boot.
You could write SRK hash keys to the mirror registers in the prototype stage.
For details, please refer to https://community.nxp.com/docs/DOC-332248
Thanks,
Yiping
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Yiping,
Any feedback?
I am trying to also figure out the address of the shadow registers? Any suggestions?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello Ana Lim,
Please use secure RCW provided in SDK 1.9.
I uploaded QorIQ Linux SDK 2.0 user manual https://drive.google.com/open?id=1-goeJsMtBB1X7X9Bfo9NV42YhAs_iuOM , please refer to the section "10.3.1.14 Appendix P3/P4/P5/T1_T2_T4 Secure Boot demo".
Please refer to the following CCS command for P5020
# Connect to CCS and configure Config Chain
ccs::config_chain p3040
display ccs::get_config_chain
#Check Initial SNVS State and Value in SCRATCH Registers
ccs::display_mem 0 0xfe314014 4 0 1
ccs::display_mem 0 0xfe0e0200 4 0 4
#Wrie the SRK Hash Value in Mirror Registers
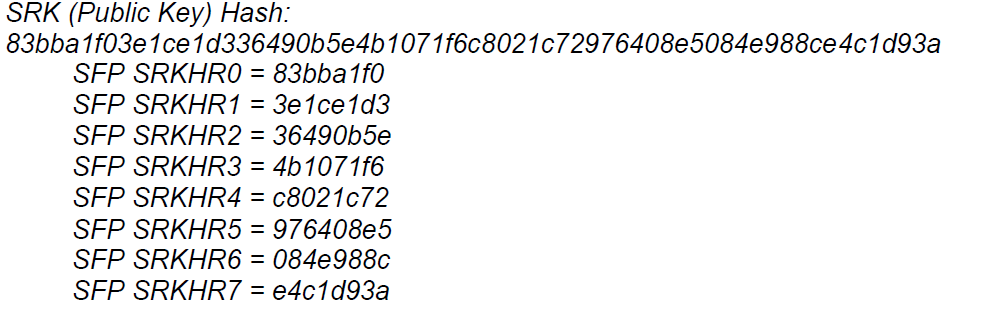
ccs::write_mem 0 0xfe0e807c 4 0 <SRKH1>
ccs::write_mem 0 0xfe0e8080 4 0 <SRKH2>
ccs::write_mem 0 0xfe0e8084 4 0 <SRKH3>
ccs::write_mem 0 0xfe0e8088 4 0 <SRKH4>
ccs::write_mem 0 0xfe0e808c 4 0 <SRKH5>
ccs::write_mem 0 0xfe0e8090 4 0 <SRKH6>
ccs::write_mem 0 0xfe0e8094 4 0 <SRKH7>
ccs::write_mem 0 0xfe0e8098 4 0 <SRKH8>
#Get the Core Out of Boot Hold-Off
ccs::write_mem 0 0xfe0e00e4 4 0 0x00000001
Thanks,
Yiping
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Yiping,
The ccs commands above only write hash to the SRKH. Do I need to burn the OTPMK since those registers seems to be write protected?
I am seeing the SCRATCHRW2=0x00010000 and SECMON_HPSR=0x812d0b00.
Ana
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello Ana,
You need to burn OTPMK and please make sure bits OTPMK_ZERO, OTMPK_SYNDROME and PE are 0 of the status register of sec mon block.
Thanks,
Yiping
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Where can I find information about these registers for different boards? I am interested in P4080DS and P5040 boards. What is the address and which bits represent them? I am not able to find them in SDK 2.0 documentation and TRM for the boards. Greatly appreciate your help in this regard. Thank you!
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Yiping, thanks!
I am seeing a mention of running the OTPMK Hamming algorithm on the OTPMK hash. Is that necessary?
Can the OTPMK hash be obtained the same way as the SRKHR?
I am suing the provide uni_sign tool to get the SRKHR hash, can it be used for the OTPMK hash?
Also, is the OTPMK hash need to be byte swapped? From the Setting up Secure boot document, the way that OTPMK hash is listed is a bit different from the SRKHR (which has no mention of bit order).
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Blow OTPMK to fuse array is necessary to enable secure boot.
Generate OTPMK key with CST command gen_otpmk_drbg, please refer to the following.
./gen_otpmk_drbg <bit_order> [string]
<bit_order> : (1 or 2) OTPMK Bit Ordering Scheme in SFP
1 : BSC913x, P1010, P3, P4, P5, C29x
2 : T1, T2, T4, B4, LSx
<string> : 32 byte string
No need to do swapping for the generate OTPMK key.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thanks Yiping!
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Yiping,
Thanks for your answer. I am reviewing the document above and have some questions.
In the document the PBI commands are as follow, but it is a bit different than the rcw that i am using (from SDK 1.9).
| Setting up Secure Boot on PBL Based Platforms in Prototype Stage | RCW from SDK1.9 for p5020 rcw_15g_sben_2000mhz.bin |
|---|---|
#LAW for ESBC 09000c10 00000000 09000c14 c0000000 09000c18 81f0001b # LAW for CPC/SRAM 09000d00 00000000 09000d04 bff00000 09000d08 81000013 # Scratch Registers 090e0200 c0b00000 090e0208 c0c00000 # CPC SRAM 09010100 00000000 09010104 bff00009 # CPC Configuration 09010f00 08000000 09010000 80000000 | #LAW for ESBC 09000cd0 00000000 09138000 00000000 09138000 00000000 # Scratch Registers 090e0200 c0b00000 |
In the rcw_15g_sben_2000mhz.bin, there is not commands to write the CPC/SRAM. Are they not needed on p5020?
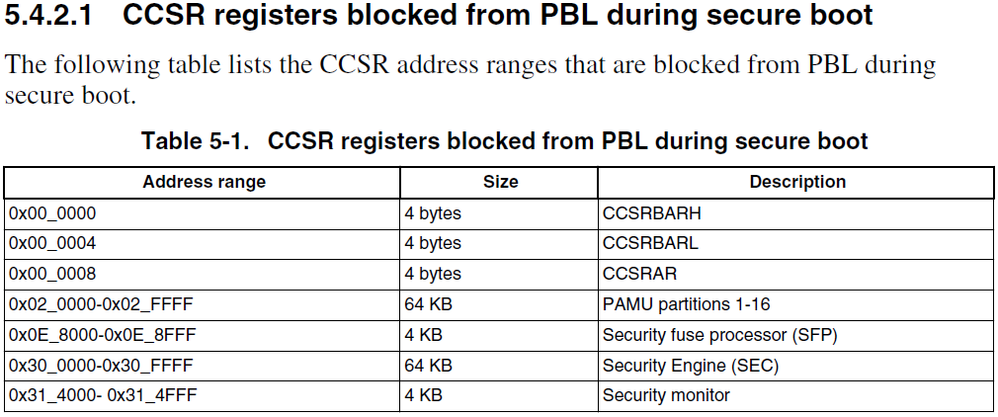
Also, in the "Setting up Secure Boot on PBL Based Platforms in Prototype Stage", there is a section to write the keys hash in ccs. However, the QorIQ P5020 Reference Manual 5.4.2.1, said that those register are blocked during secure boot.
I did try to write to the 0xe_805c and confirmed that the write did not go successfully.
Did I miss something?