- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- RFID / NFC
- :
- NFC
- :
- Re: Ntag 424DNA write lock failed while using android Native method
Ntag 424DNA write lock failed while using android Native method
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
Ntag 424DNA write lock failed while using android Native method
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
We have a React native mobile application which write some data (NDEF) to NTAG 424 DNA. After writing Tag needs to be write locked.
For write locking purpose, used android default method makeReadonly(). But it failing on tag 424 DNA.
I was able to format and Write-lock with NXP tagWriter android application. but not with android API s
Given below is tag info which I used:-
{ "canMakeReadOnly":false, "id":"043743CE80", "isWritable":true, "maxSize":254, "ndefMessage":[], "techTypes":[ "android.nfc.tech.IsoDep", "android.nfc.tech.NfcA", "android.nfc.tech.Ndef" ], "type":"NFC Forum Type 4" }
Here is a part of code which Currently using
try{ await NfcManager.writeNdefMessage(bytes) .then(()=>NfcManager.makeReadOnlyAndroid()) .then((result)=>{ console.log("Make read Only result:->",result); }); } catch (ex) { console.warn('exception', ex); _cleanUp(); }
The same is working for "NTAG216"
{"canMakeReadOnly": true, "id": "04883C82B25680", "isWritable": true, "maxSize": 868, "ndefMessage": [{"id": "", "payload": [Array], "tnf": 1, "type": [Array]}], "techTypes": ["android.nfc.tech.NfcA", "android.nfc.tech.MifareUltralight", "android.nfc.tech.Ndef"], "type": "NFC Forum Type 2"}
for react native i have also used
https://github.com/whitedogg13/react-native-nfc-manager :- this plugin.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Jonathan,
Many thanks for your support. I've just consolidated the steps I did into a file. This may give you a clear understanding of where I'm stuck.
https://docs.google.com/document/d/16lOoh2Fuo6cTDzgddQXz4VOy0K8mGEaIIApeJdeNMhw/edit?usp=sharing
Thanks & Regards,
Anandhu
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
I dont think the same process as an NTAG216 can apply to an NTAG 424,
the NTAG is a T2T which means that the capability container and the protection is handled by a PROT register and a PWD. for NTGA 424 is different since it is a T4T the capability container is not in a memory sector like NTAG 215 is in a file inside the NTAG 424
in order to interact with this you should first select the FID, then authenticate to the NTAG 424 then modify the value of the CC file.
please check if there is some API for T4T or please perform the sequence to modify the NTAG 424 CC file and also it would be good that you change the write, change and R/W access key to a known key or if you dont want anybody to using this in the future change them to F, and just leave the read value to E to everyone can read the NDEF file.
maybe you can use as reference the following post
https://community.nxp.com/t5/NFC/Change-Keys-and-quot-lock-quot-NTAG-DNA-424/m-p/1058607#M7158
it does not uses a code example or something but you can see how is the process and apply it to your code.
BR
Jonathan
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hope their is only
[NfcTech].transceive([0x00,etc..])
but am completely confused with these hexadecimal part. Is it possible to read and modify CC file using these commands,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I am sorry but I dont completely understand this reply, can you please elaborate more on this.
also please confirm you are using the DS of NTAG 424? because all of this is explained there, also in the features and hints you can find examples of how to do some things on NTAG 424.
https://www.nxp.com/docs/en/data-sheet/NT4H2421Gx.pdf
in section 5.1 you can see the user memory and the explanation of the CC file also section 10 for the command set like write and read.
https://www.nxp.com/docs/en/application-note/AN12196.pdf
in section 6 there is a personalization example where you can see how to modify the CC file.
BR
Jonathan
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thanks for helping me to complete AuthenticateEV2First using APDU commands.
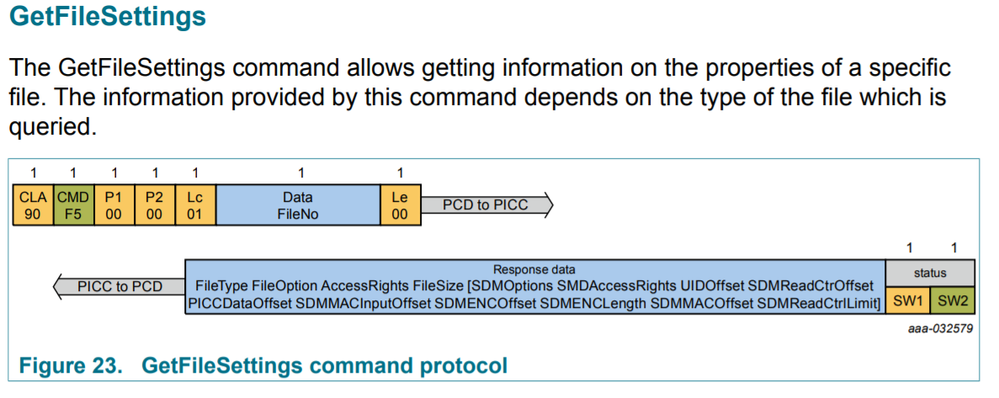
Now am trying to Get File Settings using this [CC file].
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
We were able to complete part 1 of "AuthenticateEV2First" using command :
1.
{0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0} (0x00)but the response was "Pad block Corrupted".- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
I know this question is from a long time ago. However, I am currently stuck at this step of writing on NTAG 424 DNA. I would like to know if you have solved this problem. Additionally, I cannot convince myself to consider the 147, 205, 124, 135, 153, 89, 104, 47, 41, 139, 13, 19, 29, 16, 52, 216 as RndB . I think the result of E(k0 , RndB) should be equal to 147, 205, 124, 135, 153, 89, 104, 47, 41, 139, 13, 19, 29, 16, 52, 216.
Thank you in advance