- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- QorIQプロセッシングプラットフォーム
- :
- レイヤースケープ
- :
- Issue with secure boot on ls1043ardb (blank screen)
Issue with secure boot on ls1043ardb (blank screen)
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
I am using a custom board based on LS1043ARDB and I want to enable secure boot.
I have performed the following steps
- created keys using cst
- placed srk.pub and srk.pri keys in atf source folder
- created RCW bin with SB_EN and BOOT_HO as 1
- compiled secure uboot with ls1043ardb_tfa_SECURE_BOOT_defconfig
- generated signed pbl and fip image without optee using "make PLAT=ls1043ardb TRUSTED_BOARD_BOOT=1 CST_DIR=<cst dir path> RCW=ls1043ardb/rcw_1200_sdboot.bin
BL33=u-boot.bin pbl fip"
- got bl2_sd_sec.pbl and fip.bin in folder build/ls1043ardb/release/
- flashed pbl and uboot in eMMC using mmc write 0xa0000000 8 (size of bl2_sd_sec.pbl in hexadecimal) mmc write 0xa0000000 800 (size of fip.bin in hexadecimal)
- cpld reset sd (getting a blank screen here as all cores are on hold)
Read RCW from target device using JTAG, PFA snap
- opened ccs console and wrote SRKH in mirror registers
In the last, getting the core out of boot hold-off
ccs::write_mem 32 0x1ee00e4 4 0 0x00000001
But I am seeing a blank screen only and no output in the console.
I tried to write OTPMK fuse values on shadow registers after generating with ./gen_otpmk_drbg -b 2
However, no luck still seeing the same blank screen.
Could you please help what went wrong here?
Also wanted to understand role of OTPMK and how it impacts secure boot, as images are signed with srk private keys and public hashes flashed in mirror registers.
解決済! 解決策の投稿を見る。
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Please be very cautious with secure boot verification.
It is strongly recommended to repeatedly read the <Chapter 6 Security> section of LSDK 2108 until you fully understand what you are doing.
There are several key points to remind you of what you need to pay attention to:
1.OTPMK must be fused (whether you are verifying secure boot or mass production). Here, you can burn a minimal Hamming code OTPMK such as 0xF. For verification purposes, SRKH can be written to the mirror register, but for mass production, it needs to be permanently fused.
2. When burning fuse, attention should be paid to prog_sfp voltage control.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Yes, I am already running secure boot on my device, by flashing OTPMK permanently.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thanks @kshitiz too look into the query.
I have dumped all the required registers after successfully written SRKH and OTPMK.
SecMon HPSR -> 0x1e90014
SCRATCHRW1 -> 0x1ee0200
SCRATCHRW2 -> 0x1ee0204
SCRATCHRW3 -> 0x1ee0208
SCRATCHRW4 -> 0x1ee020c
(bin) 23 % ccs::display_mem 32 0x1ee0200 4 0 1
+0 +4 +8 +C
[0x01EE0200] 10015000 (correct boot location pointer)
(bin) 24 % ccs::display_mem 32 0x1ee0204 4 0 4
+0 +4 +8 +C
[0x01EE0204] 00000101 00000000 00000000 00000000
(bin) 25 % ccs::display_mem 32 0x1ee0208 4 0 4
+0 +4 +8 +C
[0x01EE0208] 00000000 00000000 00000000 00000000
(bin) 26 % ccs::display_mem 32 0x1ee020c 4 0 4
+0 +4 +8 +C
[0x01EE020C] 00000000 00000000 00000000 00000000
(bin) 27 % ccs::display_mem 32 0x1e90014 4 0 4
+0 +4 +8 +C
[0x01E90014] 8000AB00 80000000 00000000 00000000
(bin) 28 % ccs::display_mem 32 0x1e90018 4 0 4
+0 +4 +8 +C
[0x01E90018] 80000000 00000000 00000000 00000000
@kshitiz Can you please share commands to debug the core status and find out where my core is stuck?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
Have you seen SNVS register state?
Is there any issue reported by ISBC in SCRATCHRW2 register?
Thanks
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @kshitiz
Yes for SCRATCHRW2 reg I am getting 00000101 error code.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @gandhi_999,
0x101 refers to ERROR_STATE_NOT_CHECK SEC_MON which means State Machine not in CHECK state at start of ISBC.
Some
Security violation could have occurred.
Kindly check.
Btw, are you trying with vanilla NXP code, or you are using your own custom binaries?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi @kshitiz
I am using custom binaries, as stated earlier non secure are booting.
Can you please help to know the security violation for not in check state?
Here is the dump of SecMon HPSR -> 0x1e90014 and SecMon HPSVSR -> 0x1e90018 registers.
(bin) 68 % ccs::display_mem 32 0x1e90014 4 0 4
+0 +4 +8 +C
[0x01E90014] 8000AB00 80000000 00000000 00000000
(bin) 69 % ccs::display_mem 32 0x1e90018 4 0 4
+0 +4 +8 +C
[0x01E90018] 80000000 00000000 00000000 00000000
Thanks.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thanks @kshitiz for the response.
Yes I have checked SCRATCHHRW2.
before writing SRKH and OTPMK
(bin) 41 % ccs::display_mem 32 0x1e90014 4 0 1
+0 +4 +8 +C
[0x01E90014] 8800AB00
After writing SRKH and OTPMK
(bin) 60 % ccs::display_mem 32 0x1e90014 4 0 1
+0 +4 +8 +C
[0x01E90014] 8000AB00
I believe ideally it should be 0x09 for check state then it transits to secure state
so, ideal value should be 80000900 but I am getting 0x8000AB00
Can you help me what went wrong here?
Thanks.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Kindly provide the updates on this.
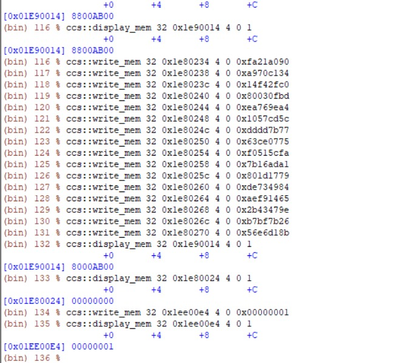
With SB_EN=0 and BOOT_HO=0 in RCW, board is able to boot non securely with the same bl2_sd_sec.pbl and fip.bin image.
With SB_EN=1 and BOOT_HO=1 in RCW and after writing SRKH and OTPMK using ccs as shown in attached snap, board is not able to boot (no output in console) with the same bl2_sd_sec.pbl and fip.bin image.
Thanks