- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- 通用微控制器
- :
- Kinetis微控制器
- :
- SHA-256 with mmCAU in K64
SHA-256 with mmCAU in K64
Hi All
I have been using SHA256 in mbedTLS and wanted to improve its speed by making use of the mmCAU in the K64.
Using the M4 assember code supplied [mmcau_sha256_functions.s] and the calls according to https://www.nxp.com/docs/en/user-guide/CAUAPIUG.pdf I haven't yet been able to get correct output.
Taking a simple test case of a 64 byte input block of "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"
the known result is
FFE054FE7AE0CB6DC65C3AF9B61D5209F439851DB43D0BA5997337DF154668EB
but I get always
0x45 0xea 0x6b 0xd6 0x74 0x80 0x39 0xe8 0x86 0xcd 0xc4 0x4e 0xa9 0x64 0x55 0x02 0x7e 0xe5 0xcc 0x61 0xeb 0x5e 0x61 0x0a 0x97 0xa4 0x42 0x7e 0x66 0x93 0x7a 0x9e
using either of thee methods:
mmcau_sha256_initialize_output((const unsigned int *)sha256.state);
mmcau_sha256_hash((const unsigned char *)sha256.buffer, (unsigned int *)sha256.state);
or
mmcau_sha256_initialize_output((const unsigned int *)sha256.state);
mmcau_sha256_hash_n((const unsigned char *)sha256.buffer, (const int)1, (unsigned int *)sha256.state);
or
mmcau_sha256_update((const unsigned char *)sha256.buffer, (const int)1, (unsigned int *)sha256.state);
In the third case mmcau_sha256_initialize_output() is not needed beforehand.
All buffers are aligned and the single block case (no padding) with repeated data should avoid any possible problems with preparing data correctly (like endian-ness).
Looking at the mmcau_api in the SDK reference it tests the speed of the operation but not the actual result.
Anyone see a reason why the library functions wouldn't return good values?
Regards
Mark
已解决! 转到解答。
Hi Mark,
I got feedback from Kinetis product team.
There mentioned the AN4307 and related software AN4307SW for your reference.
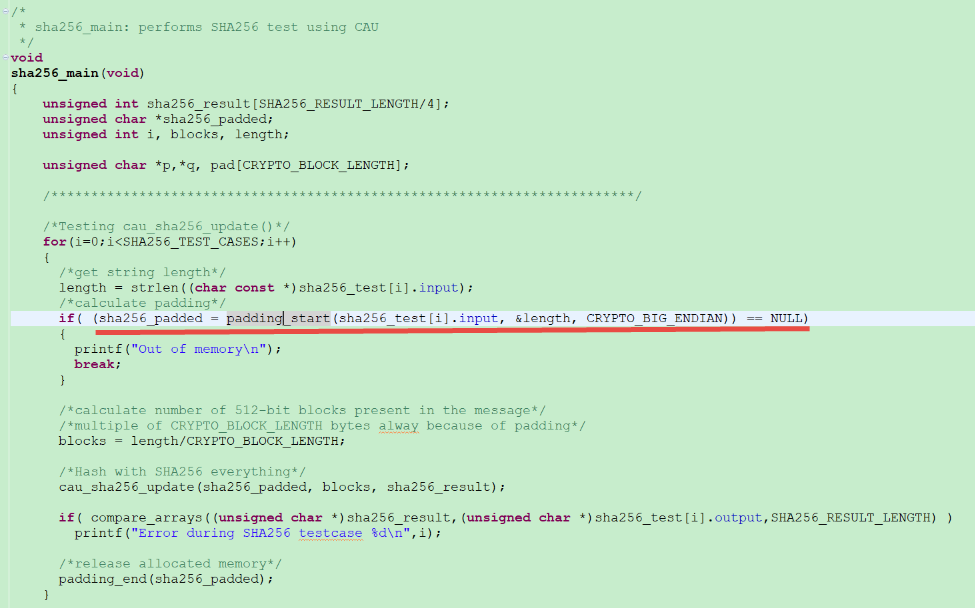
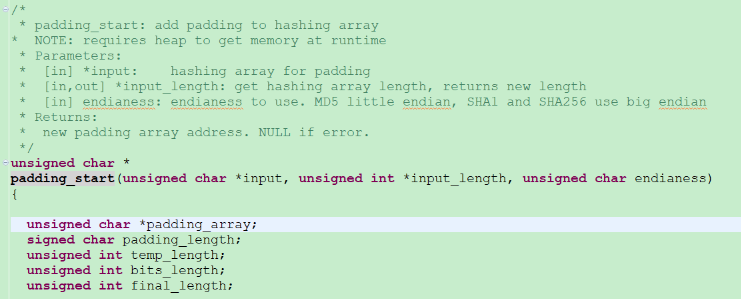
The AN4307 indicates the hashing requires the padding, I checked the SHA256 hash calculation demo of MCF54418 chip calling padding_start() function before calculation. The software project embedded in AN4307SW package.
I attached the padding_start() function below for your reference:
SHA256 test code:
padding_start() API function:
Wish it helps.
Have a great day,
Mike
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------
Hi Mark,
I got feedback from Kinetis product team.
There mentioned the AN4307 and related software AN4307SW for your reference.
The AN4307 indicates the hashing requires the padding, I checked the SHA256 hash calculation demo of MCF54418 chip calling padding_start() function before calculation. The software project embedded in AN4307SW package.
I attached the padding_start() function below for your reference:
SHA256 test code:
padding_start() API function:
Wish it helps.
Have a great day,
Mike
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------
Many thanks Mike
Now it works:
0xff 0xe0 0x54 0xfe 0x7a 0xe0 0xcb 0x6d 0xc6 0x5c 0x3a 0xf9 0xb6 0x1d 0x52 0x09 0xf4 0x39 0x85 0x1d 0xb4 0x3d 0x0b 0xa5 0x99 0x73 0x37 0xdf 0x15 0x46 0x68 0xeb
I note that:
1. When you tested you seem to have prepared padding but called MMCAU_SHA256_Update() with the wrong block length (i.e. 1) - it needs to be 2 (to include the padding block). I had the same results before I realised this...
2. In the guide https://www.nxp.com/docs/en/user-guide/CAUAPIUG.pdf (which is the document linked to on the Kinetis pages) this requirement is not discussed anywhere and so doesn't allow the API to be used without additional knowledge (and additional code)
3. It may make sense to merge https://www.nxp.com/docs/en/application-note/AN4307.pdf and https://www.nxp.com/docs/en/user-guide/CAUAPIUG.pdf in some way so that the are complete.
4. Another thing that the https://www.nxp.com/docs/en/user-guide/CAUAPIUG.pdf doesn't state is that the output (which has the correct values if the padding block is prepared) is in big-endian (stored as long words) and so a big-endian to little-endian conversion also needs to be added at the end (this is mentioned in the application note).
Thanks again because without this tip I doubt that I would have been able to work out what was going on and how to use the SHA256 in the mmCAU (without chancing on the second document;-)
Regards
Mark
Hi Mark,
I did a test with MCUXpresso SDK [mmcau] demo at FRDM-K64F board.
I get the SHA256 hash result of "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa" is:
df5bb81ce81e0626fb45a8944fd40f31b25e6816d6d499c1ab90492900635e66
The demo called MMCAU_SHA256_Update() function to do SHA256 HASH calculator.
I need to check with Kinetis product team why the SHA256 HASH result is incorrect.
I will let you know when there with any feedback.
Thank you for the patience.
Have a great day,
Mike
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------
Hi Mike
Many thanks.
I am also wondering why the mmcau interface is only available in assembler since, even if a little faster than a C implementation, it is almost impossible to maintain (especially if David Schimke and Teejay Ciancio have left Freescale/NXP in the meantime). It also restricts use to GCC (since it is not compatible with IAR, for example, and thus excludes use in quite an important percentage of developments).
This is one reason the SHA-256 in the HW accelerator hasn't been used to date since it has this limitation.
In any case, hopefully the problem can be identified quickly.
Regards
Mark