- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- i.MX Forums
- :
- i.MX Processors
- :
- Re: i.MX Security Reference Design Clarification Questions
i.MX Security Reference Design Clarification Questions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
We implemented the security reference design described in section 10.9 of i.MX Linux User's Guide. Our custom board is based on the imx8mn_evk machine, and the image complies and boots successfully. However, we have questions based on the security-related messages we see during boot (see attached screenshot):
- Does "No HAB Events Found!" message mean a successful image authentication?
- Does the meta-secure-boot layer automatically program the SRK tabe hash fuse, or do we need to do this ourselves?
- We think we have to program the SRK hash fuse ourselves, but if that is the case, how come we got a successful authentication (assuming "No HAB Events Found!" means successful authentication)?
- We tried to read the SRK hash fuse (fuse 0x580 [256 bits]) to verify, but we always read zeros using uboot `fuse read` command. Is there a way to read this fuse?
Thank you,
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After some troubleshooting, the answers are summarized below:
- Yes
- No
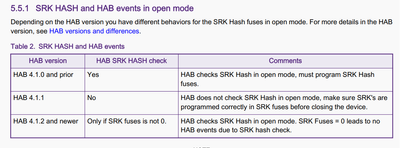
- Because HAB 4.1.2 and higher only perform a hash check if SRK keys are not zeros. In this case, the SRK fuse was not programmed, defaulting to zero and, therefore, bypassing the hash check. This is only supported by the table posted below from @Harvey021. I can't find it in AN4581, but it matches what we are experiencing. @Harvey021, could you post the source of that table?
- A reset is required to read the fuse; otherwise, it reads zero.
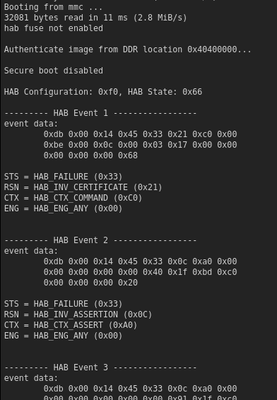
The combination of 3 and 4 made us doubt if we had a proper image before closing the device. We really wanted to see an intentional authentication failure. The only way to do this is to program the fuse and then generate an image with a different SRK table. Then, you will get the authentication failure messages as shown below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
HAB (some versions and open device) won't compare SRK table against fuses when fuses are 0's. That is correct, we have to burn SRK hash.
Without burning SRK hash, we will not get complete authentication. I think that the reference from Linux User guide mainly focus on the image signing with automation with Yocto build.
Regards
Harvey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This response confirms that the meta-secure-boot layer provided in the security reference design dose not program the SRK fuse and we would have to do it ourselves. Based on this clarification how come we are passing authentication when the fuse is all zero?
The statement “HAB (some versions and open device) won't compare SRK table against fuses when fuses are 0's.” does not agree with the statement “All HAB functions are executed as for a closed device.” mentioned in section 6.1.2.5 in imx8mn reference manual. Can you clarify?
No answers were given to questions 1 and 4. Could you please provide answers.
thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Q1, correct.
Q4, zeros means that there are no fuses hash burned.
Regards
Harvey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please answer, "Based on this clarification, how come we are passing authentication when the fuse is all zero?"
Also, we attempted to program the fuse using uboot fuse commands, but we are still reading zeros.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please refer to the AN4581.
Regards
Harvey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Harvey021, where did you get the table you copied (5.5.1)? This was not included in AN4581.We are familiar with AN4581, but it does not provide answers to our issue.
Have you attempted secure boot on imx8mn EVK? Were you able to read back the SRK fuse after programming, or did you get zeros as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AN4581:
i.MX Secure Boot on HABv4 Supported Devices (nxp.com)
Or search "AN4581" from nxp.com
Have you reset the board before read it? Please share more details about how you program SRK fuse hashs.
Regards
Harvey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After some troubleshooting, the answers are summarized below:
- Yes
- No
- Because HAB 4.1.2 and higher only perform a hash check if SRK keys are not zeros. In this case, the SRK fuse was not programmed, defaulting to zero and, therefore, bypassing the hash check. This is only supported by the table posted below from @Harvey021. I can't find it in AN4581, but it matches what we are experiencing. @Harvey021, could you post the source of that table?
- A reset is required to read the fuse; otherwise, it reads zero.
The combination of 3 and 4 made us doubt if we had a proper image before closing the device. We really wanted to see an intentional authentication failure. The only way to do this is to program the fuse and then generate an image with a different SRK table. Then, you will get the authentication failure messages as shown below.