- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
S32K144 System MPU fails to write protect Flash memory region
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Dear Community members,
I have been working on NXP S32K144 System MPU.
I have successfully,
1] Read protect flash memory region.[0x10000800 - 0x1000081F]
2] Read/Write protect SRAM memory region.[0x0100 0001 - 0x0100 0020]
For every memory access violations exception is thrown.
But for,
3] Write protect flash memory region.[0x10000800 - 0x1000081F] there is no exception generated and the memory
gets written successfully.
Following is the profile i have initialized MPU with.
/*! Master access rights configuration 0 */
const mpu_master_access_right_t memProtect1_AccessRightConfig0[] =
{
/*! CORE */
{
.masterNum = FEATURE_MPU_MASTER_CORE, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_NONE, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
},
/*! DEBUGGER */
{
.masterNum = FEATURE_MPU_MASTER_DEBUGGER, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
},
/*! DMA */
{
.masterNum = FEATURE_MPU_MASTER_DMA, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
}
};
/*! Master access rights configuration 1 */
const mpu_master_access_right_t memProtect1_AccessRightConfig1[] =
{
/*! CORE */
{
.masterNum = FEATURE_MPU_MASTER_CORE, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
},
/*! DEBUGGER */
{
.masterNum = FEATURE_MPU_MASTER_DEBUGGER, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
},
/*! DMA */
{
.masterNum = FEATURE_MPU_MASTER_DMA, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
}
};
/*! Master access rights configuration 2 */
const mpu_master_access_right_t memProtect1_AccessRightConfig2[] =
{
/*! CORE */
{
.masterNum = FEATURE_MPU_MASTER_CORE, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_R, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
},
/*! DEBUGGER */
{
.masterNum = FEATURE_MPU_MASTER_DEBUGGER, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
},
/*! DMA */
{
.masterNum = FEATURE_MPU_MASTER_DMA, /*!< Master number */
.accessRight = MPU_SUPERVISOR_USER_RWX, /*!< Access right */
.processIdentifierEnable = false /*!< Process identifier enable */
}
};
/*! User configuration */
const mpu_user_config_t mpu_memConfig[] =
{
/*! Region number 0 */
{
.startAddr = 0x00000000U, /*!< Memory region start address */
.endAddr = 0xFFFFFFFFU, /*!< Memory region end address */
.masterAccRight = memProtect1_AccessRightConfig0, /*!< Master access right */
.processIdentifier = 0x00U, /*!< Process identifier */
.processIdMask = 0x00U /*!< Process identifier mask */
},
/*! Region number 1 */
{
.startAddr = MPU_REG1_START_ADDR,//0x00000000U, /*!< Memory region start address */
.endAddr = MPU_REG1_END_ADDR,//0x0007FEFFU, /*!< Memory region end address */
.masterAccRight = memProtect1_AccessRightConfig2, /*!< Master access right */
.processIdentifier = 0x00U, /*!< Process identifier */
.processIdMask = 0x00U /*!< Process identifier mask */
},
/*! Region number 2 */
{
.startAddr = 0x00000000U, /*!< Memory region start address */
.endAddr = 0x100007FFU, /*!< Memory region end address */
.masterAccRight = memProtect1_AccessRightConfig1, /*!< Master access right */
.processIdentifier = 0x00U, /*!< Process identifier */
.processIdMask = 0x00U /*!< Process identifier mask */
},
/*! Region number 3 */
{
.startAddr = 0x10000820U, /*!< Memory region start address */
.endAddr = 0xFFFFFFFFU, /*!< Memory region end address */
.masterAccRight = memProtect1_AccessRightConfig1, /*!< Master access right */
.processIdentifier = 0x00U, /*!< Process identifier */
.processIdMask = 0x00U /*!< Process identifier mask */
},
/*! Region number 4 */
{
.startAddr = 0x0007FF20U, /*!< Memory region start address */
.endAddr = 0xFFFFFFFFU, /*!< Memory region end address */
.masterAccRight = memProtect1_AccessRightConfig1, /*!< Master access right */
.processIdentifier = 0x00U, /*!< Process identifier */
.processIdMask = 0x00U /*!< Process identifier mask */
}
};
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello karnik.somani@acclivistechnologies.com,
The flash memory is not writable by the core itself but by the FTFC module.
The core can only write the FTFC registers and launch a command such as the Program Phrase command.
Flash protection can be used instead, please refer to the reference manual:
36.5.1 Flash protection.
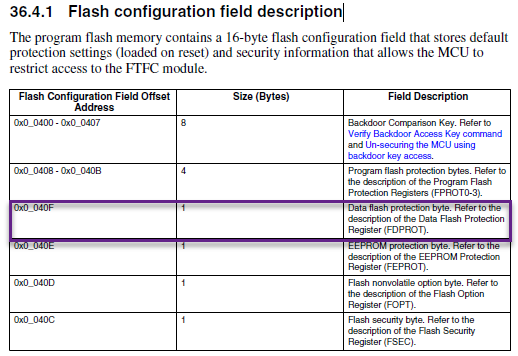
36.4.4.1.9 Data Flash Protection Register (FDPROT).
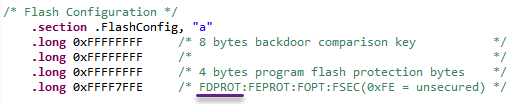
The FDPROT register is loaded from the flash configuration field during the reset sequence.
startup_S32K144.S
Regards,
Daniel
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Dear Daniel,
Thanks for the insight.
The application we are seeking is to lock and unlock flash region in during execution.
As from the RM it can be understood that write protection provided by flash protection module
is irreversible.i.e once write protect will stay until reset.
Is there any way we can protect flash memory via System MPU.
Is it possible to use Arm provided MPU?
Regards,
Karnik
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello Karnik,
I’m sorry for the delayed response.
The Arm M4 core version in this family does not integrate the Arm Core MPU.
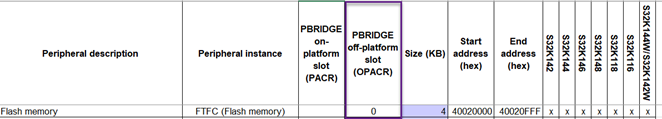
One possibility is to write-protect the FTFC registers when needed.
The peripherals (including FTFC) cannot be protected by the MPU but the Bridge provides some protection.
S32K1xx_Memory_Map.xlsx
You can therefore write-protect the FTFC module in the AIPS_OPACRA[WP0] register.
Regards,
Daniel
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Thanks for the support Daniel.