- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- ソフトウェア・フォーラム
- :
- S32 デザインスタジオ
- :
- CAN-RAppID bootloader
CAN-RAppID bootloader
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
CAN-RAppID bootloader
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I'm using the MPC5744P dev board, and the most updated bootloader version 'MPC5744P_S32DS_UART1_CAN0.rbf'
I succeed to flash an srec file using RAppID BL through CAN protocol. However, the application didn't start. The erase and flashing processes were successful and at the end of programming session, the BL wrote ''start application'' which means that the programming is conducted successfully. The problem seems to be where the start address of the application code is. If so, where should the application code start?
Thank you very much in advance
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello,
Please make sure your application project has all the required fields implemented. (See the RappID bootloader user guide / release notes document for more details)
Size Offset Value Description
(bytes) (bytes)
----- ------ ------- -----------
4 0 0x0000005A RCHW
4 4 Address Address of start of application
4 8 Delay Delay in micro seconds before bootloader launches
application on powerup
4 12 Appkey addr The location of application key. The application
key value should be 0x55AA55AAThis block should be placed at an address searchable by bootloader.
Note: For the appkey you should define constant in your app (ideally place it at the end of the flash image - define section .appkey) and pass just address to this constant in the block above.
const volatile uint32_t APPKEY __attribute__ ((section(".appkey"))) = 0x55AA55AA;Hope it helps.
Stan
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
I made sure about these fields and it didn't work
what are the searchable blocks by the bootloader ?
Could you please send me a srec file??
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
To start the application, the bootloader expects following boot header information to be present at the start location of any of the small, medium or large blocks other than block occupied by bootloader.
So for MPC5744P you could plce the boot header at address 0x00FA0000.
Attached is adjusted "Hello World" example that could be loaded using RAppID bootloader.
Hope it helps.
Stan
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Really thank you for your response
but the problem is still the same.
the srec file was flashed successfully and the bootloader started the application. however, the kit didn't respond. the red led shall be on but that didn't happen.
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Since you have devkit -> could you possibly try to attach to running target (Hello World project) after you program srec using OpenSDA debugger? this will help to figure out where the execution is.
Go to project Launch configurtation and select "attach to running target" and press debug button.
Once the debugger connection is established, press Suspend/Pause debug button.
Can you send us the screenshot of disassembly when you pause the execution?
Stan
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hello Stan, I Hope your day is fine
Here is the disassembly screenshot
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi
it seems that an unhandled exception occurred -> the address space belongs to Boot assist module - rom code executed after reset.
Which DevKit board revision do you use? what is the jumper settings?
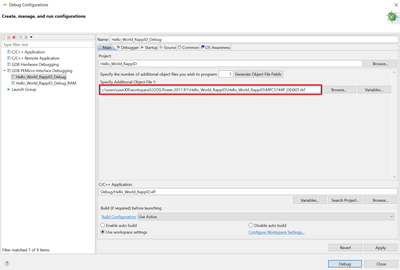
I'd suggest you to debug Hello World Rappid project (FYI: it should loads also program the bootloader - just update the absolute path to rbf file)
then put a breakpoint at app _start() and perform reset target from the debugger (see screenshot below)
Now run the execution -> do you hit the breakpoint?
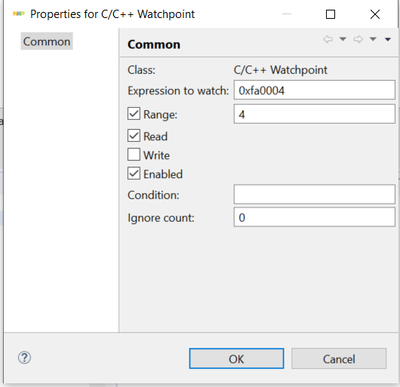
If not, please add read watchpoint to address 0xfa0004 (bootloader rchw block - app entry point) and reset from debugger. Do you hit the watchpoint?
Regards,
Stan
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi stan
Hope you are well
My Dev board is of revision E.
Jumper settings: debug mode, FAB pin is disconnected
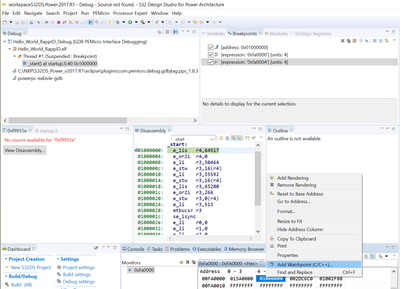
when I put a breakpoint at app _start() and perform reset target from the debugger, I didnot hit the breakpoint. the kit enters signal trap as follows,
when I read a watchpoint to address 0xfa0004, I got the following
then I reset from debugger, I got the following