- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- Product Forums
- :
- MPC5xxx
- :
- Re: CSE2 (MPC5777C) : Key Storage address space query?
CSE2 (MPC5777C) : Key Storage address space query?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CSE2 (MPC5777C) : Key Storage address space query?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Team NXP,
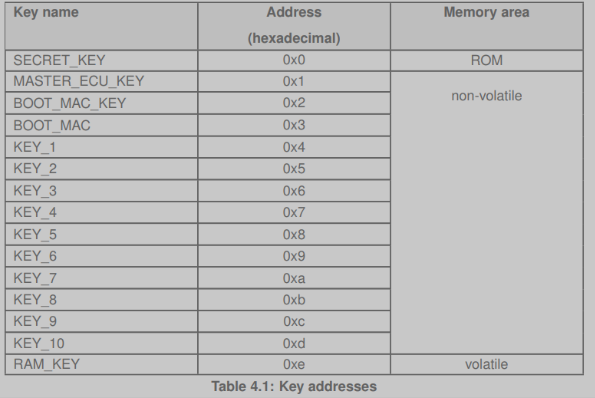
1) As per MPC5777C TRM manual, the memory map of CSE Flash is as below:
- Block-0 : 0x0060_0000 to 0x0060_3FFFF (16 KB) for CSE
- Block-1 : 0x0060_4000 to 0x0060_7FFFF (16 KB) for CSE
2) And I'm aware that followings keys makes in to those flash areas based on particular use case:
3) QUERY :
- a) I'm unable to find, Key_Wise_Memory_Slot Indication in the manual
- b) So, Can I conclude that: As developer, we have to make a 'KEY memory occupation layout' with in the address space mentioned in the point-1 ?
- c) Else, where does the NXP Flashed keys are pre-stored with in this space.
Request: Please throw relevant pointer addressing the above issues and correct me if I'm wrong in making above assumption. (Regarding the key storage layout and addresses particular to each key)
- Also, What is the rationale in giving 2-CSE Blocks (B1, B2) in flash as indicated in point-1.
- Awaiting your quick response. : )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
all the MPC5777C devices are shipped with CSE enabled. That means CSE has exclusive access to those flash blocks. Other masters are not allowed to access this memory – bus error will be triggered on such attempt.
The keys are not loaded to that flash directly. It must be done by memory update protocol defined by SHE spec. See this application note for more details. There are code examples in Appendix A:
https://www.nxp.com/webapp/Download?colCode=AN5418
Then there are application notes written for MPC5646C which has CSE module (there’s CSE2 on MPC5777C). This could also help:
https://www.nxp.com/docs/en/application-note/AN4234.pdf
https://www.nxp.com/docs/en/application-note-software/AN4234SW.zip
https://www.nxp.com/docs/en/application-note-software/AN4234video.zip
https://www.nxp.com/docs/en/application-note/AN4235.pdf
https://www.nxp.com/docs/en/application-note-software/AN4235SW.zip
https://www.nxp.com/docs/en/application-note-software/AN4235video.zip
Regards,
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas & Team NXP,
Thanks for the quick response. The content is really helpful and I went through them in keen.
We need your help on following Query.
- I have started testing CSE2 for :
a) GET_ID, [Result (CMD Error code) :- "System Memory Error")]
b) LOAD_PLAIN_KEY [Result (CMD Error code) :- "System Memory Error")]
c) ENCRYPT, DECRYPT using the loaded PLAIN_RAM_KEY. [Result (CMD Error code) :- "Empty Key")]
Query :
1) Does updating RAM_KEY using LOAD_PLAIN_KEY command has any dependency on the Success of SECURE_BOOT ? (Parallel Secure boot anyway fails in our case as its not of our interest)
- (Please note that SECURE_BOOT is not of our interest but only ENCRY, DECRY using PLAIN_RAM_KEY)
Attachment (Issue description) : Please go through attachment for issue or query details.
Your quick response as always is much appreciated and thanks in advance. lukaszadrapa csec; ram_key cse2 cse crypto services engine crypto #she
Thanks & Regards,
J.G Lakshmi Kanth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lakshmi,
it looks like you didn't initialize the CSE. Let me copy here two parts of the AN5418:
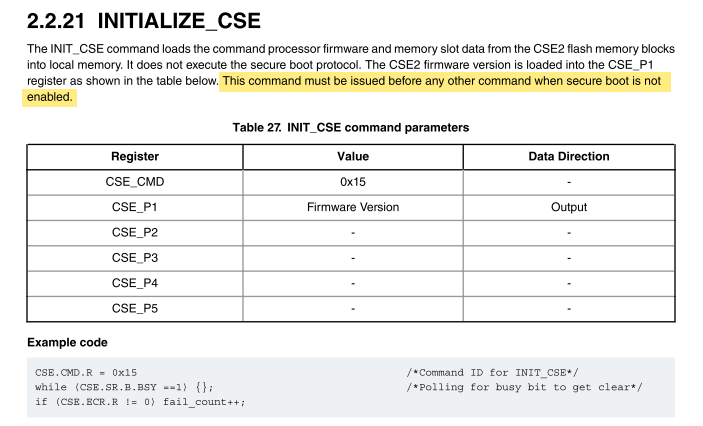
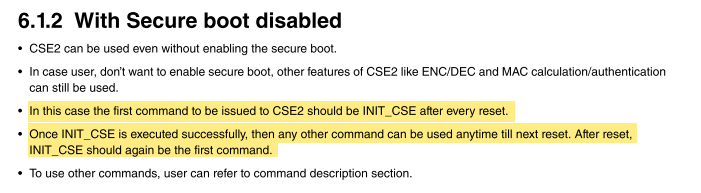
By the way, secure boot is not enabled by default. Read "6.1.1 With secure boot enabled" in the application note.
Regards,
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas,
Thanks for the reply.
Firstly I forgot to mention that : I've already executed the above mentioned test case i.e :
- First performed: INIT_CSE (Called after Mcu_Init in the main before using any CSE Services).
(Result : "CMD Sequence Error" stored in : CSE Error Code Register (CSE_ECR).
Observation : By observing "CMD Seq Error - 0x02" description, Point(3) says clearly that :
- [3. SECURE_BOOT or INIT_CSE command issued after an initial SECURE_BOOT or INIT_CSE is issued.]
Inference: So, as per the above texts, it is clear that: INIT_CSE is not required as "SECURE_BOOT" command is already enabled by default and CSE_Internal Firmware would have issued the SECURE_BOOT command internally.
Context of Test Execution:
- "CSE2 enabled by default settings at power-up in Parallel SECURE_BOOT mode for by NXPs default setting" (No changes made by us in this regard - Internal Flash Boot)
- "Also, NO KEYS Flashed before as SECURE_BOOT is not our interest and hence its expected to fail obviously (No MASTER_ECU_KEY nor BOOT_MAC_KEY available".
- This is the context in which we are trying to either INIT_CSE (Cmd Seq Error), Get UID (System Memory Error), ENCRYPT & DECRYPT (key empty) error gets registered in "Error Code Summary".
Queries : (At main() function : "CSE_ECR -> No Secure Boot" as BOOT_MAC_KEY not available and that's fine)
1) If SECURE_BOOT Fails, does it mean using even "GET_ID" & "LOAD_PLAIN_KEY" basic functionalities are restricted or having a sort of dependency.
2) INIT_CSE fails saying : Cmd Seq Error (Gives assumption, SECURE_BOOT is internally issues during SECURE_PARALLEL Boot). Is this assumption right?
3) Is it required to carryout SECURE_FALSH ERASE at-least once to even use GET_ID or LOAD_PLAIN_KEY ?
4) What is the checklist to ensure there won't be any issues w.r.t : CSE FLASH Accesses or CSE SYSTEM Memory related errors?
5) Do you suggest me to DISABLE SECURE_BOOT using DCF and use CSE functions directly?
6) Is issuing BOOT_OK Command can solve the side effects of query asked at '(1)' ?
Request for your kind co-operation in knowing the root-cause ASAP as we have some prototype demonstration very soon.
Thanks for help so far.
Regard,
Lakshmi Kanth, Senior Research Engineer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I did quick test on my board and I can see it's also necessary to initialize TRNG. My minimalist code is (reused from AN5418):
// Setting the divider value
//CSE.CR.B.DIV = ---- set as needed to achieve clock 500kHz - 2MHz
// Initializing TRNG
CSE.CMD.R = 0x0A; /*Command ID for INIT_TRNG*/
while (CSE.SR.B.BSY ==1) {}; /*Polling for busy bit to get clear*/
while(CSE.SR.B.RIN==0) {}; /*Polling RIN flag to get set*/
if (CSE.ECR.R != 0) fail_count++;
char get_id_challenge[16] = {0xE6,0xFE,0x09,0x7D,0xBC,0x72,0x3E,0x2C ,0xF0,0xEA, 0x41,0x6F,0xE6,0x8A,0xD3,0x3E}; /* user selects these values*/
vuint32_t GET_ID_UID [4];
vuint32_t UID_MAC [4];
CSE.P[0].R = (vuint32_t) & get_id_challenge; /*Pointer to ID challenge*/
CSE.P[1].R = (vuint32_t) & GET_ID_UID; /*Pointer to location, UID to be stored at*/
CSE.P[2].R = 0;
CSE.P[3].R = (vuint32_t) & UID_MAC; /*Pointer to location, MAC to be stored at*/
CSE.CMD.R = 0x10; /*Command ID of GET_ID */
while (CSE.SR.B.BSY ==1) {}; /*Polling for busy bit to get clear*/
if (CSE.ECR.R != 0) fail_count++;
This is working on my side, I'm able to get the ID. It's brand new device, I didn't do other initialization.
Could you give this a try?
Regards,
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas,
If possible, please send the 'example project' for MPC5777C used for setting up the required environment for CSE2 to RUN. (Low level files)
Thanks in advance. :smileyhappy: lukaszadrapa #cse2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
just sharing test project in a hurry. This works on my side, I can get random number and ID.
Regards,
Lukas
“Any support, information, and technology (“Materials”) provided by NXP are provided AS IS, without any warranty express or implied, and
NXP disclaims all direct and indirect liability and damages in connection with the Material to the maximum extent permitted by the applicable
law. NXP accepts no liability for any assistance with applications or product design. Materials may only be used in connection with NXP
products. Any feedback provided to NXP regarding the Materials may be used by NXP without restriction.”
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mr.Lukas,
I'm sorry to say that we use GHS compiler and not the GCC environment.
Please refer me to an article which can help me migrate the GCC based project to GHS environment (Or) please share GHS based project if having.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
you can simply copy the code from main.c. I didn't modify more files. Please confirm if this code is working on your side.
Regards,
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas,
The code works fine. (Thank you)
what is surprising is that we don't know if the CHALLENGE_VALUE for GET_UID command is a random or a derived one. We were using CHALLENGE_ID from one of previous application notes and that was creating the problem it seems. When we changed CHALLENGE as per recent application note, its working.
Anyways, thanks a lot for the effort you've put so far Mr. Lukas. It was a silly thing that was causing the problem. :smileyhappy:
(Challenge value selection for GET_UID is still a Gray area for us).
Thanks & Regards,
Lakshmi Kanth,
Senior Research Engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lakshmi,
nice to hear it works!
Generally, challenge value is a random value:
Challenge–response authentication - Wikipedia
In case of GET_UID, it's possible to use either constant value (as shown in AN5418) or random value. It depends on your needs. The command returns signature - MAC value calculated over challenge value, status register and ID. MASTER_ECU_KEY is used.
Regards,
Lukas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas,
Yaa. It works with Random Selection of CHALLENGE_VALUES.
Thanks & Regards,
J.G Lakshmi Kanth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas,
Here is the "TEST RESULT" as per your suggestion: (On MCU is MPC5777C)
1) Only Progress: Only TRNG_INIT CMD is successful. (i.e. RIN Flag set and No ERC (Error Code generated))
2) Immediately GET_ID is called. (Result : Same as before : "System Memory Error".
3) Followed by : LOAD_PLAIN_KEY (Result : "System Memory Error").
4) Then, ENCRY, DECRY CMDs leads to : "Key Slot Empty" as LOAD_PLAIN_KEY failed already.
I have few known facts & assumptions regarding the issue:
- [Fact-1]: DCF record corresponding the SECURE_BOOT is OTP and written by NXP already and cannot be overwritten.
- This concludes : CSE2 is always enabled
- SEC_BOOT always enabled in Parallel Mode. (No control to user over this part).
- [Fact-2] : MPC5777C Manual says: MPU is auto configured by default to set CSE2 free from interference from other masters. (- Conclusion made : So, user need not change MPU settings is the assumption made).
- [Fact-3] After MCU_Init & Clock distribution, the CSE2 shows SECURE_BOOT as last processed CMD with failures: (Secure boot is assumed to fail as BOOT_MAC_KEY is not yet programmed and hence ok to fail.
a) BOK : Secure Boot Not Completed or Failed
b) BFN : Secure Boot Not Finised
c) BIN : Secure Boot Personalization not finised.
d) SB : Secure Boot Not Completed.
- [Assumption-1] : Because of FACT-1 i.e SEC_BOOT enabled by default on MCU by NXP, we assume SECURE_BOOT command is issued automatically to the CSE at POWER_ON and CSE2 is loaded with the Firmware from the SECURE_FLASH to CSE2 local memory.
- Conclusion of Assumption-1 : We assume "CSE Firmware loading" is failed and we are not sure of how to check that thing.
-[Actions being taken]
- PASS, TDM & FMC55 modules are being checked to see if any locks are applied on SECURE_FLASH memory for CSE2 engine to access. (Please correct me if any-assumption is wrong). Also, do you think MPU has control over FLASH access too as I assume its only control over RAM area.
"Hoping for your quick response as usual Lukas".
lukaszadrapa #cse2 #crypto #mpc5777c
Thanks & Regard,
J.G Lakshmi Kanth