- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- QorIQ处理平台
- :
- Layerscape
- :
- Re: u-boot signing process
u-boot signing process
u-boot signing process
Hi,
ls1088a rdb, sd boot mode.
I based on Layerscape Linux Distribution POC User Guide Rev. L5.15.71-2.2.0 — 17 February 2023
Could you please describe how I can sign u-boot binaries manually?
I generate bl2_sd.pbl and fip_uboot.bin (as well as rcw_1600_sd.rcw [without SB_EN =1], rcw_1600_sd.bin and u-boot.bin) due to bitbake qoriq-atf. I know that can generate it as secure, but I need to do it manually.
As far as I know, for it the uni_sign is used, but I don't understand what is flow.
Am I correct?
- ./gen_keys 2048
- ./uni_sign --hash input_files/uni_sign/ls2088_1088/sd/input_uboot_secure (to take key.pub hash, the pub key should be in the CST dir)
- cp u-boot.bin to the CST dir
- ./uni_sign input_files/uni_sign/ls2088_1088/sd/input_uboot_secure (to sing u-boot)
The input file for both hash and u-boot signing
/* Copyright (c) 2015 Freescale Semiconductor, Inc.
*/
ESBC=1
---------------------------------------------------
# Specify the platform. [Mandatory]
# Choose Platform -
# TRUST 3.0: LS2085
# TRUST 3.1: LS2088, LS1088
PLATFORM=LS1088
---------------------------------------------------
# Entry Point/Image start address field in the header.[Mandatory]
# (default=ADDRESS of first file specified in images)
# Address can be 64 bit
ENTRY_POINT=80400000
---------------------------------------------------
# Specify the Key Information.
# PUB_KEY [Mandatory] Comma Seperated List
# Usage: <srk1.pub> <srk2.pub> .....
PUB_KEY=srk.pub
# KEY_SELECT [Mandatory]
# USAGE (for TRUST 3.x): (between 1 to
KEY_SELECT=1
# PRI_KEY [Mandatory] Single Key Used for Signing
# USAGE: <srk.pri>
PRI_KEY=srk.pri
---------------------------------------------------
# Specify IMAGE, Max 8 images are possible.
# DST_ADDR is required only for Non-PBL Platform. [Mandatory]
# USAGE : IMAGE_NO = {IMAGE_NAME, SRC_ADDR, DST_ADDR}
# Address can be 64 bit
IMAGE_1={u-boot.bin,80400000,ffffffff}
IMAGE_2={,,}
IMAGE_3={,,}
IMAGE_4={,,}
IMAGE_5={,,}
IMAGE_6={,,}
IMAGE_7={,,}
IMAGE_8={,,}
---------------------------------------------------
# Specify OEM AND FSL ID to be populated in header. [Optional]
# e.g FSL_UID_0=11111111
FSL_UID_0=
FSL_UID_1=
OEM_UID_0=
OEM_UID_1=
OEM_UID_2=
OEM_UID_3=
OEM_UID_4=
---------------------------------------------------
# Specify the output file names [Optional].
# Default Values chosen in Tool
OUTPUT_HDR_FILENAME=hdr_uboot.out
IMAGE_HASH_FILENAME=
RSA_SIGN_FILENAME=
---------------------------------------------------
# Specify The Flags. (0 or 1) - [Optional]
MP_FLAG=0
ISS_FLAG=1
LW_FLAG=0
---------------------------------------------------
# Specify VERBOSE as 1, if you want to Display Header Information [Optional]
VERBOSE=1
The u-boot.bin wasn't modified, but I got hdr_uboot.out.
- What should I do to sign normal u-boot?
- How can I sign the rcw.bin?
- Should I create pbl and fip before signing or I have to sign u-boot and rcw before creation pbl and fip?
Thanks a lot.
Thank you for contacting NXP support!
Follow these steps to compile and deploy TF-A binaries (bl2_.pbl) on the required boot mode.
- Compile PBL binary from RCW source file
- Compile U-Boot binary
- Compile TF-A binaries (bl2_.pbl and fip.bin)
1-COMPILE PBL BINARY FROM RCW SOURCE FILE
You have to create a new directory to compile the binaries that you need to create a TF-A binary
You need to compile the rcw_<boot_mode>.bin binary to build the bl2_<boot_mode>.pbl binary.
Clone the rcw repository and compile the PBL binary.
- $ git clone https://source.codeaurora.org/external/qoriq/qoriq-components/rcw
- $ cd rcw
- $ git checkout -b LSDK-21.08 LSDK-21.08
- $ cd <platform>
- If required, make changes to the rcw files.
- $ make
Inside of the directory called “RR_FQPP_1455” you can see some binaries in the with the next nomenclature:
rcw_<freq>.bin
Where “freq” is the frequency in MHz of the processor.
2-COMPILE U-BOOT BINARY
You need to compile the u-boot.bin binary to build the fip.bin binary.
Clone the u-boot repository and compile the U-Boot binary for TF-A
- $ git clone https://source.codeaurora.org/external/qoriq/qoriq-components/u-boot.git
- $ cd u-boot
- $ git checkout -b LSDK-21.08 LSDK-21.08
- $ export ARCH=arm64
- $ export CROSS_COMPILE=aarch64-linux-gnu-
- $ make distclean
- $ make <platform>_tfa_defconfig
- $ make
3 Compile TF-A binaries (bl2_.pbl and fip.bin)
- $ git clone https://source.codeaurora.org/external/qoriq/qoriq-components/atf
- $ cd atf
- $ git checkout -b LSDK-21.08 LSDK-21.08
- $ export ARCH=arm64
- $ export CROSS_COMPILE=aarch64-linux-gnu-
The compiled BL2 binaries, bl2.bin and bl2_<boot mode>.pbl are available at atf/build/<platform>/release/.
NOTE: For any update in the BL2 source code or RCW binary, the bl2_<boot mode>.pbl binary needs to be recompiled.
3.1 HOW TO COMPILE BL2 BINARY
To build BL2 binary with OPTEE, run this command:
$ make PLAT=<platform> bl2 SPD=opteed BOOT_MODE=<boot_mode> BL32=<optee_binary> pbl RCW=<path_to_rcw_binary>/<rcw_binary_for_specific_boot_mode>
The compiled BL2 binaries, bl2.bin and bl2_<boot_mode>.pbl are available at atf/build/<platform>/release/. For any update in the BL2 source code or RCW binary, the bl2_<boot_mode>.pbl binary needs to be recompiled.
To compile the BL2 binary without OPTEE:
make PLAT=<platform> bl2 BOOT_MODE=<boot_mode> pbl RCW=<path_to_rcw_binary>/<rcw_binary_for_specific_boot_mode>
3.2 HOW TO COMPILE FIP BINARY
To build FIP binary with OPTEE and without trusted board boot, run this command:
$ make PLAT=<platform> fip BL33=<path_to_u-boot_binary>/u-boot.bin SPD=opteed BL32=<path_to_optee_binary>/tee.bin
To compile the FIP binary without OPTEE and without trusted board boot:
make PLAT=<platform> fip BL33=<path_to_u-boot_binary>/u-boot.bin
The compiled BL31 and FIP binaries, bl31.bin, fip.bin, are available at atf/build/<platform>/release/. For any update in
the BL31, BL32, or BL33 binaries, the fip.bin binary needs to be recompiled
Thank you, but unfortunately, it is not answer for my questions. All these steps I passed. I need to know how I can sign it .
That is a little example to signin images on LS1043ARDB.
Command to generate public/private key pair
./gen_keys SIZE NAME
SIZE refers to size of public key in bits. (Modulus size).
Sizes supported -- 1024, 2048, 4096. The generated keys are in PEM format.
../cst/gen_keys 1024 -p srk.pri -k srk.pub
===============================================================
This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit
This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)
===============================================================
Generated SRK pair stored in :
PUBLIC KEY srk.pub
PRIVATE KEY srk.pri
The gen_otpmk utility in the Code Signing Tool can be used to generate a 256b random number and insert the hamming code, or simply perform the hamming code insertion for a user defined 256b.
>./gen_otpmk --help
Usage: ./gen_otpmk <trust_arch> [string]
string : 32 byte string
e.g. gen_otpmk 1 1111111122222222333333334444444455555555666666667777777788888888
>./gen_otpmk 2 1111111122222222333333334444444455555555666666667777777788888888
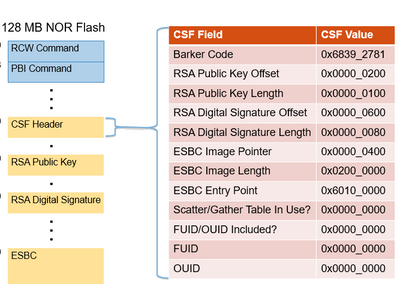
Code Signing Commands for Images: Create CSF Header
Ls -l input_files/uni_sign/ls1043
total 12
-rw-rw-r-- 3 user_lab user_lab 3490 Jan 27 00:34 input_bootscript_secure
-rw-rw-r-- 3 user_lab user_lab 3537 Jan 27 00:34 input_kernel_secure
-rw-rw-r-- 3 user_lab user_lab 3604 Jan 27 00:34 input_uboot_nor_secure
u-boot Image
./input_files/uni_sign/ls1043/input_uboot_nor_secure
The input fields are specified in input_uboot_secure file. Please ensure that the filename mentioned in the input_uboot_secure is same as copied in the cst directory.
Linux Kernel and Root file system
./input_files/uni_sign/ls1043/input_kernel_secure
kernel-fsl-ls1043a-rdb.dtb-ls1043ardb.itb would be validated form u-boot. The flash address used here is according to the address map of u-boot. Please ensure that filename mentioned in the input_uimage_secure is same as copied in the cst directory.
Boot Script
./input_files/uni_sign/ls1043/input_bootscript_secure
Please make sure that filename mentioned in the bootscript is same as copied in the cst directory
Sign the image with CST tools
$ cd /home/user_lab/Linux-LS1043A-SDK-V0.4-20150826-yocto-RDS-20151209/build_ls1043ardb_release/tmp/sysroots/x86_64-linux/usr/bin/cst
$ ll input_files/uni_sign/ls1043
total 12
-rw-rw-r-- 3 user_lab user_lab 3490 Jan 12 08:27 input_bootscript_secure
-rw-rw-r-- 3 user_lab user_lab 3537 Jan 12 08:27 input_kernel_secure
-rw-rw-r-- 3 user_lab user_lab 3604 Jan 12 08:27 input_uboot_nor_secure
$ vi input_files/uni_sign/ls1043/input_kernel_secure
Modify “IMAGE_1={kernel-fsl-ls1043a-rdb.dtb-ls1043ardb.itb,81000000,ffffffff}”
$ vi input_files/uni_sign/ls1043/input_uboot_nor_secure
Modify “IMAGE_1={u-boot-ls1043ardb.bin,60100000,ffffffff}”
$ vi input_files/uni_sign/ls1043/input_bootscript_secure
Note: bootscript is used when you have chain of trust.
CST tool generates the following SHA-256 hash in a binary hash of hex bytes, not string hash of text!
$./uni_sign --hash input_uboot_secure
./uni_sign --hash input_files/uni_sign/ls1043/input_uboot_nor_secure
We have some documents that maybe can be useful, please open a case mentioning me following the link:
you must have a valid NDA to receive that files.
Thank you for your answer. It is really very helpful information.
1. ./gen_otpmk 2 generates OTPMK fuse values. The "2" means that target platform is big-endian one. As far as I know, I must swap this values before fusing because I use a little-endian host machine to generate it. Am I correct?
2. Same with SRKH values. Please confirm it.
3. What should I do with RCW?
3.1 How can I sign it?
3.2 Do I have to sign it before creating .pbl or after?
4.1 FIP file consists at least from BL31 and BL33 (u-boot). Is u-boot signed before creating FIP?
4.2 Where can I get signed by my key BL31?
Thanks a lot for your help!
For RCW should be the same direction for cf the sign it is at the same time as u-boot.bin.
The BL31 is signed on fip.bin in that contains bl31 and bl33.
This is the map for the RCW sign.
We have a very explained tutorial for LS1043 but I can't publish that file here, please open a case following the link and mention my name on the case to provide you with the file.