- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- 通用微控制器
- :
- Kinetis微控制器
- :
- How to trigger mass erase on somehow locked K32L2A device
How to trigger mass erase on somehow locked K32L2A device
Hi,
Due to bad flashing I ended with somehow locked K32L2A device. I am using mcuxpresso with mcu-link probe. New program can not be downloaded, but memory can be read, and here is protection related part ...
Device can not be unlocked / mass erased by mcuxpresso flash tool.
It is very strange to me that mcuxpresso doesn't check for operation success (or I don't know where the right checkbox is). After program is download to device there is no automatic verify, so user think that everything is OK. Same for erase or unlock because result of all this operations is OK (green / blue). Only if dedicate verify against file is executed than will be reported error (red).
已解决! 转到解答。
I unlocked device by triggering mass erase with writing right value (mass erase under reset, because reset pin was disabled) to MDM-AP control register. I started once with development of my own hardware / software SWD tool (never finished), so used this because didn't found anything for low level SWD operations by CMSIS-DAP using MCU-Link.
; Select MDM-AP control reg
SWD_REG_WRITE DP_RESEND_SELECT, ((001h << 24) | (001h << 2))
; Set BIT3 to force a system reset. Set BIT0 to cause mass erase.
SWD_REG_WRITE_AD AP_DRW, (BIT3 | BIT0)
I really don't understand why this is not covered by mass erase in MCUXpresso.
EDIT:
After device was unlocked I found note inside device reference manual (9.4.1 MDM-AP Control Register) related to my case. It was in front of my eyes all the time, but I didn't see it.
I am not sure if solution by Erich Styger using j-link should help in my case. Because here ...
https://wiki.segger.com/Kinetis_Series_Devices
there is ...
It is mandatory to connect the reset pin of the Kinetis devices to J-Link. Otherwise, proper functionality and a stable connection cannot be guaranteed.
Note: The Kinetis manuals advertise that a reset can also be issued via the MDM-AP, so no pin is required. However, this way is unreliable and does not work properly when trying to unsecure a secured device.
... and on my device reset pin was disabled.
Hello @jh0 ,
Please follow the next guide, on the section Unlocking and Erasing with J-Link Commander.
Unlocking and Erasing with J-Link Commander
Also let me know any error message (in case of it) if it works also let me know.
Hi @nxf77486,
Unfortunately I don't have Segger probe. AFAIK only MCU-Link Pro can be used as J-Link probe with Segger firmware. MCU-Link non-Pro can't, even Segger firmware can be found inside MCU-Link non-Pro driver pack.
Here is log from MCUXpresso with mass erase executed (with reset target checked) and message that part is not secured (I hope so, that only flash is) ...
Executing flash operation 'Erase' (Erase flash) - Tue Oct 12 22:03:17 CEST 2021
Checking MCU info...
Scanning for targets...
Executing flash action...
MCUXpresso IDE RedlinkMulti Driver v11.4 (Jul 2 2021 12:03:47 - crt_emu_cm_redlink.exe build 1)
( 0) Reading remote configuration
Wc(03). No cache support.
Found chip XML file in D:/workspace/K32L2A31A_Project___/Debug\K32L2A31xxxxA.xml
( 5) Remote configuration complete
Reconnected to existing LinkServer process.
============= SCRIPT: kinetisconnect.scp =============
Kinetis Connect Script
Connecting to Probe Index = 1
This probe = 1
This TAP = 0
This core = 0
DpID = 2BA01477
Assert NRESET
Reset pin state: 01
Power up Debug
MDM-AP APID: 0x001C0020
MDM-AP System Reset/Hold Reset/Debug Request
MDM-AP Control: 0x0000001C
MDM-AP Status (Flash Ready) : 0x008801B2
Part is not secured
MDM-AP Control: 0x00000014
Release NRESET
Reset pin state: 01
MDM-AP Control (Debug Request): 0x00000004
MDM-AP Status: 0x008901BA
MDM-AP Core Halted
============= END SCRIPT =============================
Probe Firmware: MCU-LINK (r0FF) CMSIS-DAP V2.245 (NXP Semiconductors)
Serial Number: XXXXXXXXXX
VID:PID: 1FC9:0143
USB Path: \\?\hid#vid_1fc9&pid_0143&mi_00#7&29063fc9&0&0000#{4d1e55b2-f16f-11cf-88cb-001111000030}
Using memory from core 0 after searching for a good core
On debug connection - reset using system reset
( 30) Emulator Connected
( 40) Debug Halt
( 50) CPU ID
debug interface type = CoreSight DP (DAP DP ID 2BA01477) over SWD TAP 0
processor type = Cortex-M0+ (CPU ID 00000C60) on DAP AP 0
number of h/w breakpoints = 2
number of flash patches = 0
number of h/w watchpoints = 2
Probe(0): Connected&Reset. DpID: 2BA01477. CpuID: 00000C60. Info: <None>
Debug protocol: SWD. RTCK: Disabled. Vector catch: Enabled.
Content of CoreSight Debug ROM(s):
RBASE F0002000: CID B105100D PID 000008E000 ROM (type 0x1)
ROM 1 F0000000: CID B105900D PID 04001BB932 CSt ARM MTB type 0x31 Trace Sink - Basic trace router
ROM 1 F0001000: CID B105900D PID 000008E000 CSt MTBDWT type 0x4 Debug Control - Other
ROM 1 F0006000: CID B105900D PID 04000BB9A6 CSt ARM CTIv2 type 0x14 Debug Control - Trigger, e.g. ECT
ROM 1 E00FF000: CID B105100D PID 04000BB4C0 ROM (type 0x1)
ROM 5 E000E000: CID B105E00D PID 04000BB008 Gen SCS (type 0x0)
ROM 5 E0001000: CID B105E00D PID 04000BB00A Gen DWT (type 0x0)
ROM 5 E0002000: CID B105E00D PID 04000BB00B Gen FPB (type 0x0)
NXP: K32L2A31xxxxA
DAP stride is 1024 bytes (256 words)
Inspected v.2 On chip Kinetis Flash memory module K32L2A.cfx
Image 'Kinetis K32L Jul 12 2021 22:06:17'
Opening flash driver K32L2A.cfx
Sending VECTRESET to run flash driver
Flash variant 'K32L2B FTFA 2K' detected (256KB = 128*2K at 0x0)
Closing flash driver K32L2A.cfx
( 65) Chip Setup Complete
Connected: was_reset=false. was_stopped=true
( 70) License Check Complete
Opening flash driver K32L2A.cfx (already resident)
Sending VECTRESET to run flash driver
Flash variant 'K32L2B FTFA 2K' detected (256KB = 128*2K at 0x0)
Mass Erase flash at 0x0
Closing flash driver K32L2A.cfx
MassErase completed (in 9ms)
Hello @jh0 ,
Can you please make a image memory dump in order to see the 0x400 memory section in order to discard any security.
Also please send me the command prompt of the error you are receiving in order to have more info.
Hi @nxf77486
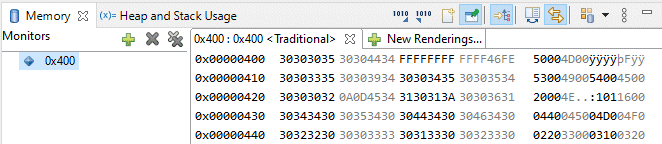
Here is 0x400 ...
If I decoded right ...
Backdoor key: 30 30 30 35 30 30 44 34
FPROT: FF FF FF FF flash is protected
reserved FF
reserved FF
FOPT: 46 0100 0110
BIT7-6: 01 Boot reserved BIT5: 0 Slow init BIT4,0: 00 VLPR mode
BIT3: 0 Reset pin disabled BIT2: 1 NMI enabled BIT1: 1 Boot source from BIT7-6
FSEC: FE 1111 1110
BIT7-6: 11 Backdoor key access disabled
BIT5-4: 11 Mass erase enabled
BIT3-2: 11 NXP factory access granted
BIT1-0: 10 MCU security status is unsecure
I know that flash does not change, because verify fail after mass erase or after program with unchanged flash memory contest starting from address zero and so on.
...
( 65) Chip Setup Complete
Connected: was_reset=true. was_stopped=true
( 70) License Check Complete
Verifying 'K32L2A31A_Project___.axf' ELF code section 0 at 0x00000000 len 0x35A0
Opening flash driver K32L2A.cfx (already resident)
Sending VECTRESET to run flash driver
Flash variant 'K32L2B FTFA 2K' detected (256KB = 128*2K at 0x0)
( 0) Comparing Flash against file at 0x00000000
Flash file verification failed at (at least) these memory addresses
@@@@00000000 - file 20018000 '... ' != flash 3038303A ':08
( 0) Comparing Flash against file at 0x00000004
@00000004 - file 00000135 '5...' != flash 30303030 '0000'
( 0) Comparing Flash against file at 0x00000008
@00000008 - file 000001A3 '....' != flash 38303030 '0008'
( 0) Comparing Flash against file at 0x0000000C
@0000000C - file 000006D1 '....' != flash 31464634 '4FF1'
( 0) Comparing Flash against file at 0x00000010
@00000010 - file 00000000 '....' != flash 34373946 'F974'
( 0) Comparing Flash against file at 0x00000014
@00000014 - file 00000000 '....' != flash 30303030 '0000'
( 0) Comparing Flash against file at 0x00000018
@00000018 - file 00000000 '....' != flash 0D463730 '07F.'
( 0) Comparing Flash against file at 0x0000001C
@0000001C - file DFFE7657 'Wv..' != flash 30313A0A '.:10'
( 0) Comparing Flash against file at 0x00000020
@00000020 - file 00000000 '....' != flash 30303430 '0400'
( 0) Comparing Flash against file at 0x00000024
@00000024 - file 00000000 '....' != flash 46463030 '00FF'
( 0) Comparing Flash against file at 0x00000028
@00000028 - file 00000000 '....' != flash 46464646 'FFFF'
( 0) Comparing Flash against file at 0x0000002C
@0000002C - file 000001A7 '....' != flash 46464646 'FFFF'
( 0) Comparing Flash against file at 0x00000030
@00000030 - file 00000000 '....' != flash 46464646 'FFFF'
( 0) Comparing Flash against file at 0x00000034
@00000034 - file 00000000 '....' != flash 46464646 'FFFF'
( 0) Comparing Flash against file at 0x00000038
@00000038 - file 000001A9 '....' != flash 46464646 'FFFF'
( 0) Comparing Flash against file at 0x0000003C
@0000003C - file 000001AB '....' != flash 45464646 'FFFE'
( 0) Comparing Flash against file at 0x00000040
@00000040 - file 000001AF '....' != flash 46464433 '3DFF'
( 0) Comparing Flash against file at 0x00000044
@00000044 - file 000001B7 '....' != flash 46424646 'FFBF'
( 0) Comparing Flash against file at 0x00000048
@00000048 - file 000001BF '....' != flash 313A0A0D '..:1'
( 0) Comparing Flash against file at 0x0000004C
@0000004C - file 000001C7 '....' != flash 30303130 '0100'
Closing flash driver K32L2A.cfx
(100) File matches flash.
Read 0x42D88 bytes in 3697ms (about 74kB/s) - verify FAILED
(100) Target Connection Failed
Unable to perform operation!
Command failed with exit code 1
I unlocked device by triggering mass erase with writing right value (mass erase under reset, because reset pin was disabled) to MDM-AP control register. I started once with development of my own hardware / software SWD tool (never finished), so used this because didn't found anything for low level SWD operations by CMSIS-DAP using MCU-Link.
; Select MDM-AP control reg
SWD_REG_WRITE DP_RESEND_SELECT, ((001h << 24) | (001h << 2))
; Set BIT3 to force a system reset. Set BIT0 to cause mass erase.
SWD_REG_WRITE_AD AP_DRW, (BIT3 | BIT0)
I really don't understand why this is not covered by mass erase in MCUXpresso.
EDIT:
After device was unlocked I found note inside device reference manual (9.4.1 MDM-AP Control Register) related to my case. It was in front of my eyes all the time, but I didn't see it.
I am not sure if solution by Erich Styger using j-link should help in my case. Because here ...
https://wiki.segger.com/Kinetis_Series_Devices
there is ...
It is mandatory to connect the reset pin of the Kinetis devices to J-Link. Otherwise, proper functionality and a stable connection cannot be guaranteed.
Note: The Kinetis manuals advertise that a reset can also be issued via the MDM-AP, so no pin is required. However, this way is unreliable and does not work properly when trying to unsecure a secured device.
... and on my device reset pin was disabled.