- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
I did execute the command to erase all via FTFC (0x44). Now i don't have any access to my microcontroller anymore.
1.) Is my understanding correct, that the command only starts erasing flash sectors when all sectors are unprotected?
2.) The content of the erased flash cells are 1, correct?
3.) When two is correct, the device should be in the secured state and the mase erase enable should be active, correct?
But I am not successful in executing a mass erase via Emergency Kinetes Device Recovery by Full Chip Erase. Did I locked out myself =(?
Best regards,
Tom
解決済! 解決策の投稿を見る。
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
I am not familiar with IAR, but I searched some information, could it be caused by this?
BR!
Jim,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Okay, thanks for your reply. I want to secure my device by changing the startup.s file in the following way:
__FlashConfig
DCD 0xFFFFFFFF ; 8 bytes backdoor comparison key
DCD 0xFFFFFFFF ;
DCD 0xFFFFFFFF ; 4 bytes program flash protection bytes
DCD 0xFFFF7FFF ; FDPROT:FEPROT:FOPT:FSEC(0xFE = unsecured)
__FlashConfig_EndBut this has no effect on the security status. I am wondering because this approach has worked for me in the past.
Best regards
Tom
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
IAR-> .sct
define symbol m_flash_config_start = 0x00000400;
define symbol m_flash_config_end = 0x0000040F;
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
Has it been resolved?
this is a configuration in the official routine.
startup_S32K142.S
/* Flash Configuration */
.section .FlashConfig, "a"
.long 0xFFFFFFFF /* 8 bytes backdoor comparison key */
.long 0xFFFFFFFF /* */
.long 0xFFFFFFFF /* 4 bytes program flash protection bytes */
.long 0xFFFF7FFE /* FDPROT:FEPROT:FOPT:FSEC(0xFE = unsecured) */
.text
.thumb.S32K142_32_flash.ld
.flash_config :
{
. = ALIGN(4);
KEEP(*(.FlashConfig)) /* Flash Configuration Field (FCF) */
. = ALIGN(4);
} > m_flash_config
Please let me know if you have any progress.
BR!
Jim,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Jim,
this is the content of my files. S32K142_32_flash.icf:
/* Flash */
define symbol m_interrupts_start = 0x00000000;
define symbol m_interrupts_end = 0x000003FF;
define symbol m_flash_config_start = 0x00000400;
define symbol m_flash_config_end = 0x0000040F;
define symbol m_text_start = 0x00000410;
define symbol m_text_end = 0x0003FFFF;startup_S32K142.s:
SECTION FlashConfig:CODE
__FlashConfig
DCD 0xFFFFFFFF ; 8 bytes backdoor comparison key
DCD 0xFFFFFFFF ;
DCD 0xFFFFFFFF ; 4 bytes program flash protection bytes
DCD 0xFFFF7FFE ; FDPROT:FEPROT:FOPT:FSEC(0xFE = unsecured)
__FlashConfig_EndI try to set the microcontroller in a secure state by this changes:
SECTION FlashConfig:CODE
__FlashConfig
DCD 0xFFFFFFFF ; 8 bytes backdoor comparison key
DCD 0xFFFFFFFF ;
DCD 0xFFFFFFFF ; 4 bytes program flash protection bytes
DCD 0xFFFF7FFF ; FDPROT:FEPROT:FOPT:FSEC(0xFE = unsecured)
__FlashConfig_EndBut as I said, this is not working.
Best regards
Tom
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
I am not familiar with IAR IDE, but the SEC settings should be correct.
I also tested it and it was OK to use PE Debugger, but it was not encrypted successfully when using J-LINK. After discussing with my colleagues, I thought it was the J-LINK debugger that unlocked it. I think the possible cause of the problem is caused by the debugger.
BR!
Jim,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Jim,
I'm also using a PE Debugger:
PE Micro Multilink Universal FX
Best regards
Tom
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
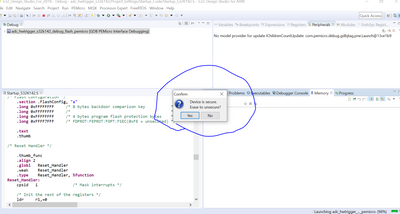
Hi@TomLightning
.S32K142EVB
.S32 Design Studio for ARM 2018 , SDK RTM3.0
.DEBUGER: OpenSDA ->PEmicro
I tested it again, as shown in the screenshot.
We are on vacation tomorrow. If you have a new question, I may not be able to answer you in time. I will return to the company on October 8, or you can ask a new question and my foreign colleague will help you answer it. Sorry for the inconvenience caused.
Have a nice weekend!
BR!
Jim,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi,
I have created a simple project by using the S32DS IDE and changed the startup file as mentioned above. Now the device is locked! So there must be a problem with my IAR EW ARM Project.
But it occurred a second problem. When the device is secured the following message pops up:
"Device is secure. Erase to unsecure?"
When I press "yes" the message pops up again. When I press "yes" again the debugger error window with the retry-button shows up. Then I need to start the process of debugging again. I need several attemps til the device gets erased and the software is downloaded on the chip. Do you have heard of such a behaivor before? Changing the debug probe does not help.
Best regards
Tom
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
I tested it, and I haven't encountered such a situation so far.
note:
If you select Yes, all downloaded programs will be erased, you need to select No to ensure that the program download is OK and the encryption is successful.
BR!
Jim,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
So, I have tried to modify the example hello_world_iar from the SDK so that the device should be in a secured state (I did the mentioned changes to the startup_S32K142.s). But that did not work either. Could you try to run the example with the IAR IDE to confirm that?
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
I am not familiar with IAR, but I searched some information, could it be caused by this?
BR!
Jim,
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi Jim,
yes, this little option has worked for me!
Thanks!
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi@TomLightning
please refers to this article.
https://www.nxp.com.cn/docs/en/application-note/AN12130.pdf
Erase all blocks is a flash command that performs a similar operation to the SWD mass erase, but the operations are not identical. Like mass erase, the erase all blocks command will erase all of the user flash contents that is, program flash, data flash, data flash IFR (including EEPROM partition configuration), EEPROM backup memory (E-flash), and FlexRAM. There are two important differences between mass erase and the erase all blocks command:
• Unlike mass erase, erase all blocks takes protection settings into account. If any flash or FlexRAM regions are protected, the erase all blocks command will abort.
• If the verify completes, erase all blocks will release security by setting the FTFC_FSEC[SEC] field to unsecured, but the security byte in the flash configuration field is not programmed to 0xFE. On a subsequent reset the processor will be in the secured state unless FSEC[SEC] in the flash configuration field is reprogrammed.
Q1.Is my understanding correct, that the command only starts erasing flash sectors when all sectors are unprotected?
A1.An erase is only possible when all memory locations are unprotected.
Q2.The content of the erased flash cells are 1, correct?
A2.Not all content ,like manual said ,
know more:
It is very similar to the security features of the Kinetis family MCUs. You can refer to AN4507 Using the Kinetis Security and Flash Protection Features
https://www.nxp.com/docs/en/application-note/AN4507.pdf
BR!
Jim,