- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- Software Forums
- :
- S32 Design Studio
- :
- Re: S32 Design Studio & Flash Mass erase
S32 Design Studio & Flash Mass erase
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
S32 Design Studio & Flash Mass erase
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do I perform a FLASH mass erase operation with s32k144 and s32 design studio? Can you describe me the precise steps to do that, without risking to brick my board as happened for other people, like here?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Based on the procedure of demo in AN12323.pdf, I don't think mass erase is able to remove partition. The only way to remove EEPROM partition is to do the partition again with suitable parameters. Otherwise, the SIM register for flash config will not be changed. Am I correct??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
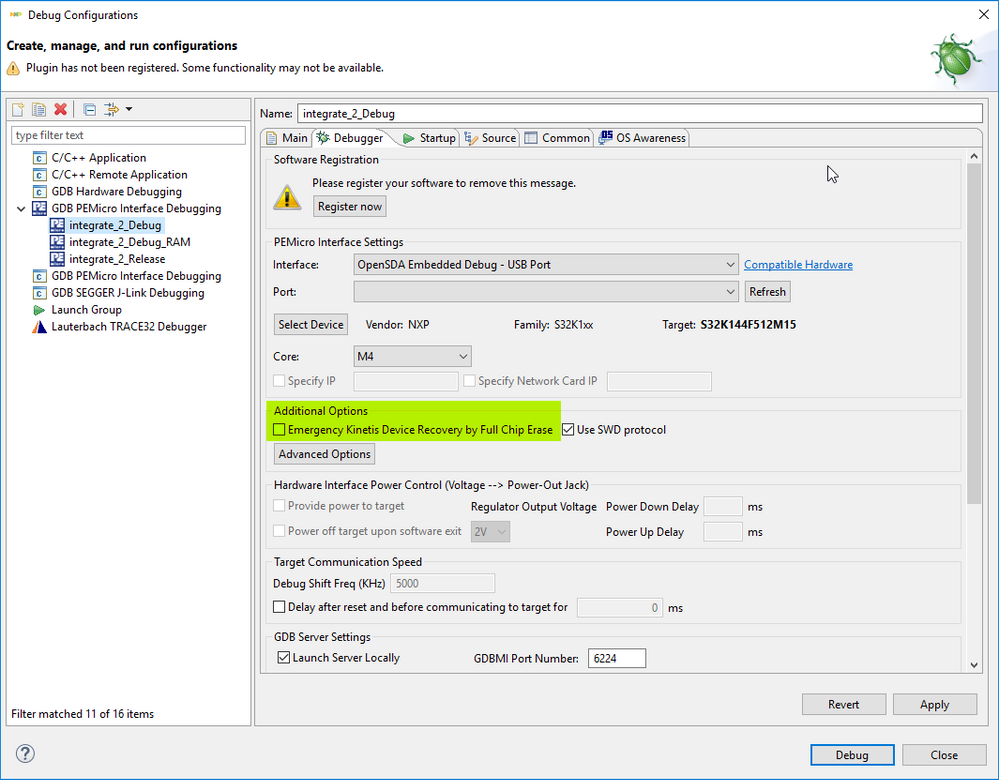
mass erase is performed prior new flash image write operation. You can also use Emergency kinetis device recovery in debug configuration.
When you are using FLASH operations by MCU - make sure that you aren't modify flash config on address 0x400-0x410. Erase of that area is okay, but make sure that you don't write there data which disable mass erase and secure the chip.
Jiri
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
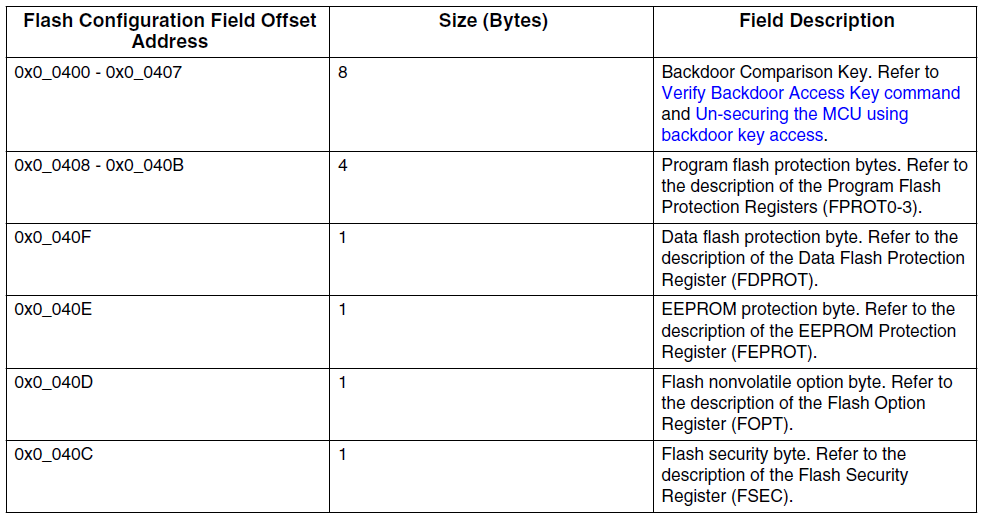
Ok, I understood that whenever I want to program/erase my s32k board, I must pay attention to not secure it, otherwise I could not be anymore able to re-program/re-erase it, if I do not have a backdoor key. The fields that I must pay attention to are in the following figure:
- The Backdoor Compartison Key is something similar to a password, that if known permits to unsecure the flash
- FPROT0-3 must be at 0xFF in order to not secure the P-Flash
- FDPROT must be at 0xFF in order to not secure the D-Flash
- FEPROT must be at 0xFF in order to not secure the E-Flash (i.e., the EEPROM backup memory)
- FOPT must be at 0xFF in order to not customize the boot options
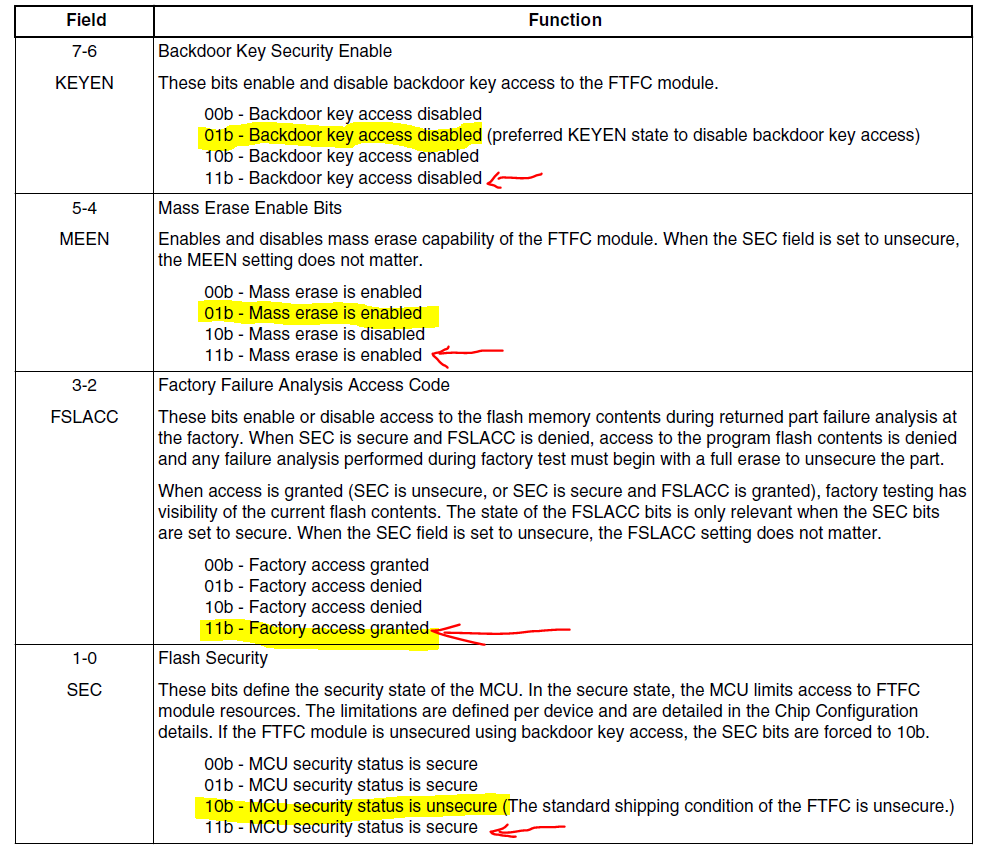
- FSEC is composed as following:
I highlighted in yellow what I want and in red what should happen when I perform a mass erase command (is it true that an erase command will put all flash bits at 1?). You said that an erase of this area is ok (i.e., the erase will not secure the device), even if the mass erase will write SEC = 11b (device is secure).
In the example provided with the SDK, after the erase of all flash blocks, the application will program the Flash Configuration Fields writing the following thing:
uint8_t unsecure_key[FTFx_PHRASE_SIZE] = {0xFFu, 0xFFu, 0xFFu, 0xFFu, 0xFEu, 0xFFu, 0xFFu, 0xFFu}
Where all bits are at 1, except for the FSEC[SEC] field that is at 10b.
So,
- How is it possible that when I upload a new application inside the S32K, even if it performs a mass erase operation, it will not secure the device?
- Does the mass erase operation remove the partitions of the FLASH memory resetting it to the "default" configuration? If yes, which is the default configuration?
- If the application residing in the P-Flash performs a mass erase operation, is the P-Flash not erased?
- I do not know how to use the Emergency Kinetis Device Recovery. What is it needed for? Why should I use it instead to perform my mass erase operation from inside the application?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
actually you need to take special care to MEEN bit, when mass erase is disabled, chip is secured and backdoor key disabled - there is no way back. Secured chip with mass erase enabled is okay.
Jiri
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, so when I erase all the flash content, SEC field secures the chip but the MEEN field leaves the mass erase operation enabled (thus, the example provided with the SDK maybe only wants to show how the flash configuration fields can be written).
What about question 2, 3 and 4? Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
2. the default config is using FlexNVM as Dflash
3. If app performs mass erase - the app erases itself too (at least partly - the program probably ends in some exception).
4. It is part of debug session with PE Micro debugger. I'm not 100% sure what this option does, but it can erase secured device with key access (jf MEEN is enabled).
Jiri