- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- Product Forums
- :
- S32K
- :
- command CMD_DBG_CHAL operation consultation
command CMD_DBG_CHAL operation consultation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
command CMD_DBG_CHAL operation consultation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
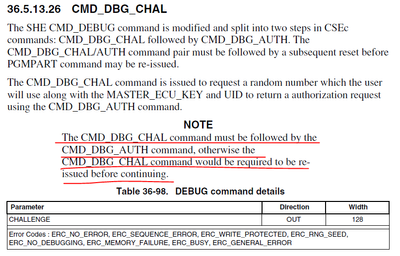
I saw the following description in the reference manual. Does the command CMD_DBG_CHAL have to be followed by the command COMD_DBG_AUTH? What will happen if other commands are executed between the two commands? At present, I dare not add it randomly. I am afraid that the chip will be locked up, so please consult your side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
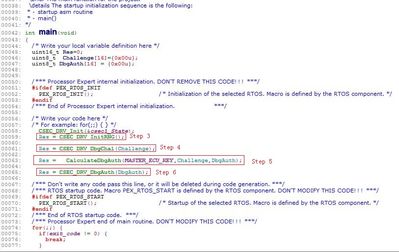
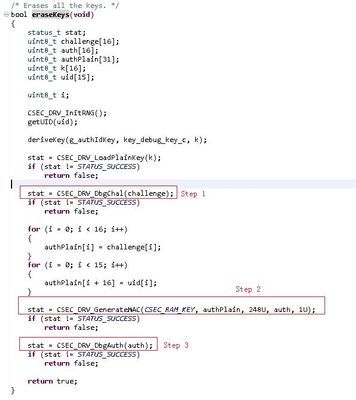
In the following sample code, there are other commands executed in step 5. Why?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @584914019,
Step 5 is needed to calculate the authorization.
Please see function DBG_AUTH() in AN5401, example 5.
Or you can use the SDK driver, example: csec_keyconfig_s32k144 function eraseKeys().
Regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
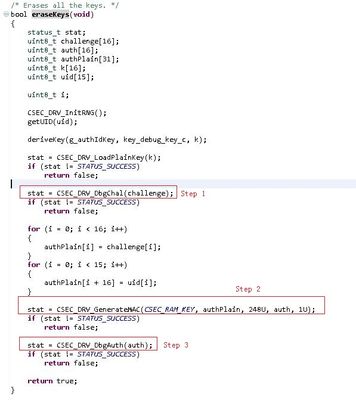
In the csec_keyconfig_s32k146 function deleteKeys(), you can see that CMD_DBG_CHAL() and CMD_DBG_AUTH have other commands CMD_GENERATE_MAC, as shown in step 2 in the figure below,Does the "CMD_DBG_CHA" command have to be followed by the command "CMD_DBG_AUTH"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Yes, the CMD_DBG_CHAL command must be followed by the CMD_DBG_AUTH command, otherwise the CMD_DBG_CHAL
command would be required to be reissued before continuing.
Please refer to AN5401 Getting Started with CSEc Security Module
4.5 Resetting Flash to the Factory State
AN5401SW.zip Example 5, Resetting flash to the factory state
Regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the csec_keyconfig_s32k146 function deleteKeys(), you can see that CMD_DBG_CHAL() and CMD_DBG_AUTH have other commands CMD_GENERATE_MAC, as shown in step 2 in the figure below,Does the "CMD_DBG_CHA" command have to be followed by the command "CMD_DBG_AUTH"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @584914019,
The challenge and response(authorization) is a two-step operation.
But the calculation of CMAC needs to be done before we can send the response (authorization) to CSEc. And this step can’t be ignored or calculated before the challenge is issued, the challenge is a random number.
The RM does not say no CSEc operation can be performed between these two steps, that's impossible.
Also, AN5401 shows how to generate the CMAC of response (authorization).
Regards,
Daniel