- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- Product Forums
- :
- S32K
- :
- How to avoid illegal data reading
How to avoid illegal data reading
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to avoid illegal data reading
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello,
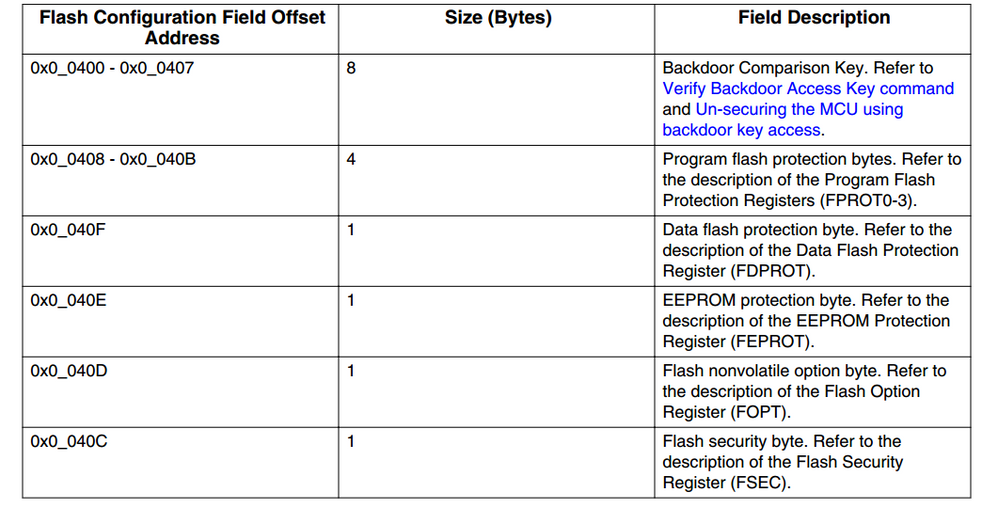
Program flash and EEPROM are not read-protected. So how do you prevent others from reading the code? I see that STM32 allows users to set read protection, so that the data read is AAAAAAAA, but it does not affect the operation of the program. In your reference manual, I did not see an introduction to read protection. How does S32k146 do read protection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
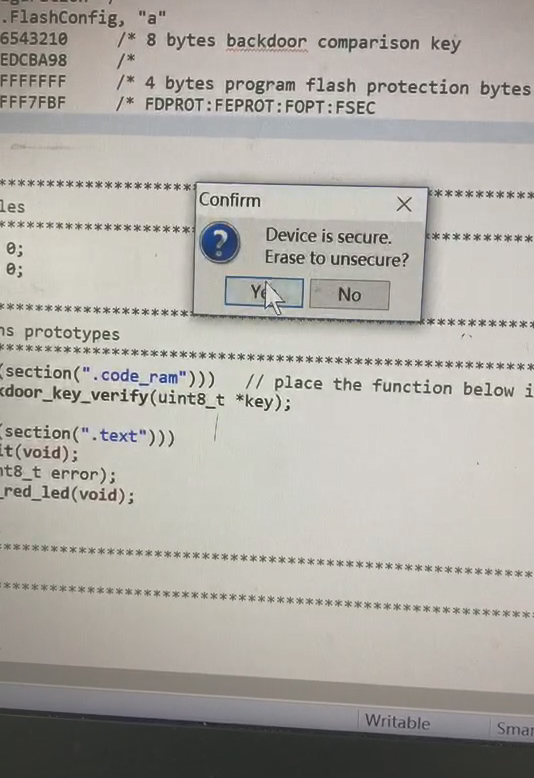
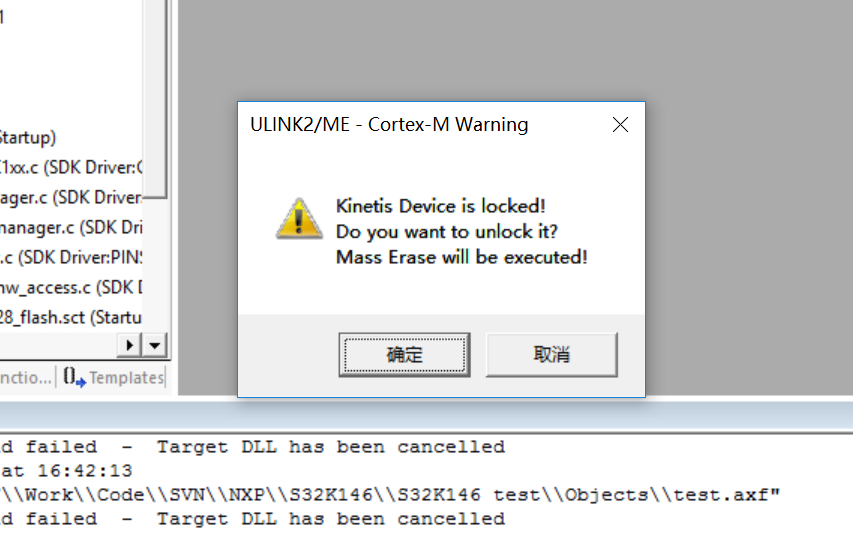
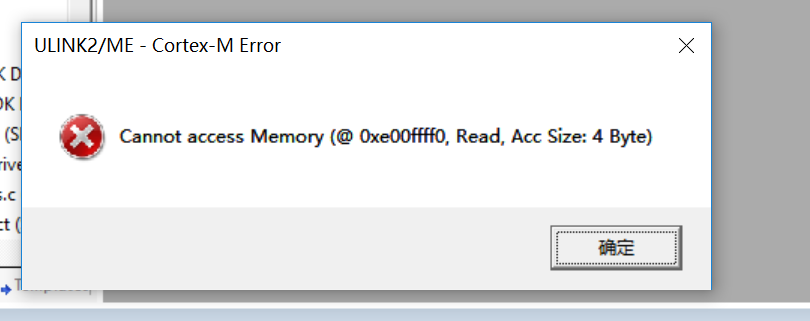
hello, now my device S32K146 state as the first picture , D1 LED is light always.
Debug status as the second and third pictures, press "Yes" in the second picture it will jump to the third picture, then press " retry" in the third picture, it will jump to the second picture.
how can i resolve this problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello 814420552@qq.com,
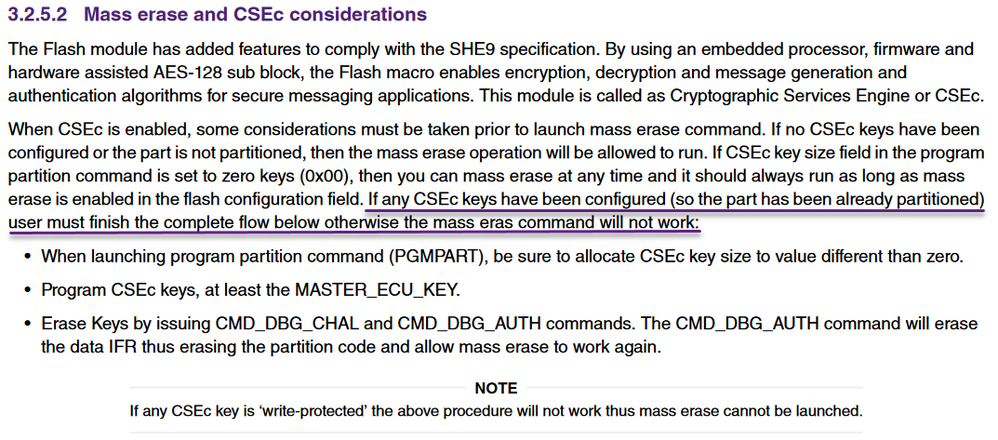
Is the MCU partitioned with CSEc keys allocated?
https://www.nxp.com/docs/en/application-note/AN12130.pdf
BR, Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
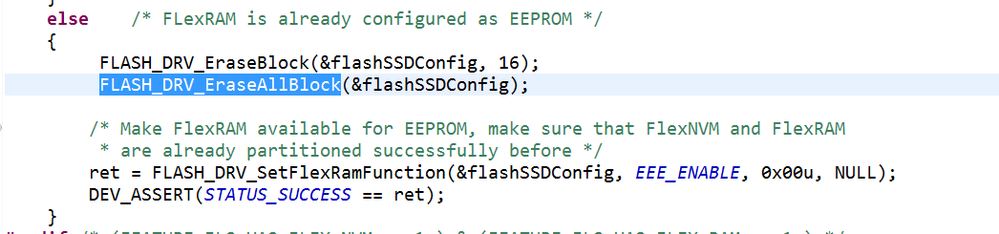
I remember that execute the following code
this is my test code, after this operation, The device security.
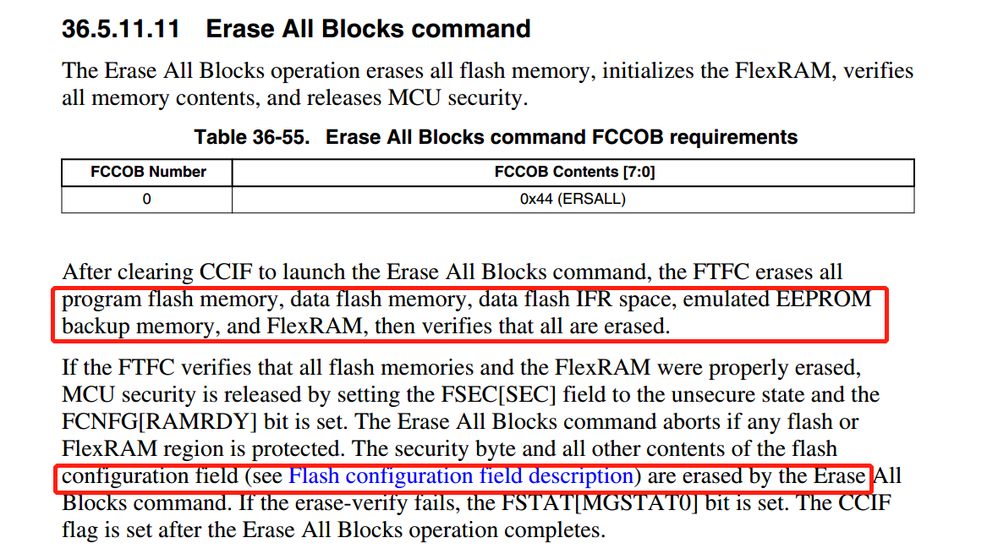
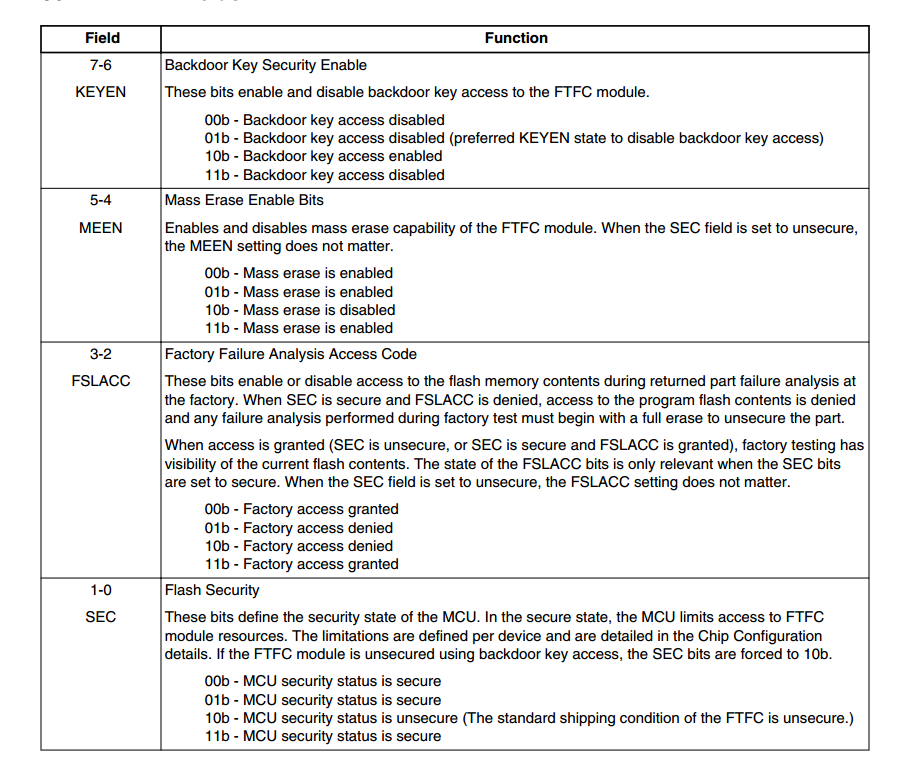
from the manual i found configuration is erased after execute erase all block command , so all the following data is changed to 0xFF, when reset the device is secured, MEEN = 11b, KEYEN = 11b,SEC = 11b.
current device is secured so this command executed succcessfully. so it is no need to consider whether to enable CSEc.
when switch to KEIL 5, run debug tips the following
then press “确定”
I don't know why, wish your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello 814420552@qq.com,
Please refer to the reference manual.
It has been already discussed, for example, here:
You can use the Backdoor key feature to remove the protection without erasing the MCU:
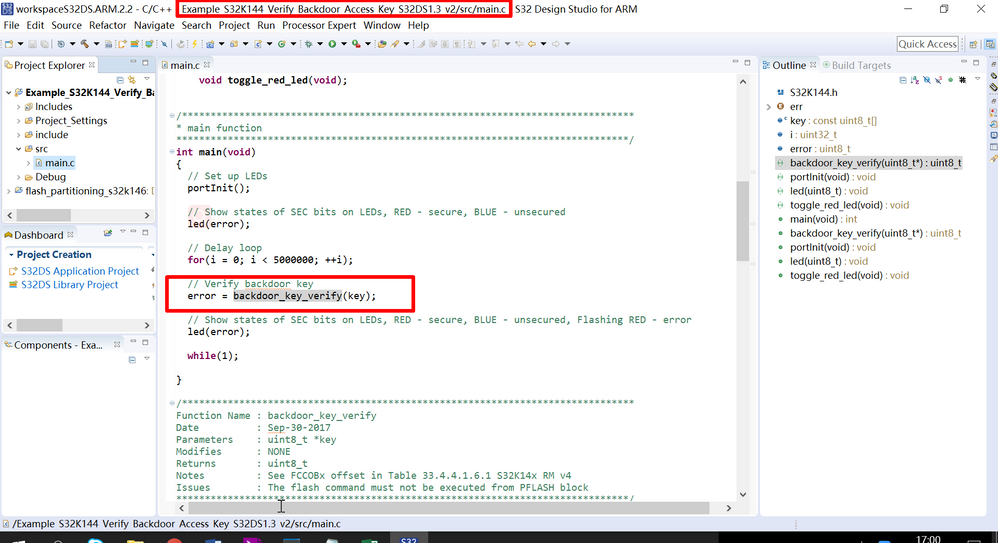
Example S32K144 Verify Backdoor Access Key S32DS1.3
Regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<1> is the backdoor key defined by NXP when the device produced?
<2> does the backdoor key can be updated by user?
you said:You can use the Backdoor key feature to remove the protection without erasing the MCU:
my question is the follow
<3> can i call the API backdoor_key_verify(Key) remove the protection?
<4> if i want to remove partition and not erase MCU, the steps are
I. call API backdoor_key_verify(Key).
II. call erase all block command
are the steps right? if not can you tell me the right step?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello 814420552@qq.com,
I believe that it is explained in the example.
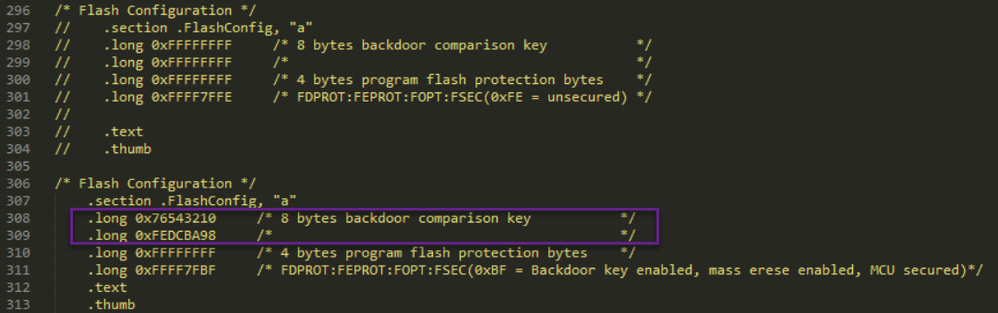
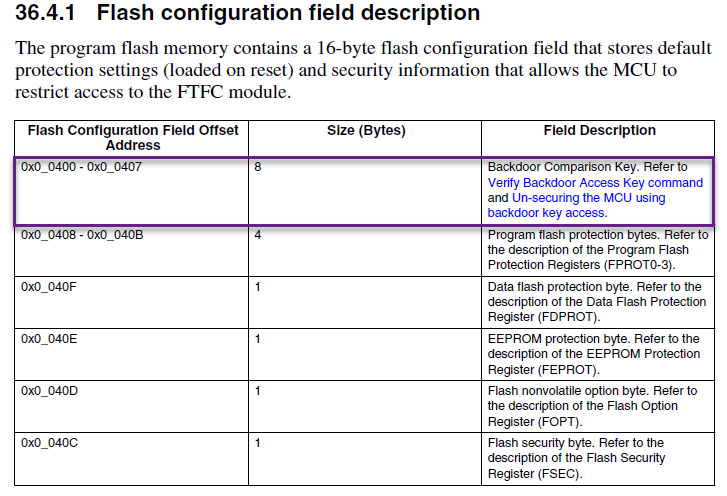
The backdoor key is defined by the user in the startup_S32K144.S file.
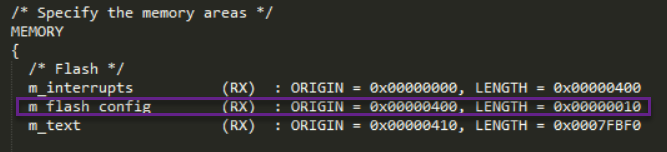
At 0x400 in the S32K1xx_flash.ld linker file.
The Backdoor Key Verify FTFC command (0x45) can be used only if the flash configuration field has the key defined.
The command unlocks the MCU so that the debugger can access the memory/registers of the MCU.
If the key is not defined and the MCU is locked, the debugger can only mass erase the MCU.
Regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi Daniel,
how can I know the backdoor key?and if my device S32K148 demo board executed erase all block command the
device will be secured, openSDA can't connect with Device and D1 led keep light, then how can i resove this problem?
if execute backdoor command, but I don't konw the backdoor key. onthe other hand if i know the backdoor key how can i execute this backdoor command in the deviec?(Debug can't connect)
wish your henlp, thanks very much!