- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- Identification and Security
- :
- NFC
- :
- Re: Change Keys and "lock" NTAG DNA 424
Change Keys and "lock" NTAG DNA 424
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Change Keys and "lock" NTAG DNA 424
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
Thanks to jonathaniglesias, i was now able to configure the NTAG 424 DNA with encrypted-part and CMAC-part (https://community.nxp.com/message/1349087?commentID=1349087#comment-1349087) and also build my own backend (https://community.nxp.com/thread/535033) in order to be able to verfiy the cmac that is provide in the URL
Example-URL: https://ntag.nxp.com/424?e=EF963FF7828658A599F3041510671E88&c=94EED9EE65337086
--------
Now comes the last step of my NTAG 424 DNA configuration and verification process, which is:
- changing the keys from default to custom keys
- locking the tag so that NO further changes can be done to the tag
Until now i only used the default keys 00000000000000000000000000000000 or empty keys for testing purposes in my backend and on my tag.
My backend basically uses two keys for now, both have the value 00000000000000000000000000000000. Let's call these two keys:
- KeyDec: I am using this key to decrypt the encoded query parameter "e" which gives me the ctr and uid in plaintext afterwards
- KeyCmac: I am using this key to generate the session key with the help of the uid and the ctr value (from the process above), and afterwards I am able to get the CMAC in order to be able to compare my calculate CMAC with the CMAC from the URL (the "c" query param from the url above).
------
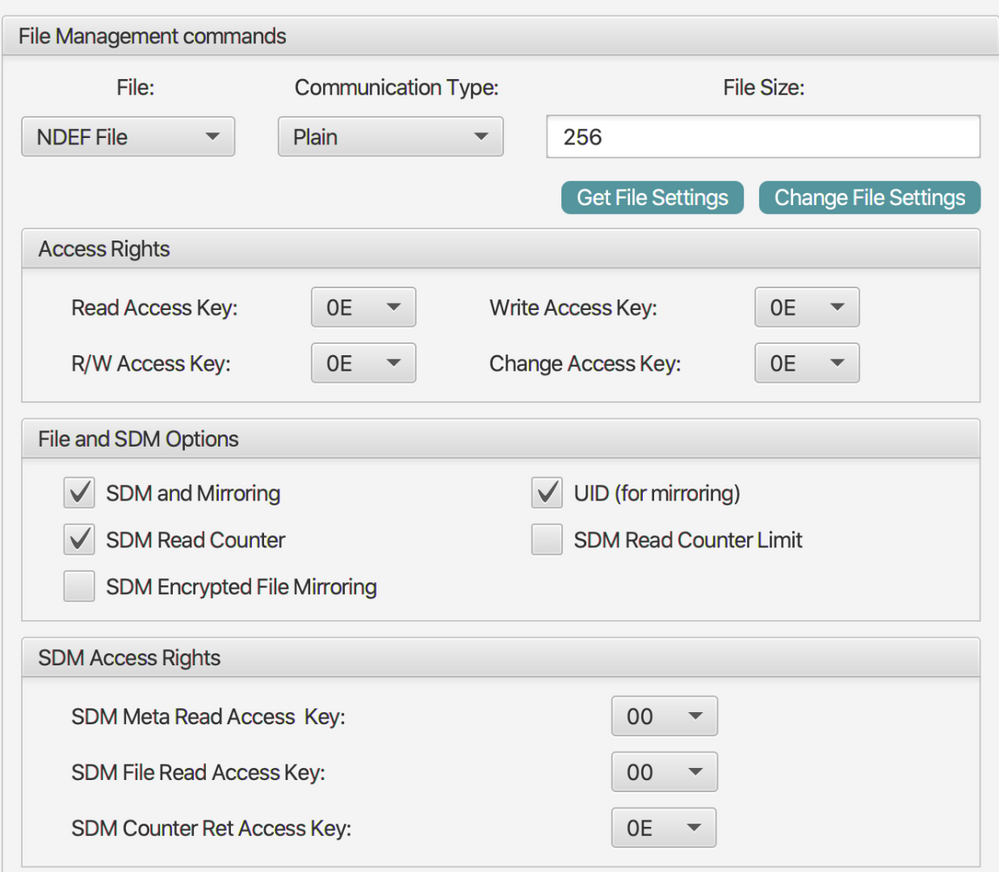
Until now i have not changed any of my keys on the tag and the configuration looks like this:
Goal:
Let us assume now that I want to use:
00000000000000000000000000000001 as value for my KeyDec
and
00000000000000000000000000000002 as value for my KeyCmac
Question:
What are the exact steps that i need to perform in the TagXplorer and in which order to achieve, that my backend would now successfully validate the tag with the new keys? (please with screenshots if possible :smileyhappy: )
-----
Question2:
Let us assume that the question above has been solved, how can i now (as a final step) protect my tag in a way that none of these keys can be read anymore from the tag and that also no data changes can be done anymore to the tag, so that the tag is ready to be used on a product in order to proof product authenticity?
Thank you (jonathaniglesias)
Btw: Thank you so much Jonathan for your great help at any time :smileyhappy:
Best,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Following the topic, do I have to have the master key at the back end to do the verification? Can I use a private key in the tag and a public key to verify?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Following the topic, do I have to expose the master key to the backend when verifying the authentication? Is there a way that I can put the private key inside the chip, and give the public key to the backend which might be my partners (I don't want to expose the private key to them)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Manuel Mertl,
ok here we have two topics, first on the key changing. the right process is the following:
1.- authenticate with masterkey
2.-change key 01
3.- authenticate again with masterkey as step 1
4.- change key 2
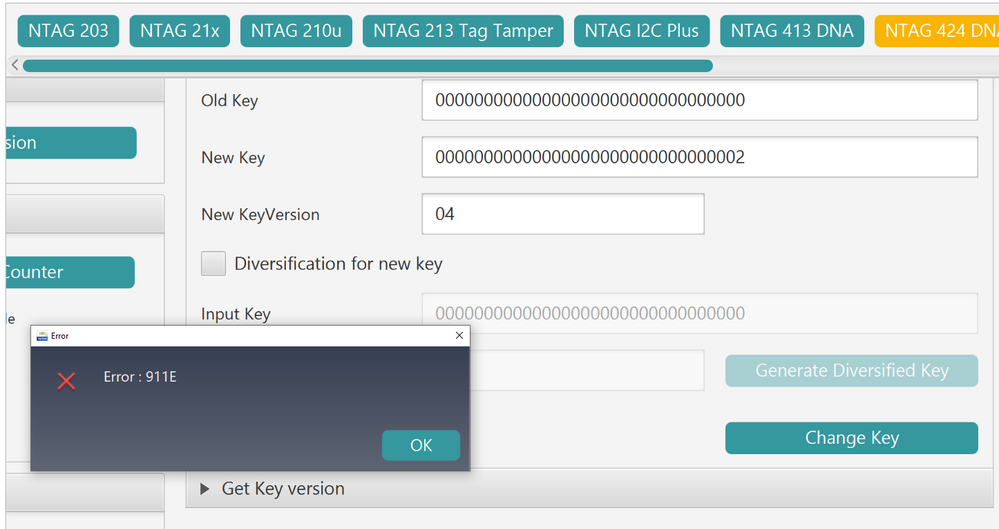
it is important that you know the information of the key inside the tag, if you happen to change the key in the past and you put the wrong key in the fields this will lead to the error that happened to you.
for example after this process tried to change again the key 02 with the incorrect values and this is wrong and will lead you to the 911e error.
for the encryption and decryption process the best would be to use the Application note NTAG 424 DNA and NTAG 424 DNA TagTamper features and hints ,4.3 section to understand the SDM Session Key Generation.
and the 4.4.2 PICCData Encrypted mirror to understand the encryption/decryption process.
let me know if you still have issues!
Have a nice day !
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, jonathaniglesias.
I think i solved the first part of my question.
I did it in the following way:
- authenticate master key 00
- set key 01 to value 00000000000000000000000000000001
- authenticate master key 00
- set key 02 to value 00000000000000000000000000000002
and then i am using the following configuration to calculate the new encrypted value (ctr+uid) as well as the cmac value
the resulting encrypted value (ctr+uid) in the url as well as the cmac in the url are matching the values calculated by my backend, so that is fine now.
------
My next questions is regarding "locking" the tag:
So my tag is now configured and working, it gives me the correct values that my backend accepts for the given two keys. In the last step I want to make sure that nobody can ever read the keys from the tag or change any data in any way to stop the NFC-tag from working, so I want to prevent any data/key changes to the tag.
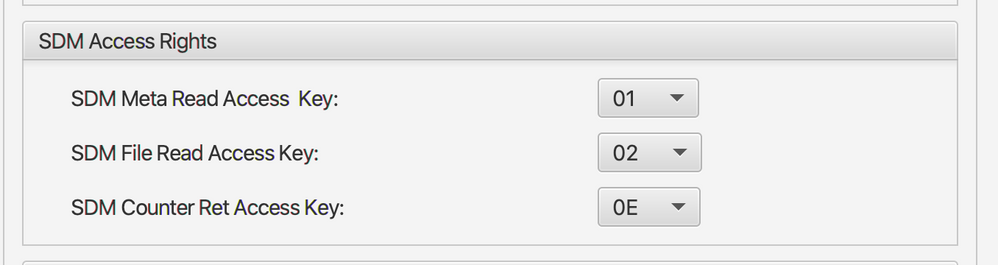
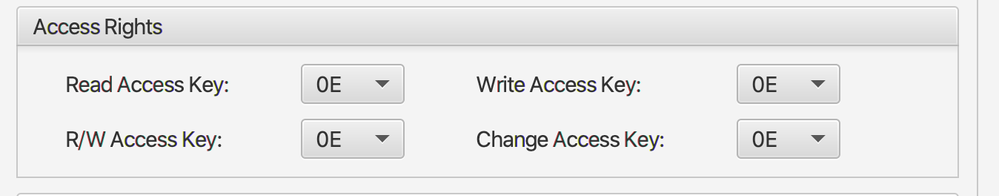
is it enough to do the following, as you described in your reply above:
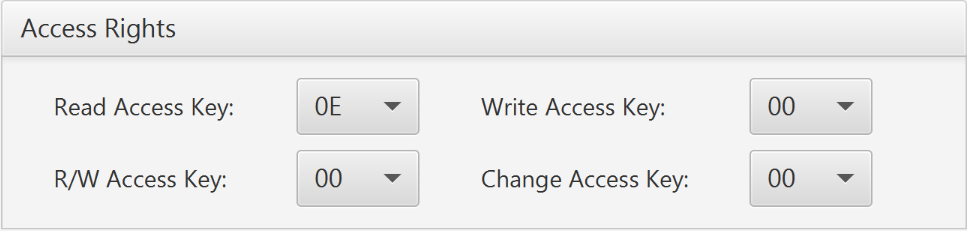
or should i also change here some values, since they are all set to 0E.
So once again, now that everything is working correctly the goal is to lock the tag and make it impossible for anyone to change data and keys again or read any of the keys ever again, since its meant to be used as product authentictiy solution.
Thank you so much jonathaniglesias
Best,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
please make the change on the CC file and set the rights of the NDEF file you can set it to read as "0E" for free reading access but would be good you set other access to masterkey so only you have this keys and be able to modify something.
if you set something to "0F"it means no access.
like the image above.
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you jonathaniglesias
1)
why do we have to leave the Read Access Key set to 0E instead of 00 like the other 3 acces right key here ?
2)
I guess i have to make the change to the CC file as the very last step, correct?
So first setting the 4 access rights like above 0E, 00, 00, 00, then changing the key 00 to something that i dont have to remember because i never ever want anyone including myself to be able to change data again, and then do the CC File change?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) this is because the main purpose of this is that the phone does not need a specific application to launch the link, any phone can launch a link and the back-end will check the information, if you set this to 00, this means first that there will be a need on your side to develop an application that activate the card and authenticate with the key 00 and then launch the link, also this is not recommended because this means your master key will be in an application and that is not safe, either if you set this to any other key number, 01, 02,... having the 0E means that any phone can read this and then launch the link. only read access should be 0E.
2) yes, usually the CC modification is done at the end, after all the NDEF is configured and the keys changed, access conditions, etc. then you change this.
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the access rights are set as below, is there still a need to program the CC?
- Read Access Key: 0E (no key required)
- R/W Access Key: 0F (no access)
- Write Access Key: 0F (no access)
- Change Access Key: 0F (no access)
Making the tag read-only is described in AN12196 section 6.15, is this 'data' in the table next to step '5' a fixed value?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Manuel,
Hope you are doing great, to change keys you can go to the security management section under NTAG 424 DNA and below the authentication area there is a change key area, so basically you will need to authenticate with the card masterkey as you can see in the DS
then issue the change key command, then you will need to take the take away from the field and put it back again so this changes happen.
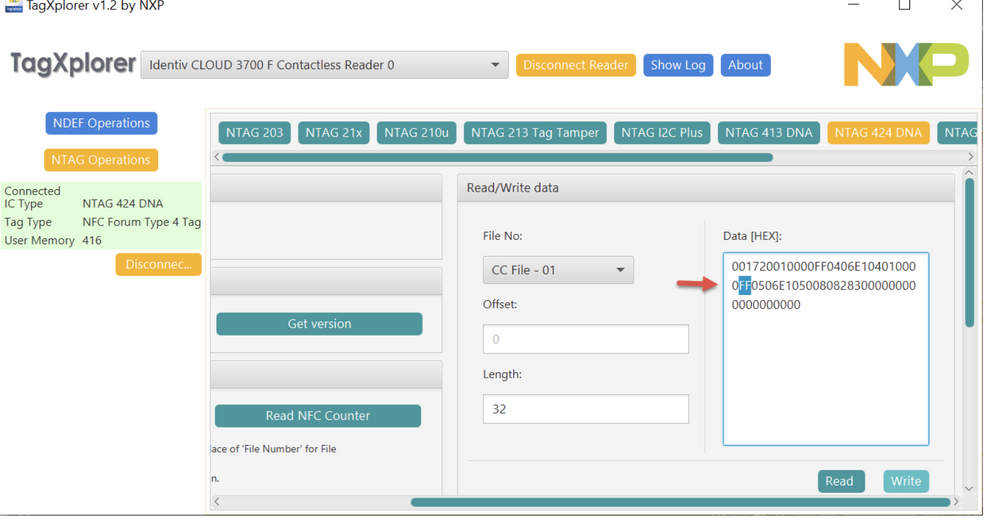
for question 2
the best would be that you modify the Capability container file the E103, if done properly this will put the card in read only mode so the tag can be reader this is done ususally in the same session where you program the NDEF into the NTAG so after doing the NDEF configuration stated in previos threads, you will need to read the CC file to get the value and just modify this into FF ( section 8.2.3.2 https://www.nxp.com/docs/en/data-sheet/NT4H2421Gx.pdf )
and write this, if you are in other session first authenticate like you did in the previous community thread.
hope this helps.
Have a nice day !
BR
Jonathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
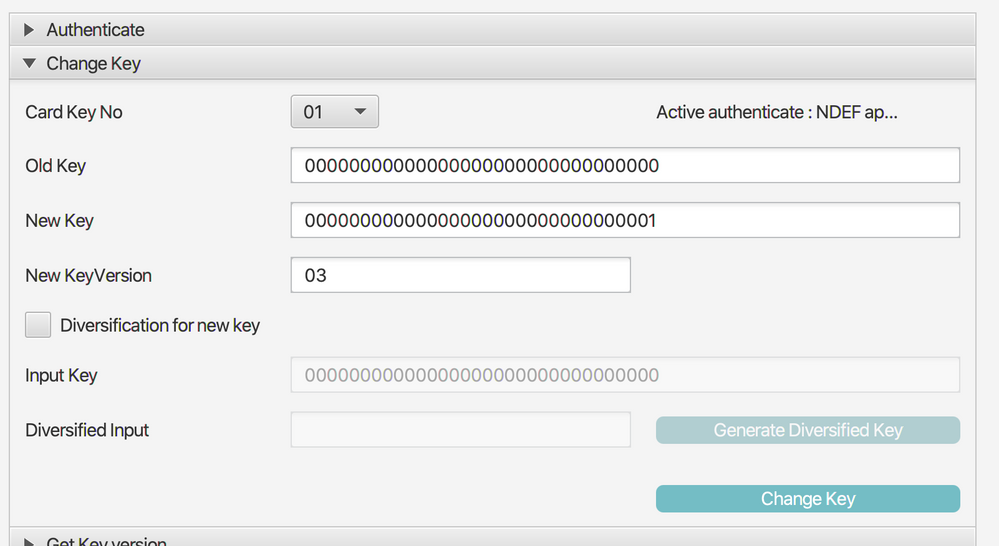
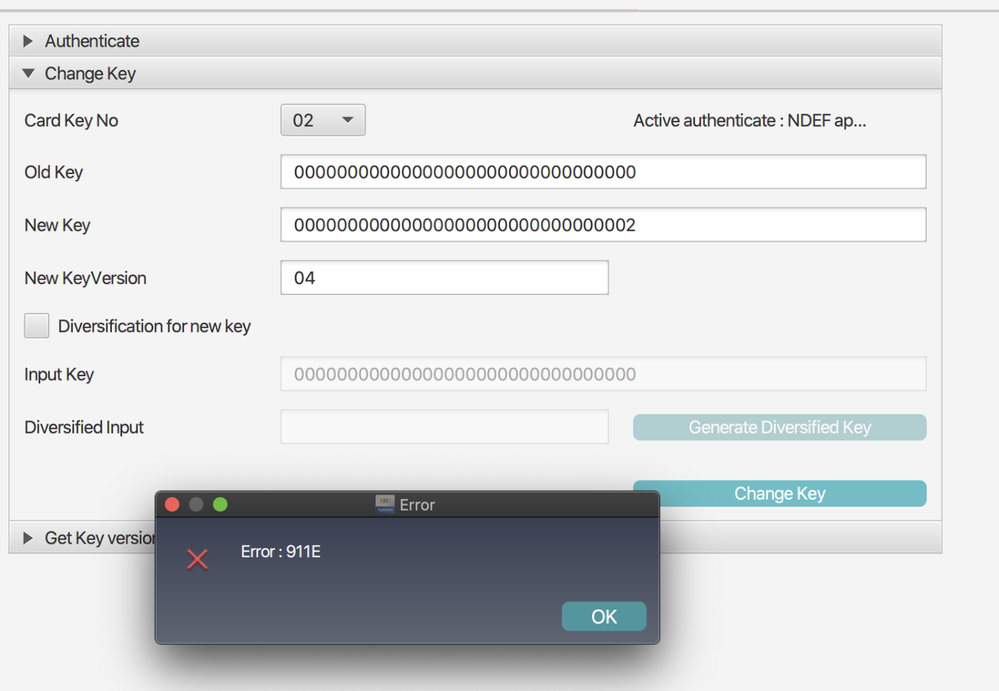
Okay, so let us assume now that I want to use:
00000000000000000000000000000001 as value for my KeyDec
and
00000000000000000000000000000002 as value for my KeyCmac
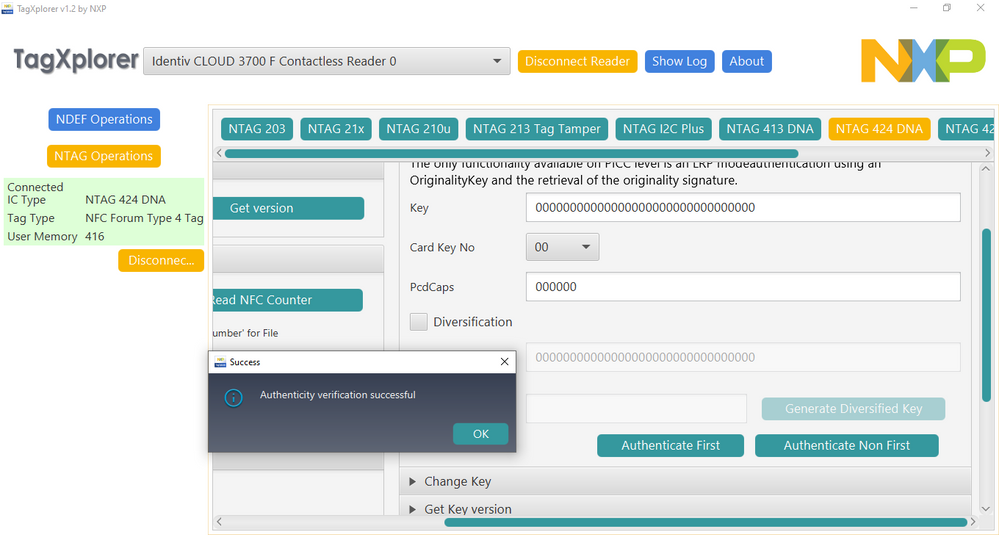
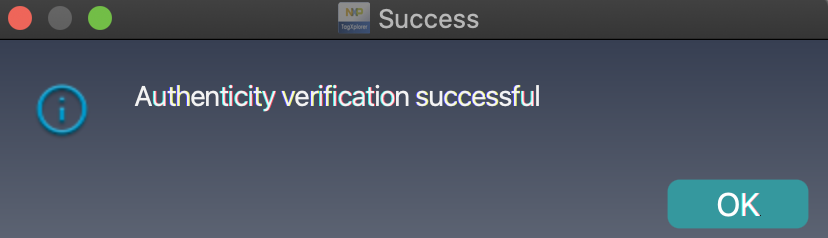
1) I go to "Security Management" and click "Authenticate First"
which prompts me:
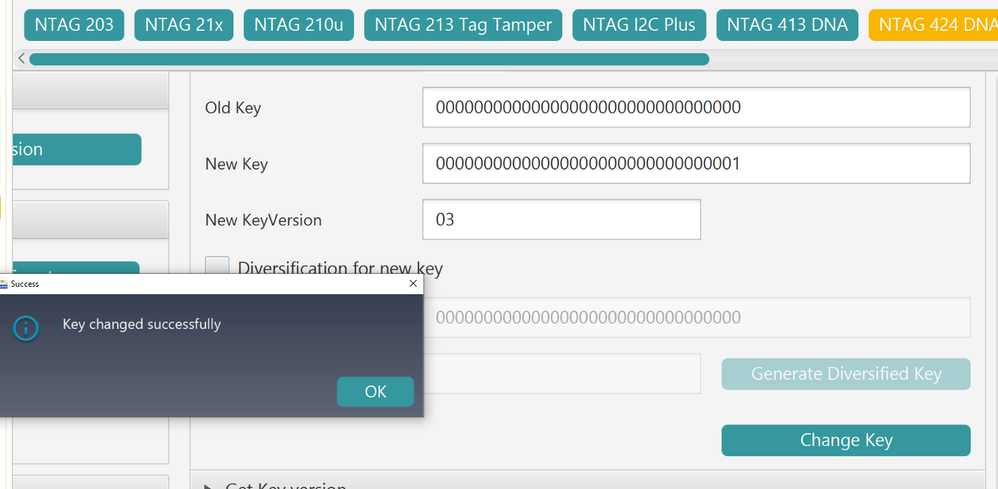
2) I go to Change Key and want to change lets say Key 01 and use that as KeyDec thus setting the value 00000000000000000000000000000001 and also set a new version for example 03
which prompts me:
3) then i have to authenticate again
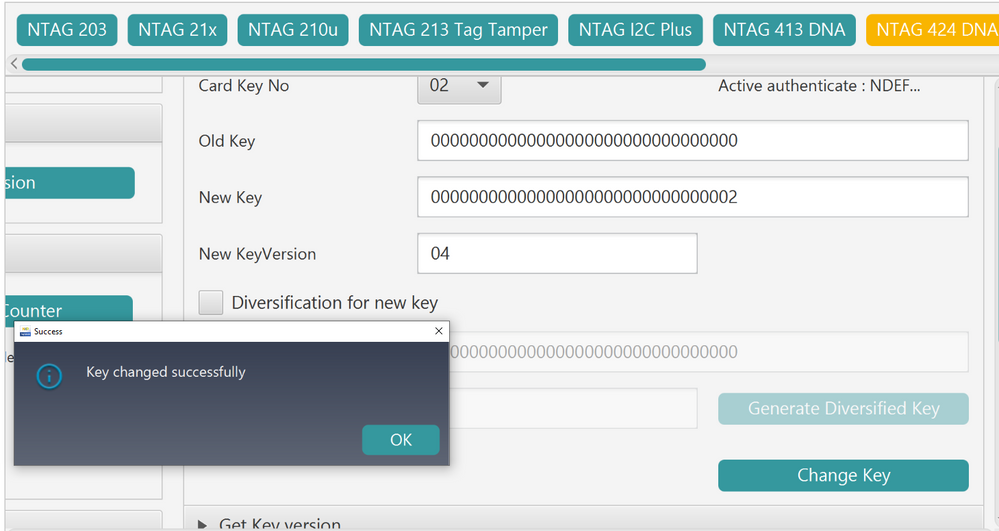
4) I go to Change Key and want to change lets say Key 02 and use that as KeyCmac thus setting the value 00000000000000000000000000000002 and also set a new version 04
but this gives me already an Error: 911E
Thanks, jonathaniglesias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
also I would like to ADD that this CMAC key and encryption keys are derivated from the authentications, you basically use one key to authenticate, during this process certain information will be shared between the tag and the reader that will create to SV numbers and after some process this SV1 and SV2 will turn into session key for CMAC and other for encryption. hope this is clear if not I can clarify it.
BR
Jonathan