- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- 汎用マイクロコントローラ
- :
- LPCマイクロコントローラ
- :
- LPC55S69 : disable PowerQuad
LPC55S69 : disable PowerQuad
- RSS フィードを購読する
- トピックを新着としてマーク
- トピックを既読としてマーク
- このトピックを現在のユーザーにフロートします
- ブックマーク
- 購読
- ミュート
- 印刷用ページ
LPC55S69 : disable PowerQuad
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi !
I'm not using PowerQuard co-processor on any side secure and nonsecure and would like to disable it in correct way.
( No idea if it used in Boot-Rom during Secure boot)
I can see in default SystemInit() it is always activated for usage together with FPU.
I try to disable it but I can't do it becouse startup freeze at early phase and I should enable access to it at list from Secure side.
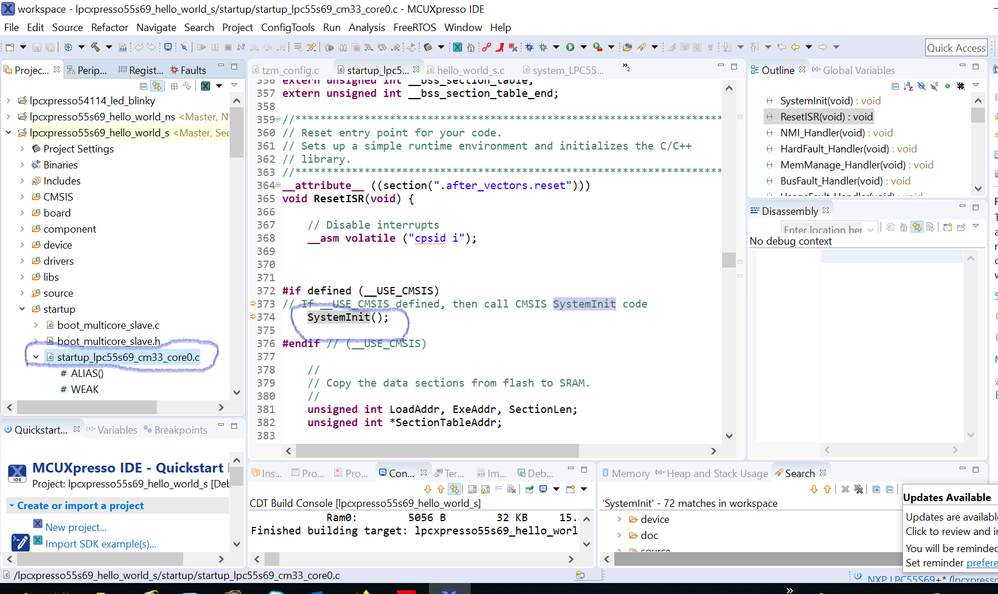
// This line when disabled cause freeze !
SCB->CPACR |= ((3UL << 0 * 2) | (3UL << 1 * 2)); /* set CP0, CP1 Full Access in Secure mode (enable PowerQuad) */
#if defined(__ARM_FEATURE_CMSE) && (__ARM_FEATURE_CMSE == 3U)
//SCB_NS->CPACR |= ((3UL << 0 * 2) | (3UL << 1 * 2)); /* set CP0, CP1 Full Access in Normal mode (enable PowerQuad) */ // OK!
#endif /* (__ARM_FEATURE_CMSE) && (__ARM_FEATURE_CMSE == 3U) */
//SCB->NSACR |= ((3UL << 0) | (3UL << 10)); /* enable CP0, CP1, CP10, CP11 Non-secure Access */ // OK !
SCB->NSACR |= (/*(3UL << 0) | */(3UL << 10)); /* enable CP10, CP11 Non-secure Access */// OK !
How-to disable PowerQuard and other co-processors if they not used at all.
Only FPU should remain.
Regards,
Eugene
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi, Eugene,
Pls refer to the following part, the MPU, SysTick timer, and some of the registers in the System Control Block (SCB) are
also banked. In other words, secure and NON-secure SCB use different address.
I suggest you refer to the SDK example "lpcxpresso55s69_hello_world_s" in SDK, refer to file core_cm33.h, it defines different struct for secure and non-secure for SCB.
1. secure
/* Memory mapping of Core Hardware */
#define SCS_BASE (0xE000E000UL) /*!< System Control Space Base Address */
#define ITM_BASE (0xE0000000UL) /*!< ITM Base Address */
#define DWT_BASE (0xE0001000UL) /*!< DWT Base Address */
#define TPI_BASE (0xE0040000UL) /*!< TPI Base Address */
#define CoreDebug_BASE (0xE000EDF0UL) /*!< Core Debug Base Address */
#define SysTick_BASE (SCS_BASE + 0x0010UL) /*!< SysTick Base Address */
#define NVIC_BASE (SCS_BASE + 0x0100UL) /*!< NVIC Base Address */
#define SCB_BASE (SCS_BASE + 0x0D00UL) /*!< System Control Block Base Address */
#define SCnSCB ((SCnSCB_Type *) SCS_BASE ) /*!< System control Register not in SCB */
#define SCB ((SCB_Type *) SCB_BASE ) /*!< SCB configuration struct */
#define SysTick ((SysTick_Type *) SysTick_BASE ) /*!< SysTick configuration struct */
#define NVIC ((NVIC_Type *) NVIC_BASE ) /*!< NVIC configuration struct */
#define ITM ((ITM_Type *) ITM_BASE ) /*!< ITM configuration struct */
#define DWT ((DWT_Type *) DWT_BASE ) /*!< DWT configuration struct */
#define TPI ((TPI_Type *) TPI_BASE ) /*!< TPI configuration struct */
#define CoreDebug ((CoreDebug_Type *) CoreDebug_BASE ) /*!< Core Debug configuration struct */
2.non-secure.
#if defined (__ARM_FEATURE_CMSE) && (__ARM_FEATURE_CMSE == 3U)
#define SCS_BASE_NS (0xE002E000UL) /*!< System Control Space Base Address (non-secure address space) */
#define CoreDebug_BASE_NS (0xE002EDF0UL) /*!< Core Debug Base Address (non-secure address space) */
#define SysTick_BASE_NS (SCS_BASE_NS + 0x0010UL) /*!< SysTick Base Address (non-secure address space) */
#define NVIC_BASE_NS (SCS_BASE_NS + 0x0100UL) /*!< NVIC Base Address (non-secure address space) */
#define SCB_BASE_NS (SCS_BASE_NS + 0x0D00UL) /*!< System Control Block Base Address (non-secure address space) */
#define SCnSCB_NS ((SCnSCB_Type *) SCS_BASE_NS ) /*!< System control Register not in SCB(non-secure address space) */
#define SCB_NS ((SCB_Type *) SCB_BASE_NS ) /*!< SCB configuration struct (non-secure address space) */
#define SysTick_NS ((SysTick_Type *) SysTick_BASE_NS ) /*!< SysTick configuration struct (non-secure address space) */
#define NVIC_NS ((NVIC_Type *) NVIC_BASE_NS ) /*!< NVIC configuration struct (non-secure address space) */
#define CoreDebug_NS ((CoreDebug_Type *) CoreDebug_BASE_NS) /*!< Core Debug configuration struct (non-secure address space) */
1.3.3 Banked internal resources
Several internal resources are banked between Secure and Non-secure states.
For registers inside the processor core:
• The Stack Pointers are banked between Secure and Non-secure states. This enables separations of
Secure and Non-secure stacks.
• Interrupt masking registers like PRIMASK, FAULTMASK, and BASEPRI are banked.
• FAULTMASK and BASEPRI are available on the ARMv8-M architecture with Main Extension only.
This allows existing software to be reused, but Non-secure software cannot influence the operation of
Secure software.
• Bit 0 and 1 of the special CONTROL register are banked. Secure and Non-secure software can have
different Stack Pointer control and privileged settings.
In addition, the MPU, SysTick timer, and some of the registers in the System Control Block (SCB) are
also banked. For example, the Vector Table Offset Register (VTOR) is banked to allow the vector tables
for Secure software and Non-secure software to be separated. Software that accesses these registers using
an existing address accesses the corresponding view of the peripheral based on the current processor
state. Secure accesses see Secure peripherals. Non-secure accesses see Non-secure peripherals. Secure
software can also access Non-secure versions of these components using alias addresses.
The following figure shows the system control and debug area of a typical memory map:
Especially, pls refer to tzm_config.c for the SCB initialization.
Hope it can help you
BR
XiangJun Rong
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi xiangjun.rong !
But this line :
// This line when disabled cause freeze !
SCB->CPACR |= ((3UL << 0 * 2) | (3UL << 1 * 2)); /* set CP0, CP1 Full Access in Secure mode (enable PowerQuad) */
executed on Secure side and if it missing, firmware freeze somewhere even no accesses to PowerQuard.
I assume I can disable accesses to it on secure and nonsecure side by using TEE config.
Is this possible ?
Regards,
Eugene
- 新着としてマーク
- ブックマーク
- 購読
- ミュート
- RSS フィードを購読する
- ハイライト
- 印刷
- 不適切なコンテンツを報告
Hi, Eugene,
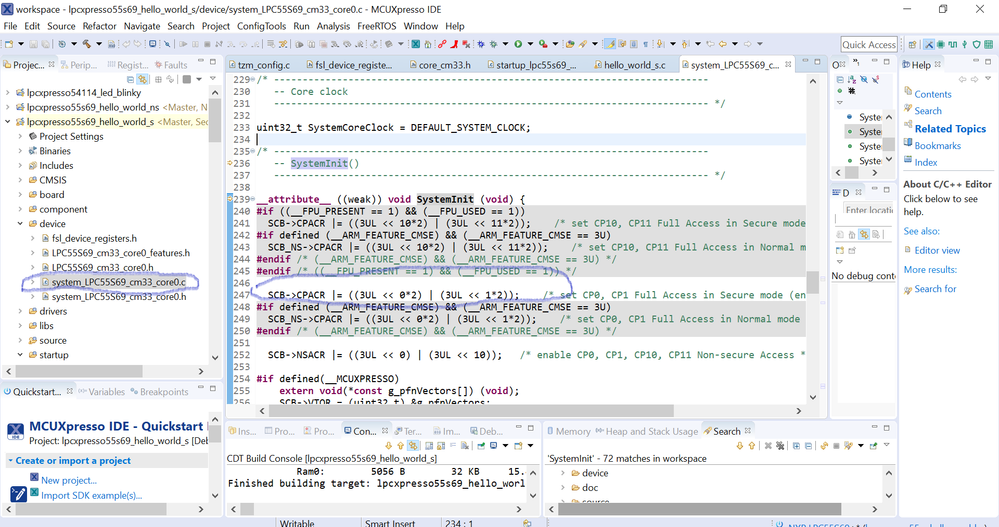
This is the code for the example.
The SystemInit() function is defined as the second fig. So in secure mode, it is okay to call the SCB->CPACR |= ((3UL << 0*2) | (3UL << 1*2));
Hope it can help you
BR
XiangJun Rong