- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- i.MX Forums
- :
- i.MX Processors
- :
- iMX8M HAB
iMX8M HAB
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
iMX8M HAB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'll start with the bottom line. I followed a document, received from NXP, for applying HAB on iMX8M processor. After updating the signed boot image and running "hab_status" command I receive the following:
Secure boot disabled HAB Configuration: 0xf0, HAB State: 0x66
As you can see, on one hand I don't see any event printed but on the other hand I also don't see the following typical message you see on a successful secure boot:
No HAB Events Found!This leaves me with a question regarding the real status.
I must say that the document I'm following, seems to be in early stages of wring and far from a formal document you can find for iMX6, for example. In this document, there are references to figures that don't exist in the document. Some of the figures contain information that is referenced later. Specifically it can be found when generating CSF files and updating the relevant HAB blocks. I believe I was able to fill this gap of information, but there is some doubt here.
So to conclude:
1. Is it OK or not, that I don't see " No HAB Events Found!" message?
2. Do you have an updated and more complete version of the document?
Thanks,
Eli.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi guys,
Regarding the HAB on i.MX8M.
I know that i.MX6 HAB does not check the validity of the certificate. -> good for my project.
What is about the i.MX8 Series or specially the i.MX8M. Is there a validity check for the certificate?
Thanks in advanced!
And may I ask here...
Are there any hints for setup FIT + pubkey in uboot.dtb with the "new" u-boot layout.
So fare I'm able to do the u-boot verification with HAB and it works fine.
u-boot=> hab_status
Secure boot disabled
HAB Configuration: 0xf0, HAB State: 0x66
No HAB Events Found!
u-boot=>
as well I'm able to sign the FIT image with the mkimage. the local check for the signature the FIT image is working as well.
u-boot-imx8/tools/fit_check_sign
Verifying Hash Integrity ... sha1,rsa2048:dev+
## Loading kernel from FIT Image at 7f366c0e9000 ...
Using 'conf@freescale_fsl-imx8mm-port-core-techshine.dtb' configuration
Verifying Hash Integrity ...
sha1,rsa2048:dev+
OK
Trying 'kernel@1' kernel subimage
Description: Linux kernel
Created: Thu Jun 25 14:04:04 2020
Type: Kernel Image
Compression: lzo compressed
Data Size: 8942282 Bytes = 8732.70 KiB = 8.53 MiB
Architecture: AArch64
OS: Linux
Load Address: 0x40480000
Entry Point: 0x40480000
Hash algo: sha256
Hash value: f2a2bb34afe08591f1c7bea8866741b1dfff21fc134e61d28e1f257d8998f0db
Verifying Hash Integrity ...
sha256+
OK
Uncompressing Kernel Image ... Unimplemented compression type 4
## Loading fdt from FIT Image at 7f366c0e9000 ...
Using 'conf@freescale_fsl-imx8mm-port-core-techshine.dtb' configuration
Verifying Hash Integrity ...
sha1,rsa2048:dev+
OK
Trying 'fdt@freescale_fsl-imx8mm-port-core-techshine.dtb' fdt subimage
Description: Flattened Device Tree blob
Created: Thu Jun 25 14:04:04 2020
Type: Flat Device Tree
Compression: uncompressed
Data Size: 36093 Bytes = 35.25 KiB = 0.03 MiB
Architecture: AArch64
Hash algo: sha256
Hash value: 759cd7596fde70a1ca5eb925f5e7180e5e813d33d38bbc12b4eac3de2459b9ae
Verifying Hash Integrity ...
sha256+
OK
Loading Flat Device Tree ... OK
## Loading ramdisk from FIT Image at 7f366c0e9000 ...
Using 'conf@freescale_fsl-imx8mm-port-core-techshine.dtb' configuration
Verifying Hash Integrity ...
sha1,rsa2048:dev+
OK
Could not find subimage node
Signature check OK
Problem is now if I create the flash.bin including the pubkey in the u-boot.dtb. I guess in this step I do something wrong. On the target the u-boot is not able to find the key to verify the signed FIT image. (dtb name removed because of policy)
u-boot=> ext2load mmc 2:1 0x50480000 image_signed_yocto_portkey_rsa.fit
8980546 bytes read in 140 ms (61.2 MiB/s)
u-boot=> bootm 0x50480000
## Loading kernel from FIT Image at 50480000 ...
Using 'conf@freescale_fsl-imx8mm-x-x-x.dtb' configuration
Verifying Hash Integrity ... sha1,rsa2048:portkey- Failed to verify required signature 'key-portkey'
Bad Data Hash
ERROR: can't get kernel image!
I'm working with the doc files from u-boot.
doc/imx/habv4/guides/mx8m_mx8mm_secure_boot.txt
doc/uImage.FIT/signature.txt
doc/uImage.FIT/beaglebone_vboot.txt
unfortunately I was not able to get it work as it should...
Would be great if someone has a Hint here.
Thanks
guys
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Yuri,
So I've extracted HAB persistent memory (addres - 0x009061C0, size -0x0B80) and it seems like there is a single HAB event with the following Header and SRCE:
db 00 24 43 69 30 e1 1d
I parsed it using HAB4_API document under CST tool as follows:
Status = 0x69 --> HAB_WARNING
Reason = 0x30 --> HAB_ENG_FAIL (Engine failure)
Context = 0xe1 --> HAB_CTX_ENTRY (Event logged in hab_rvt.entry())
Engine = 0x1d --> HAB_ENG_CAAM (Cryptographic Acceleration and Assurance Module)
So it seems like there is an issue with the initialization of the HAB library done by hab_rvt.entry funcion.
It is as far as I can get for now but I still can't understand the issue.
I'd appreciate any comment on the new findings.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
What NXP Linux BSP is used?
What is CSF file?
Regards,
Yuri.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Yuri,
Following is revision and CSF info:
CPU - Freescale i.MX8MQ rev2.0
Linux - 4.9.51-imx_4.9.51_imx8m_ga_var01+ga7188e8
U-Boot - 2017.03-imx_v2017.03_4.9.51_imx8m_ga_var01+g94b8909
CSF for FIT image:
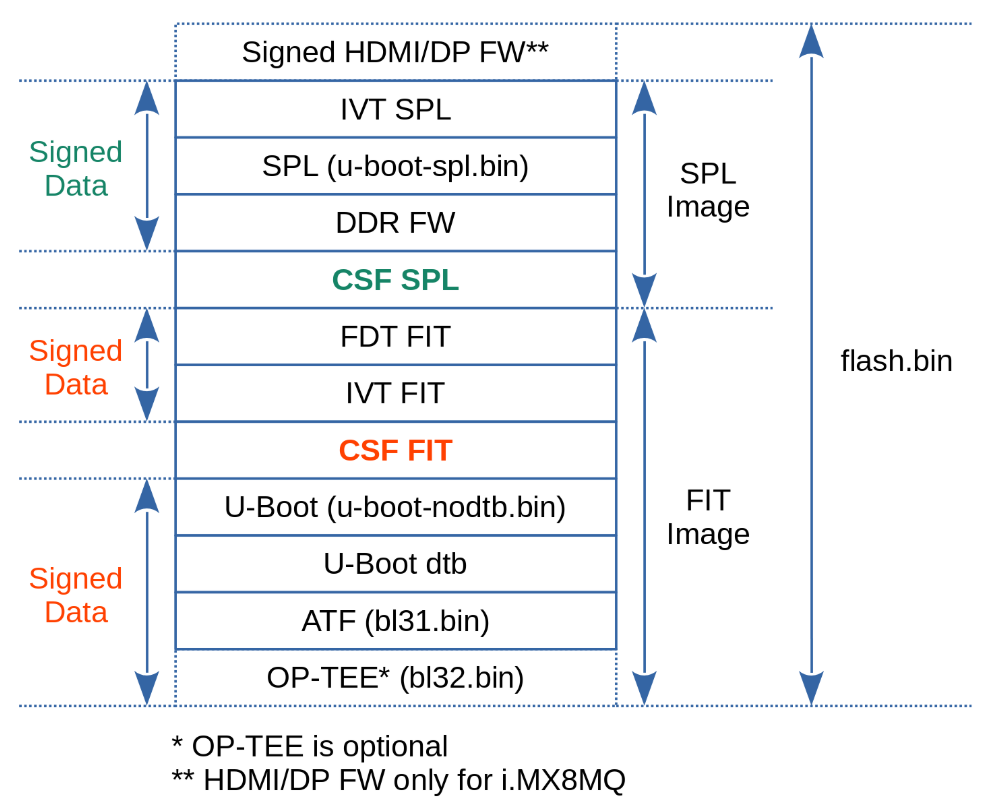
[Header] Version = 4.3 Hash Algorithm = sha256 Engine = CAAM Engine Configuration = 0 Certificate Format = X509 Signature Format = CMS [Install SRK] File = "../crts/SRK_1_2_3_4_table.bin" Source index = 0 [Install CSFK] File = "../crts/CSF1_1_sha256_2048_65537_v3_usr_crt.pem" [Authenticate CSF] [Install Key] Verification index = 0 Target index = 2 File = "../crts/IMG1_1_sha256_2048_65537_v3_usr_crt.pem" [Authenticate Data] Verification index = 2 Blocks = 0x40200000 0x5AC00 0x7A2F0 "flash.bin", \ 0x910000 0xD4EF0 0xBED0 "flash.bin", \ 0x0 0xE0DC0 0x0 "flash.bin", \ 0x4027A2F0 0xE0DC0 0x61EF "flash.bin"
CSF for SPL image:
[Header] Version = 4.3 Hash Algorithm = sha256 Engine = CAAM Engine Configuration = 0 Certificate Format = X509 Signature Format = CMS [Install SRK] File = "../crts/SRK_1_2_3_4_table.bin" Source index = 0 [Install CSFK] File = "../crts/CSF1_1_sha256_2048_65537_v3_usr_crt.pem" [Authenticate CSF] [Install Key] Verification index = 0 Target index = 2 File = "../crts/IMG1_1_sha256_2048_65537_v3_usr_crt.pem" [Authenticate Data] Verification index = 2 Blocks = 0x7e0fd0 0x1a000 0x26400 "flash.bin" Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The problem is familiar to RNG self test issue, but this issue was not reported for i.MX8.
Please create request.
Regards,
Yuri.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Yuri.
I'll give it a try...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Yuri,
Returning back to this issue after some time...
I've taken the latest version of CST (3.1.0) but unfortunately I see the same results. I added some log messages in u-boot code to figure out what is happening and based on the outputs I understand that I probably have some HAB events, however it is failing to be reported. On hab.c, inside the function hab_rvt_report_event there is a call to call_imx_sip that fails with error code 0x33 (HAB_FAILURE), and this aborts the report.
Do you have any idea or direction?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
In order to check Events generated by HAB there are various methods that can be used:
1. In u-boot, run hab_status command. Also, HAB persistent memory can be read and parsed to get these events (in case hab_status command is not available)
md.b <0xPERSISTENT_MEMORY_ADDR> <0xSIZE>
2. Connect JTAG and dump the HAB persistent memory region.
3. If chip is in Serial download mode due to Authentication failure, USB Serial download protocol can be used to read HAB persistent memory region.
Refer to section 3 (HAB Persistent Data) of app note "HABv4 RVT Guidelines and Recommendations"
for some details.
https://www.nxp.com/docs/en/application-note/AN12263.pdf
Regards,
Yuri.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
below some comments regarding the issue.
1.
Please try using the recent CST 3.1.0
2.
There is no more documentation about i.MX8 HAB available now.
Check periodically the i.MX8M Summary page for new documentation, app notes.
i.MX 8M Applications Processor | Arm® Cortex®-A53, Cortex-M4 | 4K display resolution |NXP
Have a great day,
Yuri
------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer
button. Thank you!