- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- General Purpose Microcontrollers
- :
- LPC Microcontrollers
- :
- LPC55S69 DICE
LPC55S69 DICE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LPC55S69 DICE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Our goal is to use DICE with the LPC55S69 in secure IoT applications. According to the DICE specification, the DICE should combine the UDS with the measurement of "the first mutable code" to be executed to generate the CDI. Our goal would have been, that DICE measures the first piece of our code in the secure world and creates the CDI out of the UDS and this code.
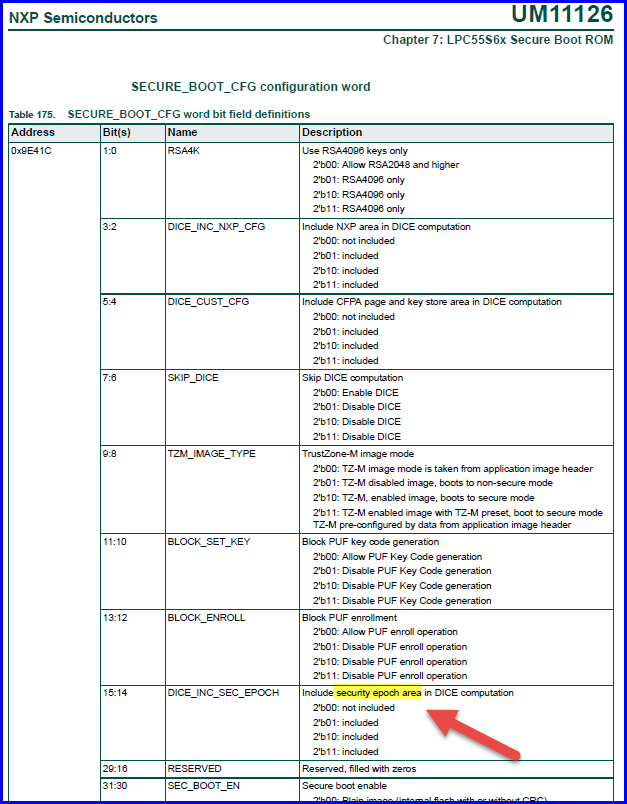
However, in the user manual I found nothing on how DICE can measure the first mutable code. The only possibilities I found to adjust the behaviour are the configuration possibilities to specify to "Include NXP Area", "Include CFPA page and key store area" and to "Include security epoch area" in the DICE computation.
The NXP Area and CFPA page are not "the first mutable code" according to my understanding. About the "security epoch area" I did not find another mention in the user manual or in any application note.
My questions therefore are 1) what is the "Security Epoch Area" and where can I find documentation about it 2) Is there any documentation I am missing about DICE apart from the few lines in the user manual 3) Is it possible to include the first piece of user code in the flash in the DICE computation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Simon Ott
I checked with application team. LPC55S69 is a very new chip. So far besides user manual, we don’t have other article document the usage of DICE. There is no demo code either.
What I know is that Microsoft developed a set of DICE package code, if you want to know more about its usage, you can check here:
https://www.microsoft.com/en-us/research/project/dice-device-identifier-composition-engine/
Yes, We can use user code image to generate Hash code, using this hash code with UDS key to generate DICE CDI.
Regarding to "Security Epoch Area", I checked there is no place documenting it. I will check it with design. If I get feedback, I will let you know.
Have a great day,
Jun Zhang
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Security Epoch Area" is mentioned in the UM.
The original plan is not open DICE function to end customer. The register should part of DICE.So you may ignore it. user can still use DICE to generate CDI without problem.
If this information is necessary for you, please let me now why you need know this for your project. thus we can ask designer for it.
Have a great day,
Jun Zhang
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding your answer "Yes, We can use user code image to generate Hash code, using this hash code with UDS key to generate DICE CDI.":
Is it correct, that DICE can only be used in combination with secure boot and a signed image, and that this signed image is used to generate the hash code for the CDI (in combination with UDS)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, right.
There is an important formula for DICE:
CDI = HMAC( UDSKey, SHA2(SBL_IMG));
Here,
SBL_IMG = L0_IMG without L0_Signature
CDI allows a host to verify the trustworthiness of an embedded device
UDS is index 15 key retrieved using key code from key store (generated during provisioning/manufacturing)
Have a great day,
Jun Zhang
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------