- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Home
- :
- General Purpose Microcontrollers
- :
- Kinetis Microcontrollers
- :
- Exception vectors to bootloader
Exception vectors to bootloader
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Exception vectors to bootloader
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've just spent a few hours debugging an issue on a KL17 that was driving me crazy. I want to preface this by saying it's resolved. Once I power cycled the part everything worked fine, but I'm still perplexed as to what was going on in case I have future issues like this.
Here's the scenario:
I connected to the KL17 using IAR and a J-Link debugger. The debugger dropped me at the application's reset vector and everything looked great. I ran the application and nothing happened. Hitting the break button, the debugger showed that execution was in the bootloader on a jump-to-self instruction. I reset and stepped through and managed to get all the way to MQX start when it sets PendSV and prepares to start the Main Task. As soon as interrupts are enabled, execution ended up at the same address.
I checked to see if it was stepping to that instruction, but no, it jumped directly to that address. The SCB indicated that the PendSV exception was active (and SysTick was pending behind it). I double checked the vector table at 0x00000000, and double checked that VTOR was indicating that the table was at address 0. That all checked out. It wasn't until I power cycled the system that everything started working.
Here's what I suspect: this was the first time this chip had been programmed, meaning it would have been sitting in the ROM bootloader when I connected with the debugger. I suspect that for whatever reason the core was still using the bootloader's vector table (at 0x1C000000). Checking the memory there, I did find that the address I was ending up at (the infinite loop) was used for the NMI, SVC and PendSV handler address (presumably a "not used" handler).
I can't for the life of me figure out how the wrong table was being used, though. Are there any registers or controls that I've missed that may have stealth remapped the vector table?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Ryan Powers:
Your own explanation makes sense. In a blank KL17 the ROM bootloader is executed in a loop waiting for communication in one of the available peripherals. During this time ROM vectors are used. Before jumping to the application the ROM bootloader performs these operations:
- Relocate VTOR to start of flash.
- Clear RCM_FM[FORCEROM] and RCM_RM[BOOTROM] bits.
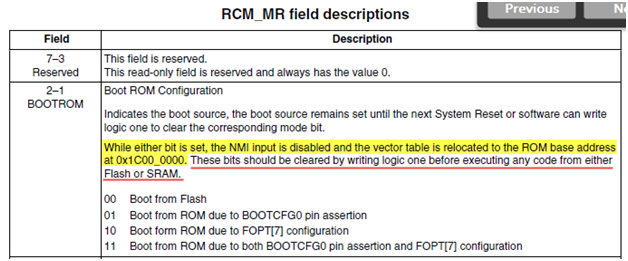
When the Jlink connection takes control of the KL17, does not allow such operations to happen. See the description of RCM_MR register below:
So, the vectors from ROM are still used until the next boot from flash or until the bootloader restores the RCM registers and the VTOR value without intervention from the debugger.
Regards!
Jorge Gonzalez