- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Home
- :
- i.MX Forums
- :
- i.MX RT
- :
- rt1052开启HAB后,使用nxp mcu bootutility串口启动无法连接flashloader
rt1052开启HAB后,使用nxp mcu bootutility串口启动无法连接flashloader
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
rt1052开启HAB后,使用nxp mcu bootutility串口启动无法连接flashloader
04-18-2023
08:49 PM
790 Views
Evanee
Contributor I
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
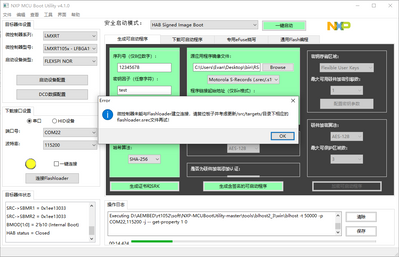
看控制台信息,感觉flashloader已经签名成功了,并且下载、跳转到芯片,不知道为什么连接不上。我使用的是核心板和底板组合的板子,换一个没开启HAB的核心板,可以正常下载,说明flashloader本身没有问题。打开自动生成的为flashloader签名的bd文件,没看出什么问题,希望寻求帮助。
控制台信息如下:
executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- error-status
toolStatus: 0
commandOutput: {
"command" : "error-status",
"response" : [ 4042322160 ],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1075790864 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1075790880 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1074757636 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1074757660 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1074757660 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\elftosb4\win>"D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\elftosb4\win\elftosb.exe" -f imx -V -c "D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\gen\bd_file\imx_flashloader_gen.bd" -o "D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\gen\bootable_image\ivt_flashloader_signed.bin" "D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\src\targets\MIMXRT1052\flashloader.srec"
CSF Processed successfully and signed data available in csf.bin
Section: 0x14
Section: 0x15
Section: 0x16
Section: 0x18
Section: 0x19
Section: 0x1a
Section: 0x1f
Section: 0x21
iMX bootable image generated successfully
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- write-file 539001344 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\gen\bootable_image\ivt_flashloader_signed.bin
toolStatus: 0
commandOutput: {
"command" : "write-file",
"response" : [ 3351091 ],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
自动生成的bd文件如下
options {
flags = 0x08;
startAddress = 0x20208200;
ivtOffset = 0x0;
initialLoadSize = 0x200;
entryPointAddress = 0x2021b26d;
}
sources {
elfFile = extern(0);
}
constants {
SEC_CSF_HEADER = 20;
SEC_CSF_INSTALL_SRK = 21;
SEC_CSF_INSTALL_CSFK = 22;
SEC_CSF_INSTALL_NOCAK = 23;
SEC_CSF_AUTHENTICATE_CSF = 24;
SEC_CSF_INSTALL_KEY = 25;
SEC_CSF_AUTHENTICATE_DATA = 26;
SEC_CSF_INSTALL_SECRET_KEY = 27;
SEC_CSF_DECRYPT_DATA = 28;
SEC_NOP = 29;
SEC_SET_MID = 30;
SEC_SET_ENGINE = 31;
SEC_INIT = 32;
SEC_UNLOCK = 33;
}
section (SEC_CSF_HEADER;
Header_Version="4.2",
Header_HashAlgorithm="sha256",
Header_Engine="DCP",
Header_EngineConfiguration=0,
Header_CertificateFormat="x509",
Header_SignatureFormat="CMS"
)
{
}
section (SEC_CSF_INSTALL_SRK;
InstallSRK_Table="../../../gen/hab_cert/SRK_1_2_3_4_table.bin",
InstallSRK_SourceIndex=0
)
{
}
section (SEC_CSF_INSTALL_CSFK;
InstallCSFK_File="../../cst/crts/CSF1_1_sha256_2048_65537_v3_usr_crt.pem",
InstallCSFK_CertificateFormat="x509"
)
{
}
section (SEC_CSF_AUTHENTICATE_CSF)
{
}
section (SEC_CSF_INSTALL_KEY;
InstallKey_File="../../cst/crts/IMG1_1_sha256_2048_65537_v3_usr_crt.pem",
InstallKey_VerificationIndex=0,
InstallKey_TargetIndex=2)
{
}
section (SEC_CSF_AUTHENTICATE_DATA;
AuthenticateData_VerificationIndex=2,
AuthenticateData_Engine="DCP",
AuthenticateData_EngineConfiguration=0)
{
}
section (SEC_SET_ENGINE;
SetEngine_HashAlgorithm = "sha256",
SetEngine_Engine = "DCP",
SetEngine_EngineConfiguration = "0")
{
}
section (SEC_UNLOCK;
Unlock_Engine = "SNVS",
Unlock_features = "ZMK WRITE"
)
{
}
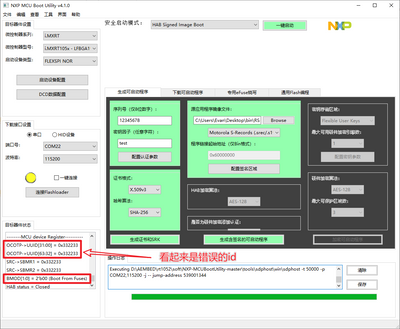
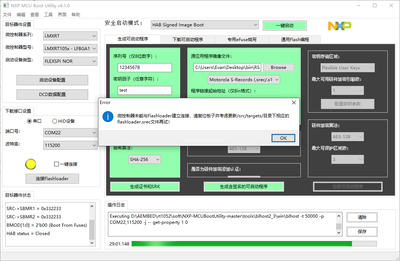
nxp-mcu bootutility报错截图如下:
但实际上,按键配置的是BMOD[1:0]=2'b01(serial downloader)
比较多的时候,启动模式会识别成BMOD[1:0]=2'b00(boot from fuse)
很少时候会是BMOD[1:0]=2'b10(internal boot)
然后识别到的UUID看起来也是不正常的
非常奇怪,从来不会把启动模式识别为BMOD[1:0]=2'b01(serial downloader)
ps:换成没有配置HAB的核心板,每次都能正常识别为BMOD[1:0]=2'b01(serial downloader)
3 Replies
04-20-2023
05:47 PM
765 Views
NXP Employee
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
控制台命令截图不太完整,write-file 后面没有命令了吗?
05-03-2023
07:56 PM
677 Views
Evanee
Contributor I
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
能不能再帮忙看一下,是什么原因?
04-21-2023
06:03 PM
755 Views
Evanee
Contributor I
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
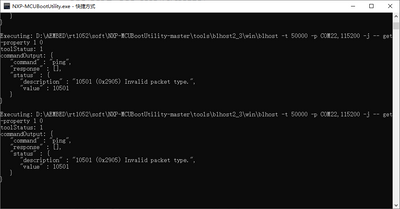
控制台完整截图以及内容如下:
xecuting: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- error-status
toolStatus: 0
commandOutput: {
"command" : "error-status",
"response" : [ 4042322160 ],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1075790864 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1075790880 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1074757636 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1074757660 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- read-register 1074757660 32 4 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\vectors\readReg.dat
toolStatus: 0
commandOutput: {
"command" : "read-register",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\elftosb4\win>"D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\elftosb4\win\elftosb.exe" -f imx -V -c "D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\gen\bd_file\imx_flashloader_gen.bd" -o "D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\gen\bootable_image\ivt_flashloader_signed.bin" "D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\src\targets\MIMXRT1052\flashloader.srec"
CSF Processed successfully and signed data available in csf.bin
Section: 0x14
Section: 0x15
Section: 0x16
Section: 0x18
Section: 0x19
Section: 0x1a
Section: 0x1f
Section: 0x21
iMX bootable image generated successfully
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- write-file 539001344 D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\gen\bootable_image\ivt_flashloader_signed.bin
toolStatus: 0
commandOutput: {
"command" : "write-file",
"response" : [ 2290649224 ],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\sdphost\win\sdphost -t 50000 -p COM22,115200 -j -- jump-address 539001344
toolStatus: 0
commandOutput: {
"command" : "jump-address",
"response" : [],
"status" : {
"description" : "305411090 (0x12343412) HAB enabled.",
"value" : 305411090
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\blhost2_3\win\blhost -t 50000 -p COM22,115200 -j -- get-property 1 0
toolStatus: 1
commandOutput: {
"command" : "ping",
"response" : [],
"status" : {
"description" : "10501 (0x2905) Invalid packet type.",
"value" : 10501
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\blhost2_3\win\blhost -t 50000 -p COM22,115200 -j -- get-property 1 0
toolStatus: 1
commandOutput: {
"command" : "ping",
"response" : [],
"status" : {
"description" : "10501 (0x2905) Invalid packet type.",
"value" : 10501
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\blhost2_3\win\blhost -t 50000 -p COM22,115200 -j -- get-property 1 0
toolStatus: 1
commandOutput: {
"command" : "ping",
"response" : [],
"status" : {
"description" : "10501 (0x2905) Invalid packet type.",
"value" : 10501
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\blhost2_3\win\blhost -t 50000 -p COM22,115200 -j -- get-property 1 0
toolStatus: 1
commandOutput: {
"command" : "ping",
"response" : [],
"status" : {
"description" : "10501 (0x2905) Invalid packet type.",
"value" : 10501
}
}
Executing: D:\AEMBED\rt1052\soft\NXP-MCUBootUtility-master\tools\blhost2_3\win\blhost -t 50000 -p COM22,115200 -j -- get-property 1 0
toolStatus: 1
commandOutput: {
"command" : "ping",
"response" : [],
"status" : {
"description" : "10501 (0x2905) Invalid packet type.",
"value" : 10501
}
}