- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
关于P2020长地址跳转问题
你好!
我在codewarrior下,通过L2 SRAM运行一级boot跳转到0x7fe00500的二级boot地址,无法跳转,调试发现在汇编指令生成的指令是调用bctrl进行的,跳转地址0x7fe00500的值已写到cout寄存器,但PC指针为0;地址空间0x0000_0000 --0x3fff_ffff和0x4000_0000 - 0x7fff_ffff的TLB属性是一致无法跳转,将SX等属性全部打开也不行;但是跳转到0x1fe00500地址是可以的。使用仿真器调试时时可以的,自动运行无法跳转。
> 2.SDK version:
> - CodeWarrior for Power Architecture
> Version: 10.5.1
> Build Id:160128
SDK means Linux Software Development Kit - not CodeWarrior IDE.
Provided pictures have bad resolution - almost unreadable.
Hi!
I have count a problem when i run the first-level boot jump to the second-level boot address of 0x7fe00500, and cannot jump. Debugging finds that the instruction generated in assembly instruction is called BCTRL, and the value of jump address 0x7fe00500 has been written to the count register, but the PC pointer is 0.Address space 0x0000_0000 --0x3fff_ffff and 0x4000_0000-0x7fff_ffff TLB attribute is the same cannot jump, SX and other attributes all open is not ok;But it's ok to jump to 0x1fe00500 or 0x3fe00500.Using the simulator debugging can be, automatic running can not jump.
The address 0x7fe00500 is avilable for access,and can pritf the jump instruction.
TLB value :
0xa0007fc0fc0800000000000000000001 for 0x0000_0000 --0x3fff_ffff
0xa0007fc0fc0800004000000040000001 for 0x4000_0000-0x7fff_ffff
Is SDRAM accessible in the range 0x4000_0000-0x7fff_ffff ?
You wrote:
> NXP SDK : P2020DS for sram
What is the exact SDK revision?
> assembly instruction is called BCTRL, and the value of jump address
> 0x7fe00500 has been written to the count register,
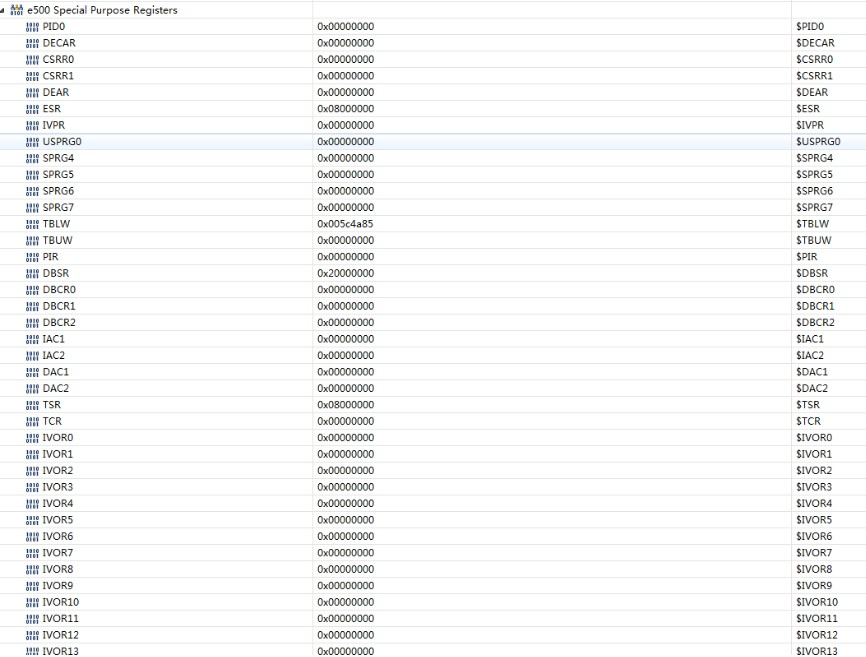
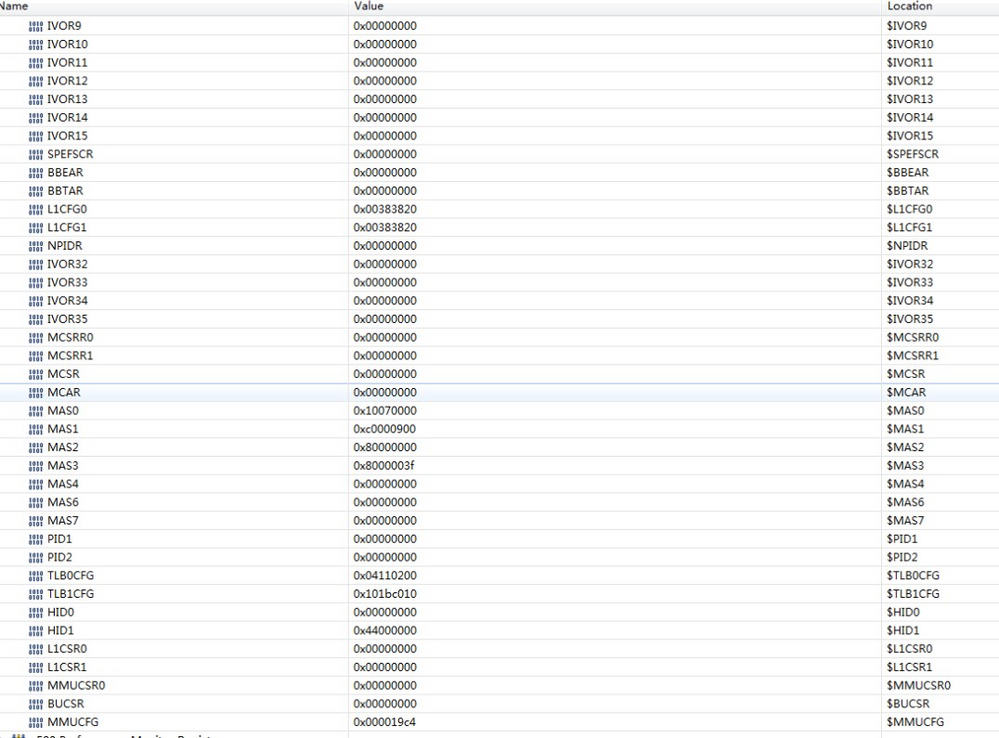
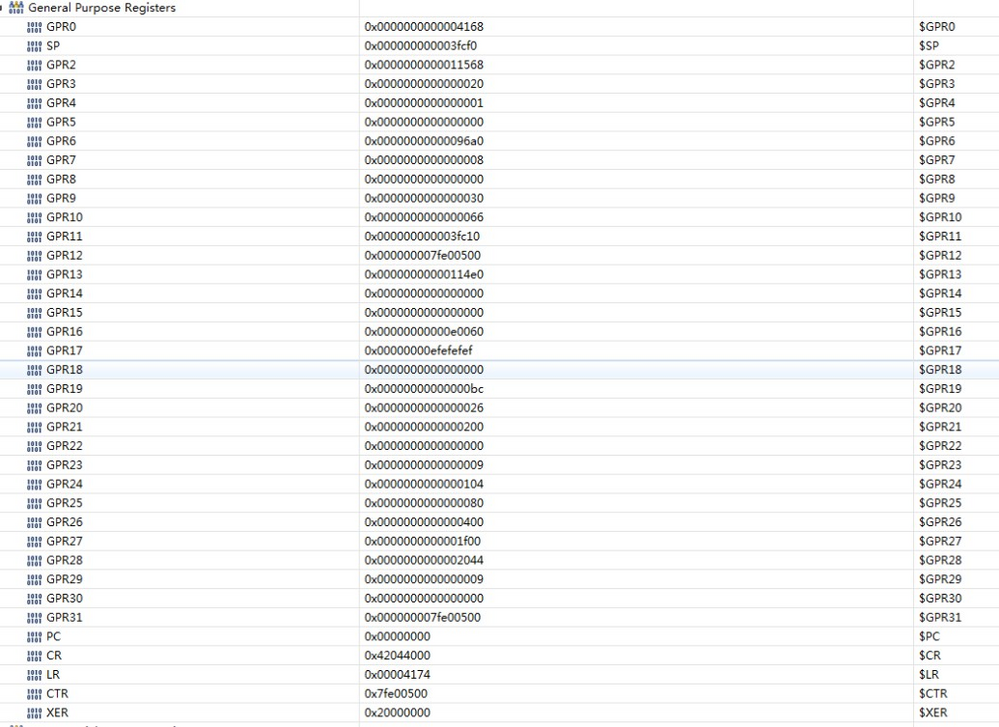
Please provide the assembler code excerpt and dump of the processor's registers when breakpoint is set on the branch instruction.
What happens after single step through the BCTRL? + one more dump of the processor's registers.
1.SDRAM is accessible in the range 0x4000_0000-0x7fff_ffff ;
2.SDK version:
- CodeWarrior for Power Architecture
Version: 10.5.1
Build Id:160128
3.The jump address is 0x7fe00500,and before jump i can printf the vaule of 0x7fe00500;
4.
C code:
#define BOOT_BASE_ADDR 0x7fe00000
entry bootentry = (entry)(BOOT_BASE_ADDR+0x500);
printf("goto 0x%x 0x%x...\n\r",bootentry,*(UINT32*)bootentry);
/* gotoBootrom();*/
bootentry();
Autorun printf:
bootrom copy down...
goto 0x7fe00500 0x480ff301...
The assembly instrucion :
E:\Freescale\CW_PA_v10.5.1\workspace\2020_sram-core00\Sources\/main_SRAM.c:429
4168: 7f ec fb 78 mr r12,r31
416c: 7d 89 03 a6 mtctr r12
4170: 4e 80 04 21 bctrl
The exact register vaule is follow: