- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- Wireless ConnectivityWireless Connectivity
- RFID / NFCRFID / NFC
- Advanced AnalogAdvanced Analog
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
- S32Z/E
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- Generative AI & LLMs
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
- RFID / NFC
- Advanced Analog
-
- NXP Tech Blogs
- Home
- :
- General Purpose Microcontrollers
- :
- LPC Microcontrollers
- :
- Re: LPC55S69: Secure boot, debug and programming the other fields of CFPA/CMPA
LPC55S69: Secure boot, debug and programming the other fields of CFPA/CMPA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I managed to generate and flash a secure boot 2 capsule, so far so good
But i raised 2 questions :
Q1: Other fields of CMPA/CFPA
---------------------------------------------
There are some parts that are a bit unclear , for example the BOOT_CFG/SPI_CFG/SDIO_CFG fields ?
The SECURE_BOOT_CFG is detailed both in the UM and the secure boot Application note, but i couldnt locate the details of the ones above
Any hint for these would be appreciated.
Q2 Debugging
--------------------
My test App works fine in "plain" mode but crashes pretty quickly in "secure boot" mode.
TrustZone is NOT enabled, it crashes as soon as FreeRTOS is started.
By default, debug is not possible with a secure boot firmware. I suppose it's due to the field CC_SOCU_PIN & CC_SOCU_DFLT being both to zero so debug is disabled by default.
Is that the case ?
I tried to enable it (CC_SOCU_PIN=1F 00 00 00 and CC_SOCU_DEFLT=00 00 00 00 in CMPA), but it didnt work and actually sort of bricked the board
So the 2nd question :
What is the right way to enable debug over SWD in secure boot mode , when you dont care about securing the debug link ? (that will happen later)
Thank you in advance
Tres
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
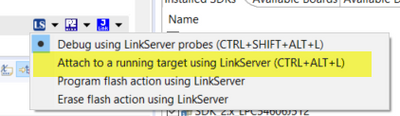
Yes, it can't erase and program, you can also test Attach function to debug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
Thank you for your reply,
Q1: It is mentioned in the AN12283 (secure boot) page 8 (it is also mentioned in the LPC55S6x user manual)
They are field No 0 and 1 of CMPA header (offset 0 & 4)
Q2: Unfortunately i cannot get the board to go to ISP mode any longer. I'm afraid i've really bricked it. I bought a few in advance, not a real problem.
But the question 2 stands : How to enable SWD debug (without authentication) when secure boot is enabled ? So that i can debug why it crashes only when secure boot is enabled ?
Thank you in advance
Tres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Tres,
Q1, yes there isn't more description about "SPI_CFG/SDIO_CFG", I think this is a issue in UM, I will
take a ticket about this, thanks for your sharing.
Q2, If you haven't config the CC_SOCU part, after successful enable secure boot, the debug function can work well. If enable secure boot failed, the debug also can't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your reply
This is what i tried
CC_SOCU_PIN= 0x1F 00 00 00
CC_SOCU DEFLT= 00 00 00 00
I though that would enable debug by default on all domains, but it seems that did exactly the opposite.
What would be the value to put in SOCU_PIN & SOCU_DEFAULT to enable all debug by default ?
My aim is to do debugging to check why it crashes in secure boot and not in "plain" mode
Thank you in advance
Tres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Tres,
1) "I though that would enable debug by default on all domains,"
-> Yes, do not config "CC_SOCU_PIN/CC_SOCU DEFLT", then every domains can debug.
2) While if enable secure boot failed, no matter how to config , no domains can debug.
About enable secure boot, please strictly fellow up the
https://www.nxp.com.cn/docs/en/application-note/AN12283.pdf
Regards,
Alice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
Thank you for your reply
The secure boot *is* working
The problem is the app is crashing quickly in secure boot mode, and it is working fine in non secure boot mode
I 'm looking for a way to debug the app in secure boot mode, so that i can check why it crashes and fix it
It's fine if i have to lower the overall security temporarily
Any help would be appreciated
Best Regards
Tres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello trescurieux,
How do you know "The secure boot *is* working" ?
If the secure boot configure well, and program a SB2 file (APP+singed+security), it can work well.
And at this time, also can debug(Do not erase,program, just debug).
Regards,
Alice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
Thank you for you reply
Indeed, i will retry and disable erase/program in the debugger, that might be the main issue
Tres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it can't erase and program, you can also test Attach function to debug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know it's working because i have some debug statement in the console
So i know :
* that secure boot is accepting my fw (else it would go to isp mode)
* it's starting to boot (the serial messages)
But it crashes very quickly after that.
My guess is that some things are not initialized properly and the chip configuration is different if you use secure boot or not.
Since it is not re-initialized properly by my app, it crashes
(the app is just running freeRTOS and blinking one of the onboard LED)
Tres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed the "attach to running" method worked
Just need to figure out why it crashes now
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello trescurieux,
Q1: Please tell me where is "SPI_CFG/SDIO_CFG" you mentioned.
Q2: If you haven't enable"Seal security configuration ", you can try to program a empty file to CMPA
refer to:
Until the CMPA is not sealed (HASH of CMPA written), you can change the configuration. The empty CMPA isattached. Use "blhost -p COMxx write-memory 0x9E400 CMPA_empty.bin". This is not applicable to the LPC55S69 0Asilicon.
Regards,
Alice