- Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
- S32M
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
- MCUXpresso Training Hub
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Knowledge Bases
- ARM Microcontrollers
- i.MX Processors
- Identification and Security
- Model-Based Design Toolbox (MBDT)
- QorIQ Processing Platforms
- S32 Automotive Processing Platform
- Wireless Connectivity
- CodeWarrior
- MCUXpresso Suite of Software and Tools
- MQX Software Solutions
-
- Home
- :
- Identification and Security
- :
- Secure Authentication
- :
- Re: Broken pkcs11 sign and verify in SDK SE05x-MW-v04.03.00
Broken pkcs11 sign and verify in SDK SE05x-MW-v04.03.00
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Broken pkcs11 sign and verify in SDK SE05x-MW-v04.03.00
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
In latest SDK SE05x-MW-v04.03.00 pkcs11 sign and verify functionalities are broken.
Steps to re-produce,
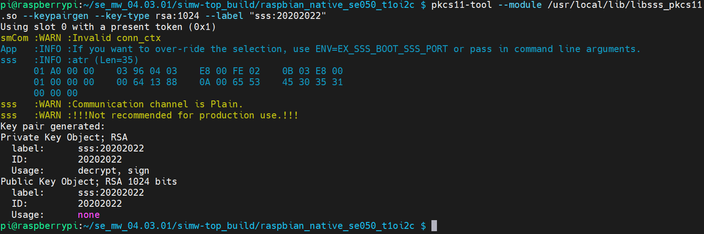
pkcs11-tool --module /usr/lib/libsss_pkcs11.so --keypairgen --key-type rsa:1024 --label "sss:20202020"
pkcs11-tool --module /usr/lib/libsss_pkcs11.so --sign --label sss:20202020 -m SHA256-RSA-PKCS --slot 1 -i in.der -o rsa-signature.der
Regards
Vishwa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @vishwanchandapu ,
I just got the latest MW v04.03.01 and tried your example with it, and looks like this issue got fixed in the latest version. Please kindly refer to the following for details.
but I don't have the in.der file for further verification, maybe you can share it with me or tell me how to generate this file?
Thanks for your patience!
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Look like in latest build it is NOT fixed.
Regarding "in.der" that is any dummy input file.
You can create using linux command.
cat "Test 1234" > in.der
Regards
Vishwa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, such kind of mutiple sign operation has not been supported but will be implemented in the future, for now you may split it into separate steps – first generate the digest, then do the signing, which may avoid using C_SignUpdate. Please kindly refer to the attachment for details.
Hope that makes sense,
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @vishwanchandapu ,
Would you please specify the platform as well as the se05x variant used in your tests? I may try to reproduce this issue here.
Thanks for your patience!
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Kan_Li
Thank for your response.
Platform: linux
Variant :0x051C.
I think we have fix this, is there any way we can submit the patch?
Regards
Vishwa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @vishwanchandapu ,
Good to know that! Yes, you may submit a private ticket for that topic, please refer to the following for details.
https://www.nxp.com/video/tutorial-for-nxp-support-case-portal:NCP-VIDEO
I also noticed you has posted another thread in https://community.nxp.com/t5/Secure-Authentication/C-GetAttributeValue-EC-PARAMS-failed-for-EC-secp5... , and if that is also the case, you may create a private ticket for it as well.
Have a great day,
Kan
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------