- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- i.MX Forums
- :
- i.MX Processors
- :
- hab_auth_img problem
hab_auth_img problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
hab_auth_img problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am using imx8mm-evk.
I am trying to sign a Kernel image and verify its signature from u-boot with command hab_auth_img.
I followed the instruction at mx8m_mx8mm_secure_boot.txt\guides\habv4\imx\doc - uboot-imx - i.MX U-Boot , chapter 2.
I am not sure I interpreted correctly what in that page they call "load Address" in the genIVT.pl script , is that meaning the Image load address or the IVT load address ?
I filled it in with my image load address. So my genIVT.pl is now :
#! /usr/bin/perl -w
use strict;
open(my $out, '>:raw', 'ivt.bin') or die "Unable to open: $!";
print $out pack("V", 0x412000D1); # Signature
print $out pack("V", 0x40480000); # Load Address (*load_address)
print $out pack("V", 0x0); # Reserved
print $out pack("V", 0x0); # DCD pointer
print $out pack("V", 0x0); # Boot Data
print $out pack("V", 0x41AF6000); # Self Pointer (*ivt)
print $out pack("V", 0x41AF6020); # CSF Pointer (*csf)
print $out pack("V", 0x0); # Reserved
close($out);
I considered self pointer to be set to 0x41AF6000 because I calculated that as Load Address + Image size after padding (0x01676000 ) .
+32 bit and I get also CSF pointer .
Is this interpretation correct ?
Now I have the csf_additional.txt :
[Authenticate Data]
# Key slot index used to authenticate the image data
Verification index = 2
# Authenticate Start Address, Offset, Length and file
Blocks = 0x40480000 0x00000000 0x01676000 "Image-imx8mmevk_pad_ivt.bin"
Is this correct ? I put length of file excluding IVT table but including padding. Or should I put length including ivt.bin ( length of the full Image-imx8mmevk_pad_ivt.bin file ) here ? OT excluding both IVT and padding ?
at u-boot prompt then :
u-boot=> fatload mmc 1:1 0x40480000 Image-imx8mmevk_signed.bin
23555936 bytes read in 275 ms (81.7 MiB/s)
u-boot=> hab_auth_img 0x40480000 0x1676000 0x41AF6000
hab fuse not enabled
Authenticate image from DDR location 0x40480000...
bad magic magic=0x0 length=0x00 version=0x0
bad length magic=0x0 length=0x00 version=0x0
bad version magic=0x0 length=0x00 version=0x0
Error: Invalid IVT structure
Allowed IVT structure:
IVT HDR = 0x4X2000D1
IVT ENTRY = 0xXXXXXXXX
IVT RSV1 = 0x0
IVT DCD = 0x0
IVT BOOT_DATA = 0xXXXXXXXX
IVT SELF = 0xXXXXXXXX
IVT CSF = 0xXXXXXXXX
IVT RSV2 = 0x0
I tried also with
u-boot=> hab_auth_img 0x40480000 0x1676F60 0x41AF6000 ( 0x1676F60 is the full file size including ivt part ).
But I got same error
Please see also attachments
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am using a customized board of i.MX8MP and I am stuck at the same point
The loadaddr for imx8mp is 0x40480000
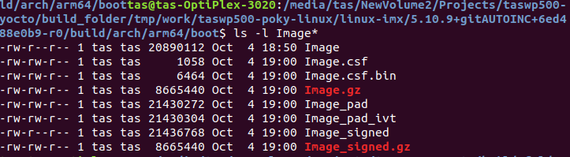
I have the following files generated
I am trying to authenticate the image with
hab_auth_img <kernel load address> <size image+ivt+csf> <ivt offset>
hab_auth_img 0x4048000 0x1471960 0x418f000
where
0x40480000 - loadaddr
0x1471960 - hex value of Image_signed ( Image + ivt + csf )
0x1470000 - hex value of ivt offset ( Image + pad )
But I am still getting error of invalid IVT structure.
Where am I going wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hab_auth_img <kernel load address> <size image+ivt+csf> <ivt offset>
u-boot=> hab_auth_img 0x40400000 0x1df0f68 0x1df0000
Authenticate image from DDR location 0x40400000...
Secure boot enabled
HAB Configuration: 0xcc, HAB State: 0x99
No HAB Events Found!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
1.
The "load Address" in the genIVT.pl is the Image load address.
2.
The diagram below illustrate the Image layout:
------- +-----------------------------+ <-- *load_address
^ | |
| | |
| | |
| | |
| | Image |
Signed | |
Data | |
| | |
| +-----------------------------+
| | Padding to Image size |
| | in header |
| +-----------------------------+ <-- *ivt
v | Image Vector Table |
------- +-----------------------------+ <-- *csf
| |
| Command Sequence |
| File (CSF) |
| |
+-----------------------------+
| Padding (optional) |
+-----------------------------+
Pay attention on the Signed Data - Image, Padding to Image size in header,
and IVT are included in the signed area.
Regards,
Yuri.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok I made it working, I had missed the diagram.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello, i have the same problem, could you tell me how you soved it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi..it would be helpful If you could let me know the solution...I followed exactly like in document... secure boot is fine but cannot get signed kernel image working... could you please share what you did to make it work...(like csf and genivt file)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just following correctly the document at mx8m_mx8mm_secure_boot.txt\guides\habv4\imx\doc - uboot-imx - i.MX U-Boot ,that has the same diagram that was posted up here, should make it working. Following correctly both when signing and when verifying the signatures, I haven't modified anything on that document to make it working.