- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- General Purpose Microcontrollers
- :
- LPC Microcontrollers
- :
- LPC55S69 Signed Image Boot - Questions on using Certificate Chains?
LPC55S69 Signed Image Boot - Questions on using Certificate Chains?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
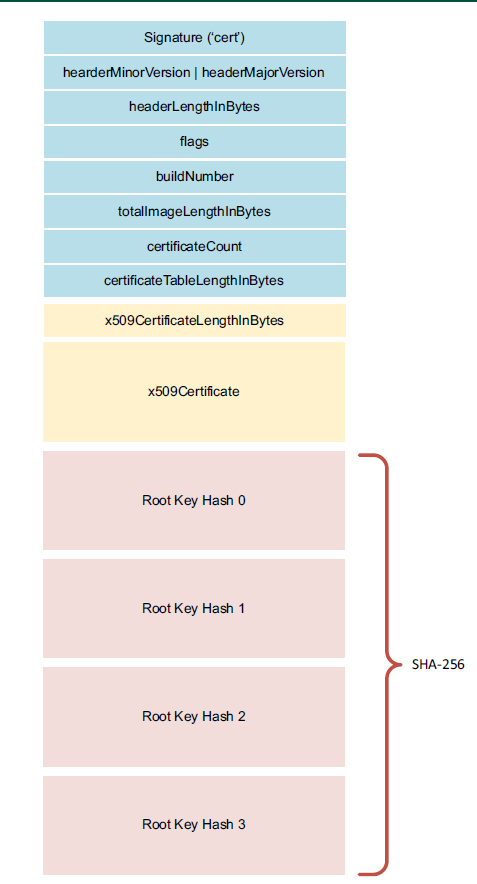
I've read through Application Note 12283 (LPC55Sxx Secure Boot) and am trying to work through exactly how a certificate chain, if it is used, is walked on the processor. My confusion is that the App Note only ever talks about one certificate - the root. It mentions in section 3.4 that you can and should create a certificate chain, but then, how does the ROM validate the chain? Figure 5 (Signed image format) only shows one x509 certificate that would be included in the firmware file. What if my chain has a root -> intermediary -> end entity? Is it expecting that one x509 certificate to include the entire chain in it? If so, are there any length restrictions? This just isn't clear :-(
Also, when generating certificate chains, there is the sequence id that has the revocation id, but each cert in the chain could have their own sequence numbers. What is best practice here? Should all of the sequence numbers in the chain be the same for the purpose of anti-rollback? Or, is only the end entity sequence number checked?
I'm sorry if these questions seem silly, but considering the probability of me bricking my dev kit is high if I make a mistake in this stuff, I'd rather ask silly questions than be left with a paperweight.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jeffrey,
Hope you are doing well.
I recommend to take a look at Chapter 7 of the reference manual. It explains with the details of what you are looking for, such as the structure, length, considerations, etc.
Specifically, section 7.3.5 where you will find the certificate block structure and its requirements and recommendations.
For the revocation ID, The x509 serial number field in the image signing certificate is used the following way: byte 0
shall be 0x3c, byte 1 shall be 0xc3, byte 2 and byte 3 form an unsigned 16-bit integer whose value is compared with the IMAGE_KEY_REVOKE value in the PFR. On mismatch, the image authentication process will fail.
The image signing certificate is the final certificate of the certificate table. It's not a problem if you use one certificate, for more details on the structure you can refer to the last part of section 7.3.5.2.
Hope this helps!
If you need any further information or have any further questions, please do not hesitate to get back to me.
Best Regards,
Sabina
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jeffrey,
Hope you are doing well.
I recommend to take a look at Chapter 7 of the reference manual. It explains with the details of what you are looking for, such as the structure, length, considerations, etc.
Specifically, section 7.3.5 where you will find the certificate block structure and its requirements and recommendations.
For the revocation ID, The x509 serial number field in the image signing certificate is used the following way: byte 0
shall be 0x3c, byte 1 shall be 0xc3, byte 2 and byte 3 form an unsigned 16-bit integer whose value is compared with the IMAGE_KEY_REVOKE value in the PFR. On mismatch, the image authentication process will fail.
The image signing certificate is the final certificate of the certificate table. It's not a problem if you use one certificate, for more details on the structure you can refer to the last part of section 7.3.5.2.
Hope this helps!
If you need any further information or have any further questions, please do not hesitate to get back to me.
Best Regards,
Sabina
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the pointer to the additional information in the UM. The explanation in the user manual that the "Certificate" is really a "Certificate Table" where it can contain multiple certificates was immensely helpful and cleared up a lot of my confusion around that.
And, from what I understand from your explanation, it is the revocation ID in the end entity (image signing certificate) that is used to enforce rollback protection. If I put any revocation IDs anywhere else up in the chain, they would be ignored.
If you get a chance to confirm my understanding, that would be great. Thanks so much for your reply!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
If I put any revocation IDs anywhere else up in the chain, they would be ignored.
Yes this is correct, it has to be the final certificate.
Not a problem, glad to help!
If you have any questions in the future don't hesitate to contact us again.
Best Regards,
Sabina
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------