- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- General Purpose Microcontrollers
- :
- Kinetis Microcontrollers
- :
- MMCAU SHA256
MMCAU SHA256
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MMCAU SHA256
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good morning
I run the example mmcau_api. I test the SHA256 with the proposed test vector. Here it is
static uint8_t g_testSha[TEST_LENGTH] = {0x54, 0x68, 0x65, 0x20, 0x71, 0x75, 0x69, 0x63, 0x6b, 0x20, 0x62, 0x72, 0x6f,
0x77, 0x6e, 0x20, 0x66, 0x6f, 0x78, 0x20, 0x6a, 0x75, 0x6d, 0x70, 0x73, 0x20,
0x6f, 0x76, 0x65, 0x72, 0x20, 0x74, 0x68, 0x65, 0x20, 0x6c, 0x61, 0x7a, 0x79,
0x20, 0x64, 0x6f, 0x67, 0x80, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x58};
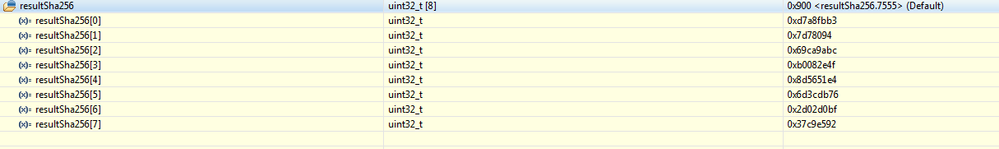
The result I get is
{3618175923, 131563668, 1774885564, 2953326159, 2371244516, 1832704886, 755159231, 935978386}
I test the same vector on line here https://www.fileformat.info/tool/hash.htm?hex=0x54%2C+++0x68%2C+0x65%2C+0x20%2C+0x71%2C+0x75%2C+0x69...
and I get the result
| d4b8527d7a673b096ba19aabfb458c357a43f008d214aac413ee18cf29485fe2 |
It does not match. So what is wrong???
Thank You
Pietro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Pietro
I checked in the uTasker project (supporting SW, mmCAN and LTC SHA256):
static const ALIGNED_BUFFER text = { 0,{0x54, 0x68, 0x65, 0x20, 0x71, 0x75, 0x69, 0x63, 0x6b, 0x20, 0x62, 0x72, 0x6f,
0x77, 0x6e, 0x20, 0x66, 0x6f, 0x78, 0x20, 0x6a, 0x75, 0x6d, 0x70, 0x73, 0x20,
0x6f, 0x76, 0x65, 0x72, 0x20, 0x74, 0x68, 0x65, 0x20, 0x6c, 0x61, 0x7a, 0x79,
0x20, 0x64, 0x6f, 0x67, 0x80, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x58} };
int i;
fnSHA256(text.ucData, recovered.ucData, 64, SHA_START_CALCULATE_TERMINATE);
for (i = 0; i < 32; i++) { // the HASH is always 32 bytes in length
fnDebugHex(recovered.ucData[i], (WITH_SPACE | sizeof(unsigned char) | WITH_LEADIN));
}
The output it gives is:
0xd4 0xb8 0x52 0x7d 0x7a 0x67 0x3b 0x09 0x6b 0xa1 0x9a 0xab 0xfb 0x45 0x8c 0x35 0x7a 0x43 0xf0 0x08 0xd2 0x14 0xaa 0xc4 0x13 0xee 0x18 0xcf 0x29 0x48 0x5f 0xe2
which matches with the one from your link.
1. It looks like you are displaying the result in decimal form - try displaying in hex instead.
2. Also ensure that you are displaying as a string of binary values rather than risking little-/big endian confusion.
3. If using mmCAU ensure that your buffers are long word aligned since the crypto accelerators tend to require this.
Regards
Mark
Complete Kinetis solutions, training and support: http://www.utasker.com/kinetis.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am also wandering what is the LTC SHA ???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pietro
LTC is the Low power trusted cryptography module found in some of Kinetis parts (it may be instead of mmCAU or it may be in addition to mmCAU, but it is only in a few parts).
I also had some difficulties with the SHA256 in mmCAU and needed to do additional research to get it working:
If you have access to the professional version of the uTasker project you can find the interface in crypto.c which handles all of the nuances (alignment, padding, endian-ness) needed by the various crypto accelerators.
Regards
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Mark
There is a good new now. I tried to use the wrapper of the wolfssl and it is working in this way. I will try to catch what is problem.
Thank You
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hei Mark
Good to find You here also.
I have tested the source code as is in the example and I expect it should work. I have here the FRDMK64 and the TOWER for the KV58.
Both of them give the same wrong result.
The HEX counterpart is here and it does not help. All of the buffers are correctly aligned.
That's the dump of the hex
If you have suggestionns are welcome.
Thank You
Pietro