- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- QorIQ Processing Platforms
- :
- QorIQ
- :
- SMC instruction, and PPA
SMC instruction, and PPA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SMC instruction, and PPA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
In my project I have to write my own bootloader instead of U-Boot for LS1043A, currently I'm working on the LS1043ARDB board. I have 2 issues I would like to ask about:
1. After I bring the processor to non-secure EL1 and try to call the smc #0 instruction, I get an serror exception (offset 0x380) - is there any thing I need to configure in order for smc to go to the appropriate synchroneous vector (offset 0x400) ? The VBAR registers have been pre-configured of course. Also when I call smc #0 from EL2, all is good and it goes to the sync vector. I assume that calling smc #0 from EL1 should be possible.
Another thing is, if I load from U-Boot, then calling smc #0 is ok from EL1 as well, so I guess U-Boot is doing something I don't somewhere, it's just that there are a multitude of initializations to be done, and I can put my finger on in in the U-Boot code - I would appreciate any help.
2. Assuming I get over the previous issue, I need then to load and initialize the PPA instead of U-Boot in order to have a secure monitor going. Can anyone say what is the procedure for loading and initializing the PPA?
Thanks in advance,
Yaron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Yaron Alterman,
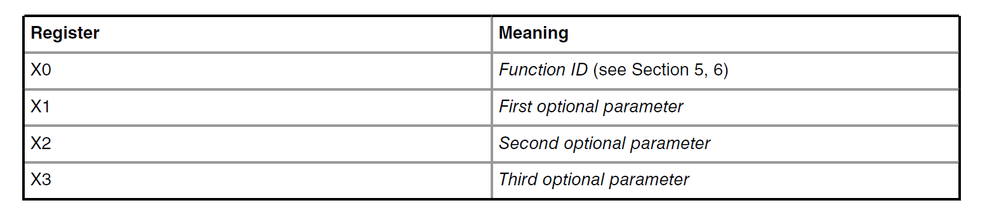
SMC functions treat registers x0-x12 as volatile, to call an SMC/PSCI function, load the registers according to the table below, then execute an “SMC 0x0” instruction. Please refer to "smc #0" invoking in the file arch/arm/cpu/armv8/sec_firmware_asm.S of u-boot source code.
The procedure for loading and initialize PPA.
1. The PPA must be loaded to a 64Kb boundary
2. Copy the binary image to the load address – the component installing the PPA MUST be executing at EL3
3. PPA should be loaded to an address in secure memory - recommend a 2MB secure region in DDR (but PPA can be tested in non-secure DDR)
4. After copying the image file to DDR, clean the data cache by VA (all virtual address ranges affected by PPA load) , and invalidate the instruction cache.
5. The PPA initialization runs at EL3 – but the PPA transfers control back to the address loaded in BOO TLOCPTR at EL2 –you must write the start address of the EL2 portion of your bootloader into BOOTLOCPTR before initializing the PPA.
6. After writing the EL2 start address in BOOTLOCPTR, initialize the PPA by branching to its start address
Have a great day,
TIC
-----------------------------------------------------------------------------------------------------------------------
Note: If this post answers your question, please click the Correct Answer button. Thank you!
-----------------------------------------------------------------------------------------------------------------------