- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
- Cloud Lab Forums
-
- Home
- :
- MCUXpresso Software and Tools
- :
- Kinetis Software Development Kit
- :
- K81 KSDK MBEDTLS RSA 2048 bit key check error
K81 KSDK MBEDTLS RSA 2048 bit key check error
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
K81 KSDK MBEDTLS RSA 2048 bit key check error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My current project requires RSA 2048 bit operations performed on K81 MCU.
I am using KSDK 2.1 and mbedtls 2.2.1.
I can successfully generate a RSA 2048bit key pair using mbedtls_rsa_gen_key function.
Then I perform mbedtls_rsa_check_privkey at the newly generated key.
The problem is that this check fails when the key is longer than 2016 bits, e.g 2044 or 2048bits
I followed the execution path like this:
bignum.c:mbedtls_rsa_check_privkey: Line 210: MBEDTLS_MPI_CHK( mbedtls_mpi_div_mpi( &L1, &L2, &H, &G2 ) );
bignum.c:mbedtls_mpi_div_mpi: Line 1400: MBEDTLS_MPI_CHK( mbedtls_mpi_sub_mpi( &X, &X, &T1 ) );
bignum.c:mbedtls_mpi_sub_mpi: Line 1043: MBEDTLS_MPI_CHK( mbedtls_mpi_sub_abs( X, A, B ) );
ksdk_mbedtls.c: mbedtls_mpi_sub_abs:
Line 767:
if ((sizeA > sizeN) || (sizeB > sizeN))
{
return MBEDTLS_ERR_MPI_BAD_INPUT_DATA;
}
mbedtls_mpi_sub_abs returns MBEDTLS_ERR_MPI_BAD_INPUT_DATA because the size of A and/or B (260 bytes) is greater than size of N (256 bytes), i.e. A.n (or B.n) == 0x41.
Apparently the maximum value(number of limbs) of A.n (or B.n) that can be handled by this function is 0x40.
It looks like at some point earlier in this execution path due to left shift the size of X is increased above 0x40.
My question is:
Is this limitation known to NXP and is it possible that this limitation could affect encryption/decryption functions when used with an RSA 2048bit keys ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
We don't make any limitation on this, LTC of K81 could support keysize up to 2048bit.
For RSA algorithm principle, A, B must be no more than N.
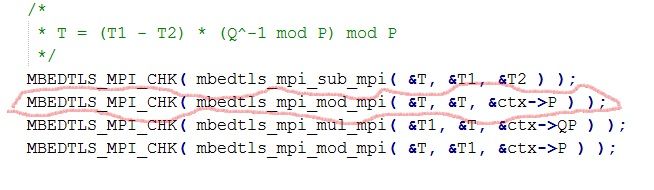
Upon my experience, there have a bug behind the line 406 of rsa.c when you enable CRT function.
See the below picture as reference:
If you also open CRT function, you could try it.
Best regards,
Juying
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Juying!
Thank you for your reply !
I will apply the suggested fix in the mbedtls_rsa_private function and will test it.
However, please note that the issue I reported is with the RSA key check function and AFAIK there is an updated KSDK version which deals with it and is not related to the K81 capability to handle 2048bit operands in the LTC module. It is the MBEDTLS library which fails to stick to max 2048bit operands.
This issue is detected with keys generated with various PC software and imported in the K81 firmware. It is clearly linked to the size of the key.
Kind regards !
Stefko