- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- i.MX Forums
- :
- i.MX Processors
- :
- Spoofed TCP RST issue on imx6 sabresd with android 4.2.2
Spoofed TCP RST issue on imx6 sabresd with android 4.2.2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Spoofed TCP RST issue on imx6 sabresd with android 4.2.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
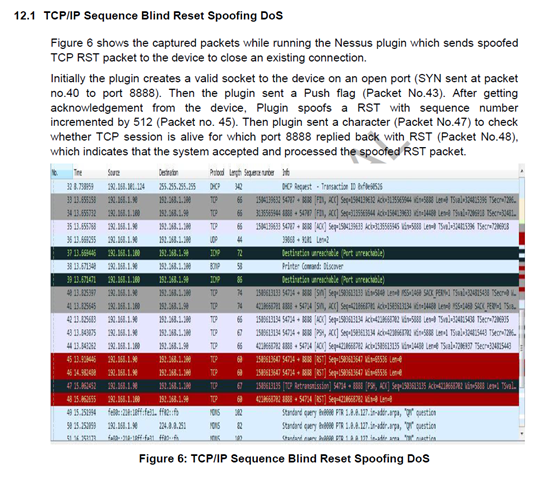
I got a spoofed TCP RST issue on imx6 sabresd with android 4.2.2 and kernel version 3.0.35.
The problem as following, the imx6 sabresd processes spoofed TCP RST packets. This plugin creates a TCP session to an open port on sabresd device. It sends a character to the port, if it get a reply other than RST packets it indicates that the session is alive, and then it spoofs a RST whit the sequence number incremented by 512 from the valid tuple defining the socket(i.e. srchost, dsthost, srcport, dstport). It then sends a character to the socket created to check for a RST from the host. If it gets a RST from sabresd device, then that indicates that the system accepted and processed the spoofed RST. When this scan was launched on Central HMI, from the packet capture is was observed that the spoofed RST packet close the TCP session successfully.
Could anyone tell me how to disable processing TCP packets with spoofed sequence number ??