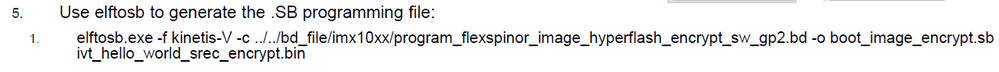- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- i.MX Forums
- :
- i.MX RT
- :
- Re: RT1015 BEE XIP Step Confirm
RT1015 BEE XIP Step Confirm
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RT1015 BEE XIP Step Confirm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I got doc from FAE, but I want to confirm some step.
Please check.
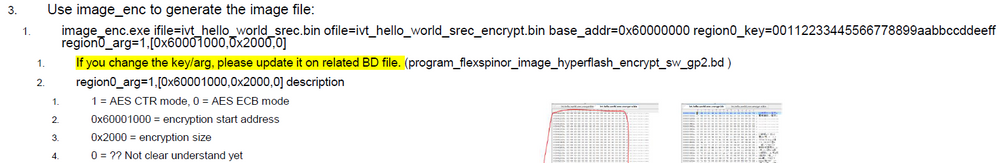
1. For pdf page 3 "Tools", I got image_enc.exe from FAE and rename to ”image_enc.exe".
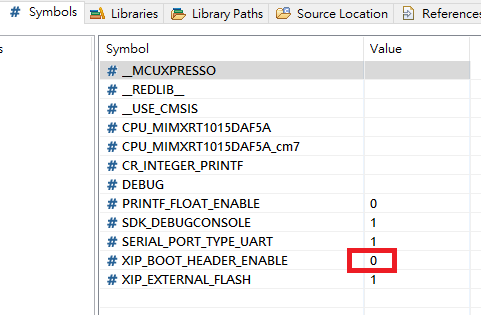
2. In page "Project modification", SDK Example: I use evkmimxrt1015_igpio_led_output SDK and generate evkmimxrt1015_igpio_led_output.s19 file with XIP_BOOT_HEADER_ENABLE=0 and XIP_BOOT_HEADER_DCD_ENABLE=0.
3. I prepare a folder and make all utility file in the same path and create a batch file.
4. In page 7 Generate secure image.
I change to
elftosb.exe -f imx -V -c imx-flexspinor-normal-unsigned.bd -o ivt_igpio_led_output_srec.bin evkmimxrt1015_igpio_led_output.s19
5.
My script is "image_enc.exe ifile=ivt_igpio_led_output_srec.bin ofile=ivt_igpio_led_output_srec_encrypt.bin base_addr=0x60000000 region0_key=00112233445566778899aabbccddeeff region0_arg=1,[0x60001000,0x2000,0]"
6.
I made a tool to remove first 1KB data.
My script is "RemoveBinaryBytes.exe ivt_igpio_led_output_srec_encrypt.bin ivt_igpio_led_output_srec_encrypt_remove1K.bin 1024"
My output is ivt_igpio_led_output_srec_encrypt_remove1K.bin.
7.
My script is "elftosb.exe -f kinetis -V -c program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd -o boot_image_encrypt.sb ivt_igpio_led_output_srec_encrypt_remove1K.bin"
The final sb file is "boot_image_encrypt.sb".
I attach all of my script and bin file.
8.
I think the boot_image.sb is the boot_image_encrypt.sb file.
But in this step, I am confused.
From AN12079, I guess it should modify the ucl2.xml file, but my doc doesn't mentioned about it.
Here is the page 29 of AN12079.
Sorry I change to simplified Chinese here.
疑问一:
我的program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd档案当中
section(0)里面的动作,是不是都要透过blhost去执行,我必须跟AN12079一样,加上blhost receive-sb-file的command
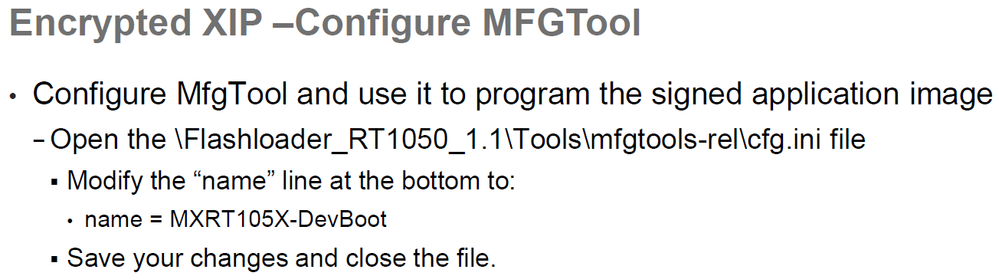
FAE给我的doc中,只提到将Flashloader的ini里面的name改成 name = MXRT105X-DevBoot
我认为这边是有问题的
疑问二:
program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd档案当中
sources {
myBinFile = extern (0);
}
以及
#5. Program image
load myBinFile > kAbsAddr_Ivt;
我看不懂是将哪一个档案load到kAbsAddr_Ivt这一个位置?
Assign to Kerry
To Kerry: 你可以使用英文或中文回覆
附件有我的SDK和我的script以及FAE提供的doc
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry
抱歉
比较晚回覆
这几天再忙别的事情
非常感谢你的资料 我会再确认 有任何更新会再告诉你
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
我这边用命令行的方式已经完全成功了。
我看你的fuse, 你没有烧写BEE_KEY0_SEL,BEE_KEY1_SEL这些。
我这边用了engine0,所以烧写了BEE_KEY0_SE,目前已经完全成功使用命令行了。
当然由于我这边之前用MCUBootutility的时候,已经烧过fuse,所以我就把我bd文件里面关于烧写fuse的部分去掉了,生成的image.sb使用MFGTool烧写没有问题,另外,boot也没问题。
你那边需要注意下,烧写之后,boot,在SW8配置为:1-ON,2-OFF 3-ON 4-OFF
如果那边需要烧写fuse,我也额外生成了烧写fuse的.sb
elftosb.exe -f imx -V -c imx-flexspinor-normal-unsigned.bd -o ivt_evkmimxrt1015_iled_blinky_0x60002000.bin evkmimxrt1015_iled_blinky_0x60002000.s19
image_enc.exe hw_eng=bee ifile=ivt_evkmimxrt1015_iled_blinky_0x60002000.bin ofile=evkmimxrt1015_iled_blinky_0x60002000_bee_encrypted.bin base_addr=0x60000000 region0_key=0123456789abcdeffedcba9876543210 region0_arg=1,[0x60001000,0x2000,0] region0_lock=0 use_zero_key=1 is_boot_image=1
RemoveBinaryBytes.exe evkmimxrt1015_iled_blinky_0x60002000_bee_encrypted.bin evkmimxrt1015_iled_blinky_0x60002000_bee_encrypted_remove1K.bin 1024
elftosb.exe -f kinetis -V -c program_imxrt1015_qspi_encrypt_sw_gp2.bd -o boot_image_encrypt.sb evkmimxrt1015_iled_blinky_0x60002000_bee_encrypted_remove1K.bin
elftosb.exe -f kinetis -V -c burn_fuse.bd -o burn_fuse.sb
pause
然后你可以在ucl2.xml里面添加烧写burn_fuse.sb的内容
<LIST name="MXRT1015-beefuse_DevBoot" desc="Boot Flashloader">
<!-- Stage 1, load and execute Flashloader -->
<CMD state="BootStrap" type="boot" body="BootStrap" file="ivt_flashloader.bin" > Loading Flashloader. </CMD>
<CMD state="BootStrap" type="jump" onError = "ignore"> Jumping to Flashloader. </CMD>
<!-- Stage 2, burn BEE related fuse using Flashloader -->
<CMD state="Blhost" type="blhost" body="get-property 1" > Get Property 1. </CMD> <!--Used to test if flashloader runs successfully-->
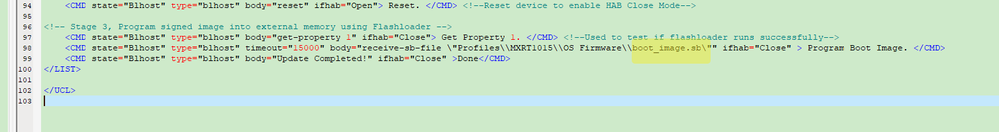
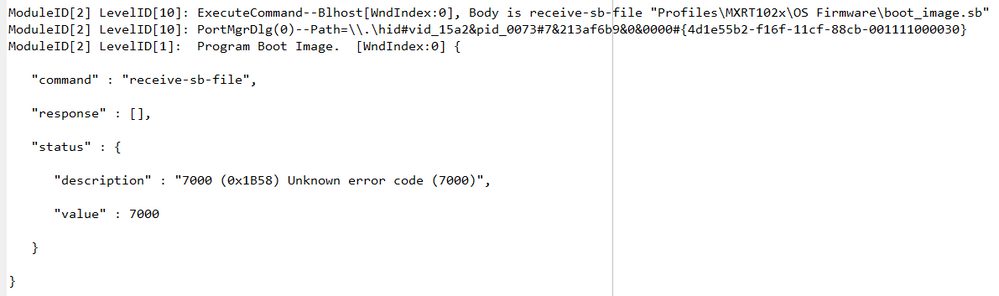
<CMD state="Blhost" type="blhost" body="receive-sb-file \"Profiles\\MXRT1015\\OS Firmware\\burn_fuse.sb\"" > Program Boot Image. </CMD>
<CMD state="Blhost" type="blhost" body="reset" > Reset. </CMD> <!--Reset device-->
<!-- Stage 3, Program boot image into external memory using Flashloader -->
<CMD state="Blhost" type="blhost" body="get-property 1" > Get Property 1. </CMD> <!--Used to test if flashloader runs successfully-->
<CMD state="Blhost" type="blhost" timeout="15000" body="receive-sb-file \"Profiles\\MXRT1015\\OS Firmware\\boot_image.sb\"" > Program Boot Image. </CMD>
<CMD state="Blhost" type="blhost" body="Update Completed!">Done</CMD>
</list>cfg.ini文件里面选择MXRT1015-beefuse_DevBoot
第一次烧写过fuse之后,后续就不需要再烧fuse,然后你可以cfg.ini再用回MXRT1015-DevBoot
我这边上传我的相关文件
你那边有空可以试试,我这边烧写了boot_image_encrypt.sb之后,修改boot模式,可以正常boot, led灯也可以正常闪烁。
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry
我发现我跟你的.s19档案,有相当的差异
我的步骤是
1.
2.
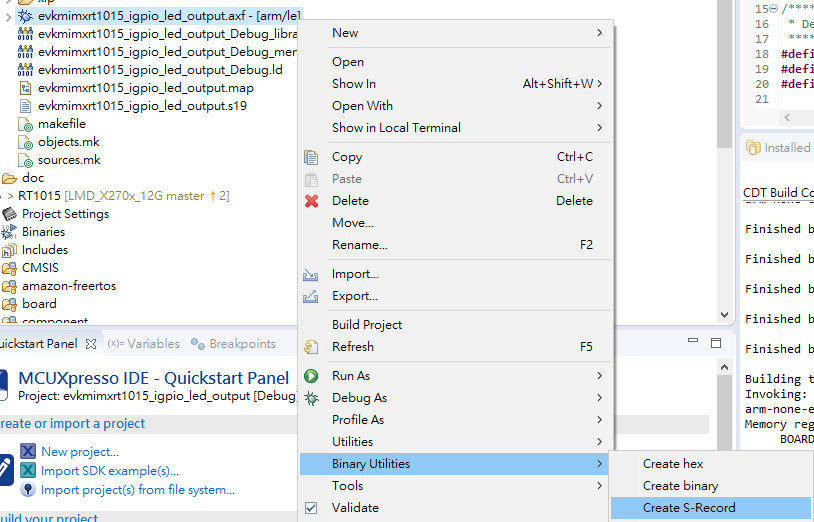
3. AXF --> S-Record
我的步骤正确吗?
还是说要使用Release Build?
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
上午好,非常高兴听到你至少能用我的文件工作了。
我这边使用的是debug模式,不是release模式。
你说有差异,具体差异是什么?
还有,你用我的能工作,是我的image吗?具体用了哪些文件?还是MFGTool直接烧录我的image sb文件的?
楼主你更新是否可以从最后一贴更新,不然我比较难找到你最新的回复,都夹在中间了。
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry
Good news!
我使用你的
烧进去我的EVK
Image跑起来了!
我也会先确认这个部分
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
很抱歉迟回复你了。
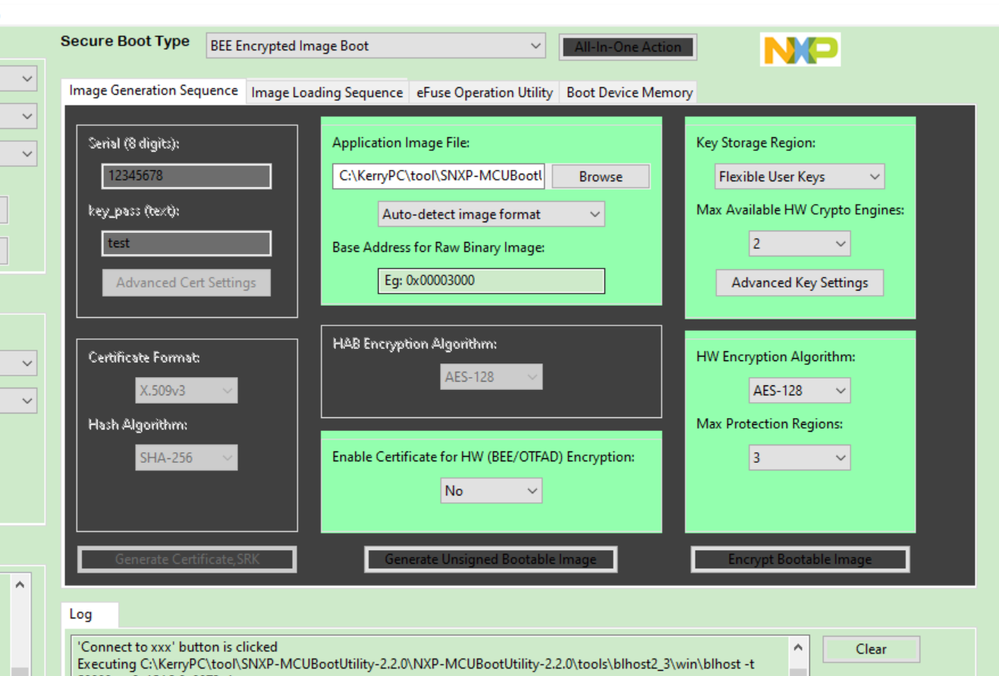
1. 关于我上面MCUBootUtility的配置,对应的image_enc 的命令如下:
C:\KerryPC\tool\SNXP-MCUBootUtility-2.2.0\NXP-MCUBootUtility-2.2.0\tools\image_enc2\win>"C:\KerryPC\tool\SNXP-MCUBootUtility-2.2.0\NXP-MCUBootUtility-2.2.0\tools\image_enc2\win\image_enc.exe" hw_eng=bee ifile="C:\KerryPC\tool\SNXP-MCUBootUtility-2.2.0\NXP-MCUBootUtility-2.2.0\gen\bootable_image\ivt_evkmimxrt1015_iled_blinky_0x60002000_unsigned.bin" ofile="C:\KerryPC\tool\SNXP-MCUBootUtility-2.2.0\NXP-MCUBootUtility-2.2.0\gen\bootable_image\ivt_evkmimxrt1015_iled_blinky_0x60002000_unsigned_bee_encrypted.bin" base_addr=0x60000000 region0_key=0123456789abcdeffedcba9876543210 region0_arg=1,[0x60001000,0x2000,0] region0_lock=0 use_zero_key=1 is_boot_image=1
和你ppt里面有些区别,主要使用的BEE engine key是zero key,你PPT命令不配置,则默认为radom key
2. 关于你那边SB文件最后MFGTool的问题
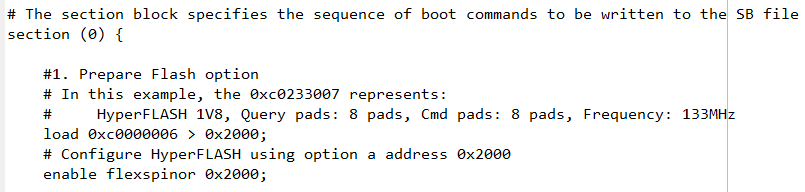
你最大的问题是直接使用了program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd,这个是RT1050结合hyperflash的bd文件,而你如果使用的是MIMXRT1015-EVK 板子,实际上你的板载flash芯片是QSPI 芯片:adesto AT25SFxxxA芯片,你需要使用的bd文件内容如下:
sources {
myBinFile = extern (0);
}
section (0) {
load 0xc0000007 > 0x20202000;
load 0x0 > 0x20202004;
enable flexspinor 0x20202000;
erase 0x60000000..0x60005000;
load 0xf000000f > 0x20203000;
enable flexspinor 0x20203000;
load myBinFile > 0x60000400;
}
如果使用的是单引擎,engine0的话,那么fuse那边只需要烧 BEE_KEY0_SEL
load fuse 0x00003000 > 0x6;
然后烧写SW_GP2还可以维持之前的:
# program SW_GP2
load fuse 0x76543210 > 0x29;
load fuse 0xfedcba98 > 0x2a;
load fuse 0x89abcdef > 0x2b;
load fuse 0x01234567 > 0x2c;
当然,如果已经烧写了fuse,后面再改变firmware的时候,bd文件里面可以去掉烧fuse的内容,直接烧写文件就可以了。
你那边目前的最大问题应该是.bd文件内容不对,是针对Hyper flash的,所以生成的文件是不能够烧录到你的qspi flash的。
我建议你用我这边的bd文件内容再试下。
image_enc2的命令,也用我上面的命令。
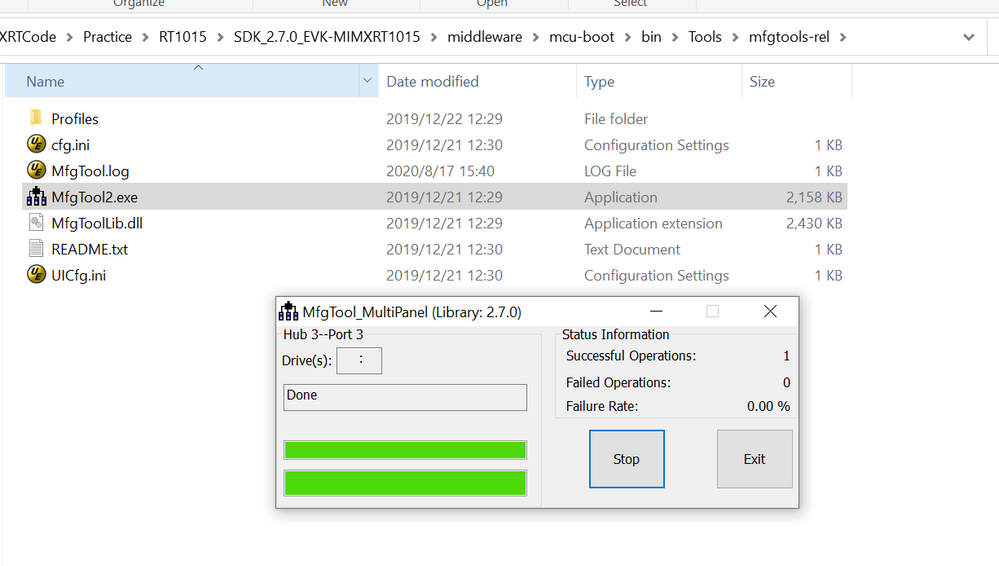
你也可以用我附件里面的sb去烧录看看, 我这边MFGtool烧录结果:
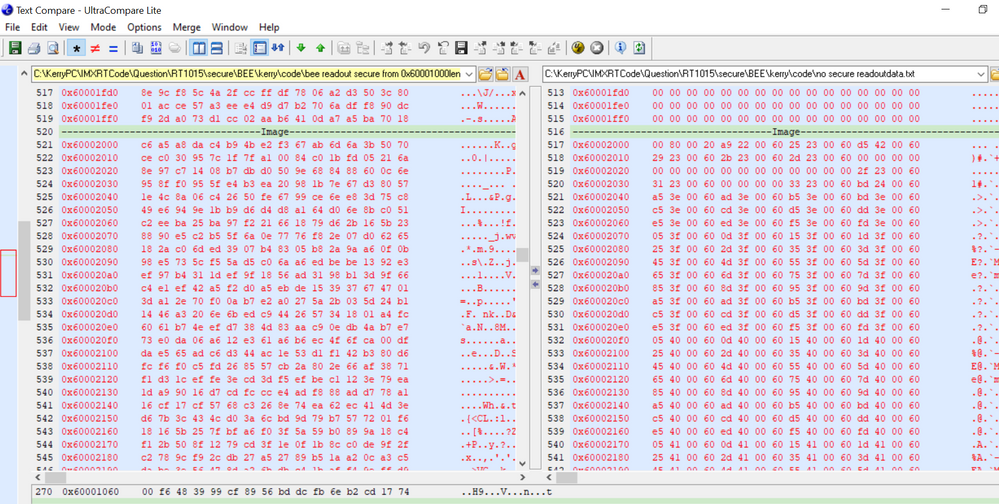
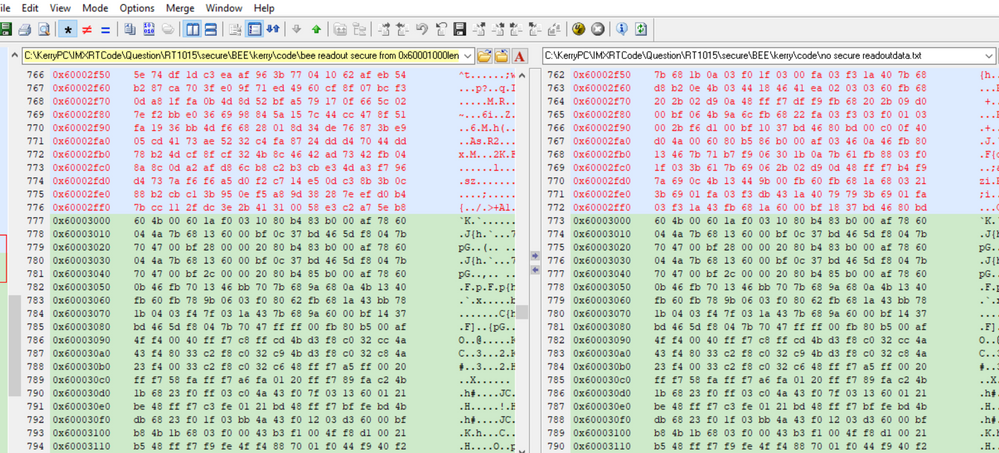
我的文件,加密区域起始地址是:0X60001000,长度是0X2000。
我也给出我的未加密app的原文件,你可以发现,如果烧录了我 的SB文件,再读出image,你会发现,0X60001000-0X60002FFF是密文,0X60003000开始就是明文了。
如果还有任何问题,欢迎和我继续交流。
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry
更新一下
后来我的FAE建议我将load Hyperflash部分改成
load 0xC0000006 > 0x2000
MFGTool就可以将.sb 档案成功烧录
但是image还是无法执行
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken,
我看到你之前上传的文件中,是可以用image_enc.exe, 你在做这个命令生成BEE加密文件的时候是否遇到过问题?
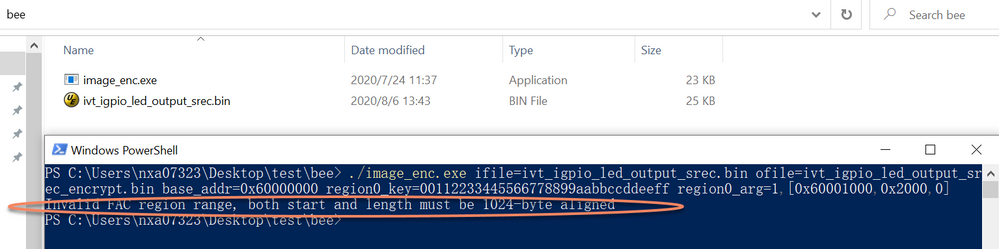
./image_enc.exe ifile=ivt_igpio_led_output_srec.bin ofile=ivt_igpio_led_output_srec_encrypt.bin base_addr=0x60000000 region0_key=00112233445566778899aabbccddeeff region0_arg=1,[0x60001000,0x2000,0]
Invalid FAC region range, both start and length must be 1024-byte aligned
我这边发现总是出现invalid FAC region range的问题。
然后我用你的image_enc.exe, 还有你的源文件ivt_igpio_led_output_srec.bin,还是会出现这个问题:
麻烦你那边看看,你是怎么解决这个问题的?
我现在图片中两个文件都是你的文件。
要么难道是不能用powershell,必须要用和你一样的bat文件吗?
我现在自己这边单独用powershell也是会出现这个问题。
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
这个问题最后确认下来是powershell问题,用cmd就不会出这个问题了。
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
感谢你的信息更新。
那么你有没有用我上面的bd文件内容?
还有,你那边在用image_enc.exe的时候,有没有试下我这边的命令:
./image_enc.exe hw_eng=bee ifile=ivt_evkmimxrt1015_iled_blinky_0x60002000_unsigned.bin ofile=evkmimxrt1015_iled_blinky_0x60002000_bee_encrypted.bin base_addr=0x60000000 region0_key=0123456789abcdeffedcba9876543210 region0_arg=1,[0x60001000,0x2000,0] region0_lock=0 use_zero_key=1 is_boot_image=1
去生成对应的BEE代码,是否能够生成成功?
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
楼主你好!感谢你的新建问题,本来我以为会建case,case不是Public的community,可以一对一的发私有的文件。
下次你也可以建case,这样你那边有些不好放在公共论坛的可以邮件发给我。
建case 流程:
1. Open below SUPPORT site, click blue "Go to Tickets" in the middle.
http://www.nxp.com/support/support:SUPPORTHOME
2.Then you will be requested to Login, if you have no an account, please first Register with your business email.
3.After login, please "Create New Cases" button in the middle, then you can submit your question.
下面我先回复下你的几个疑问:
疑问一:
我的program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd档案当中
section(0)里面的动作,是不是都要透过blhost去执行,我必须跟AN12079一样,加上blhost receive-sb-file的command
FAE给我的doc中,只提到将Flashloader的ini里面的name改成 name = MXRT105X-DevBoot
我认为这边是有问题的
回答:
关于.bd section(0),其实这些你都不需要额外的去关心,因为后续MFGTool会自动根据i生成好的sb文件直接去调用对应的接口,这些最终都会通过blhost去直接操作RT芯片,你不需要额外操作,工具会去做了。
关于你对I think the boot_image.sb is the boot_image_encrypt.sb file.这个问题,其实这个是由MFGtool里面的脚本决定。
你打开:SDK_2.8.0_EVK-MIMXRT1015\middleware\mcu-boot\bin\Tools\mfgtools-rel\Profiles\MXRT1015\OS Firmware\ucl2.xml
其实就是你的文件名要和你.xml里面的.sb名字一样就可以了。
当然你选择的是name="MXRT1015-DevBoot" ,那么你就需要改name="MXRT1015-DevBoot" 下面的.sb名字,或者你直接把你的app sb的名称直接改成boot_image.sb,这样就不需要改这个.xml了。
疑问二:
program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd档案当中
sources {
myBinFile = extern (0);
}
以及
#5. Program image
load myBinFile > kAbsAddr_Ivt;
我看不懂是将哪一个档案load到kAbsAddr_Ivt这一个位置?
回答: 这边的意思,我理解的就是把你带有IVT的,也就是直接从IVT开始数据的.bin放到kAbsAddr_Ivt = 0x60001000;这个地址,在你用这个bd以及ivt_app.bin生成.sb的时候,所以可以理解为myBinFile就是你:
elftosb.exe f kinetis V c ../../bd_file/imx10xx/program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd o boot_image_encrypt.sb
ivt_hello_world_srec_encrypt.bin
这个命令里面的ivt_hello_world_srec_encrypt.bin
希望能帮到你。
如果还有问题,欢迎继续交流!
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry
谢谢
疑问一:
这个部分我了解了,其实MfgTool的ucl2.xml都编好了,只要改name就会对应不同的流程。
name改成MXRT102x-DevBoot后就会对应到有receive-sb-file的command
疑问二:
了解,所以以下面的例子
elftosb.exe f kinetis V c ../../bd_file/imx10xx/program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd o boot_image_encrypt.sb ivt_hello_world_srec_encrypt.bin
"ivt_hello_world_srec_encrypt.bin"这个档案是必须要让mfgtool找的到 对吧?
还是说不需要,上面的command已经把ivt_hello_world_srec_encrypt.bin的内容放进去boot_image_encrypt.sb了
目前我照着所有的程序做,最后的boot_image_encrypt.sb我改成boot_image.sb,放在
Flashloader_RT1020_1.0_GA\Tools\mfgtools-rel\Profiles\MXRT102X\OS Firmware\路径下,覆盖原本的
执行mfgtool后出现了错误,我想我的sb档案是有问题的,还需要再继续厘清
抱歉我没有使用case,我误解你的意思,但我刚刚建立好了一个case,我不知道怎么assign给你
是写在post里面吗?
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
你好!
感谢你的信息更新。
继续讨论你的问题:
1.
疑问二:
了解,所以以下面的例子
elftosb.exe f kinetis V c ../../bd_file/imx10xx/program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd o boot_image_encrypt.sb ivt_hello_world_srec_encrypt.bin
"ivt_hello_world_srec_encrypt.bin"这个档案是必须要让mfgtool找的到 对吧?
还是说不需要,上面的command已经把ivt_hello_world_srec_encrypt.bin的内容放进去boot_image_encrypt.sb了
目前我照着所有的程序做,最后的boot_image_encrypt.sb我改成boot_image.sb,放在
Flashloader_RT1020_1.0_GA\Tools\mfgtools-rel\Profiles\MXRT102X\OS Firmware\路径下,覆盖原本的
执行mfgtool后出现了错误,我想我的sb档案是有问题的,还需要再继续厘清
回复:
ivt_hello_world_srec_encrypt.bin, program_flexspinor_image_hyperflash_encrypt_sw_gp2.bd 你只要放一起,然后使用elftosb命令生成对应的sb文件,该sb文件是包含了下载命令以及你的app代码的最终image,供MFGtool去下载。所以,对于mfgtool,它需要的是sb文件,而不是你的"ivt_hello_world_srec_encrypt.bin"。
看到你那边确实mfgtool下载sb出问题了,说明这个Image还是有问题,确实需要进一步的查看。
我想问下,你那边现在操作的RT芯片是你之前跑过MCUBootUtility tool,烧了HAB close的片子吗?
对了, 你那边后来有没有继续用MCUBootUtility tool工具烧写呢?而是直接想用这个MFGtool去烧,对吗?
我建议你可以进入serial download模式,然后使用MCUBootUtility工具,连接下,看看是否还能连接?如果能连接成功了,你可以把你的fuse map读出来,然后分享出来给我看看。
你那边测试的板子是我们官方的MIMXRT1015-EVK吗?
今天我可能没有时间直接测试了,下周我也找个时间,和你一起测试下这个命令模式。
关于你的新建case,我这边以及看到拿到我这边了,本来我是想你那边的文档如果不方便直接通过论坛给我,可以建case给我,现在我以及拿到你的文档,我们可以通过case,也可以直接论坛交流,当然如果有些信息你那边不太方便论坛写,也可以直接case里给我发邮件。
Wish it helps you!
If you still have questions about it, please kindly let me know.
Best Regards,
Kerry
-------------------------------------------------------------------------------
Note:
- If this post answers your question, please click the "Mark Correct" button. Thank you!
- We are following threads for 7 weeks after the last post, later replies are ignored
Please open a new thread and refer to the closed one, if you have a related question at a later point in time.
-------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kerry
谢谢回覆,我先一样再这边回覆给你,因为我想中文比较方便。
我手边有两片NXP官方的RT1015 EVK,还有我们自己案子用的板子,上面也是RT1015。
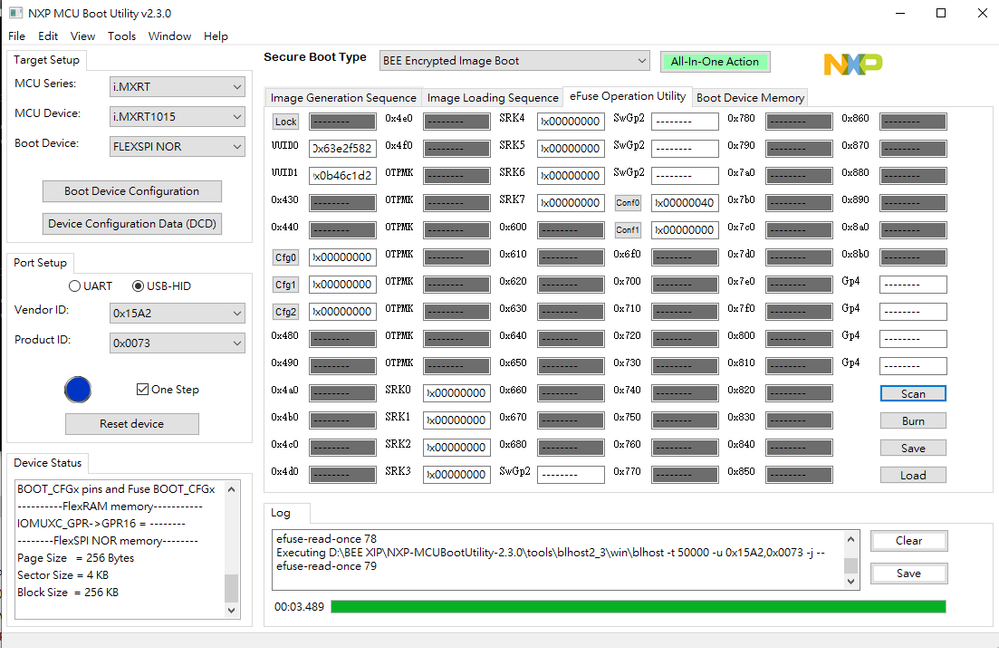
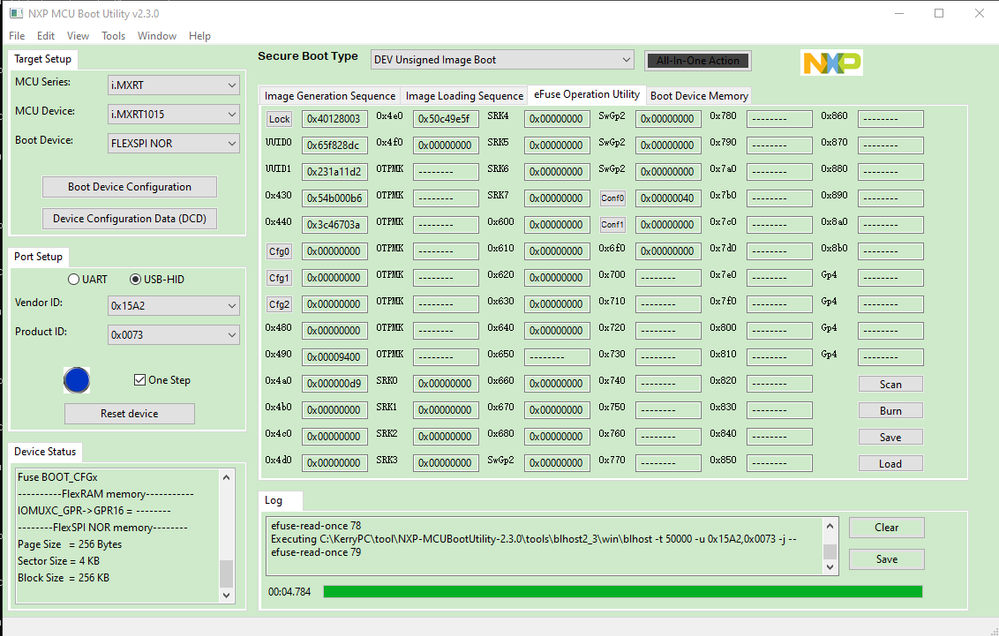
我的HAB应该是open状态,请确认我的efuse
efuse的读取我附上我自己用blhost读跟用MCUBootUtility scan结果。
我目前只使用MFGtool并没有再使用MCUBootUtility
等你有空的时候再帮我确认
Blhost read:
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 0
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 1085440003 (0x40b28003)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 1
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 1675818370 (0x63e2f582)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 2
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 189186514 (0xb46c1d2)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 3
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 1420820724 (0x54b000f4)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 4
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 1011249210 (0x3c46703a)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 5
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 6
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 7
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 8
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 9
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 41984 (0xa400)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 24
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 25
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 26
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 27
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 28
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
E:\WORK\Doc\datasheet\vendor\NXP\i.MaxRT\Application\FlashUpgrade\1015\USB_UART_Download_Script>blhost.exe -t 50000 -u 0x15A2,0x0073 -- efuse-read-once 29
Inject command 'efuse-read-once'
Response status = 0 (0x0) Success.
Response word 1 = 4 (0x4)
Response word 2 = 0 (0x0)
Regards
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ken Su,
非常抱歉这么迟的回复你,最近太多问题要测试。
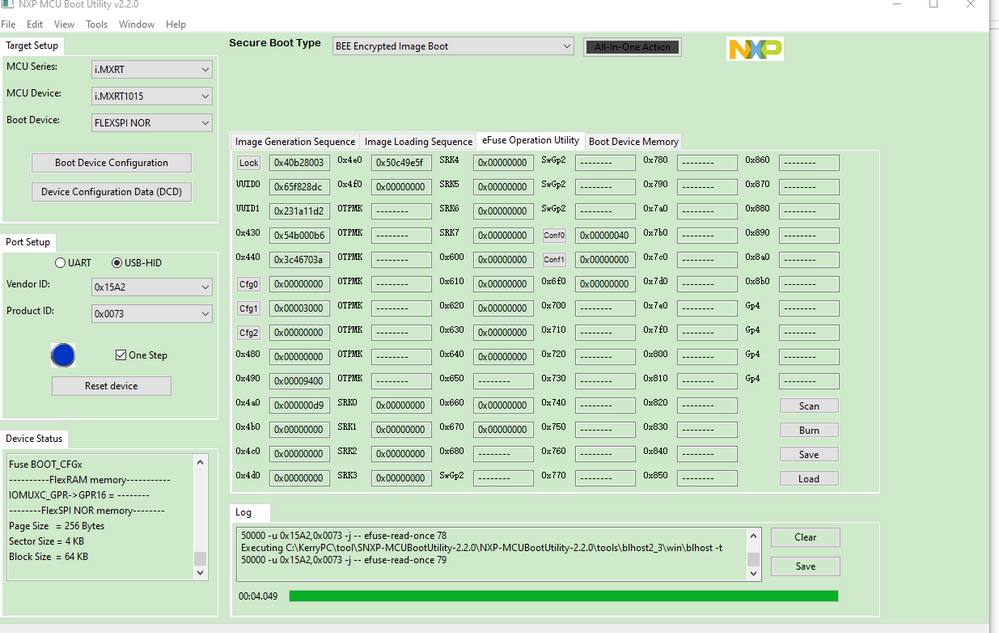
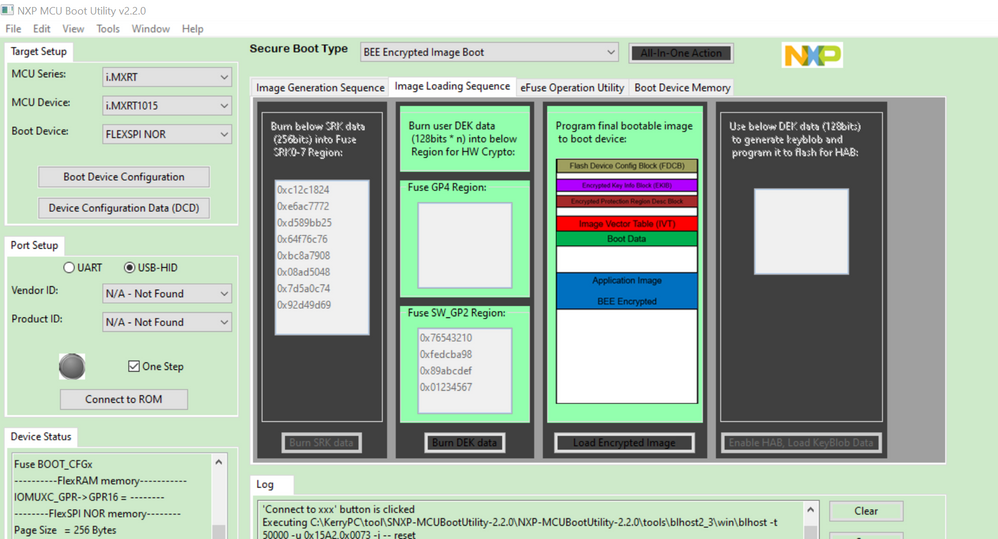
今天我测试了下MIMXRT1015-EVK的情况,不过我还没用命令的模式,我暂时是用MCUBootUtility工具测试,这边BEE不使能HAB加密的方式,我已经测试成功,这是我这边的配置以及测试情况。
fuse map, 初始无加密状态:
fuse map,加密之后的状态:
配置情况:
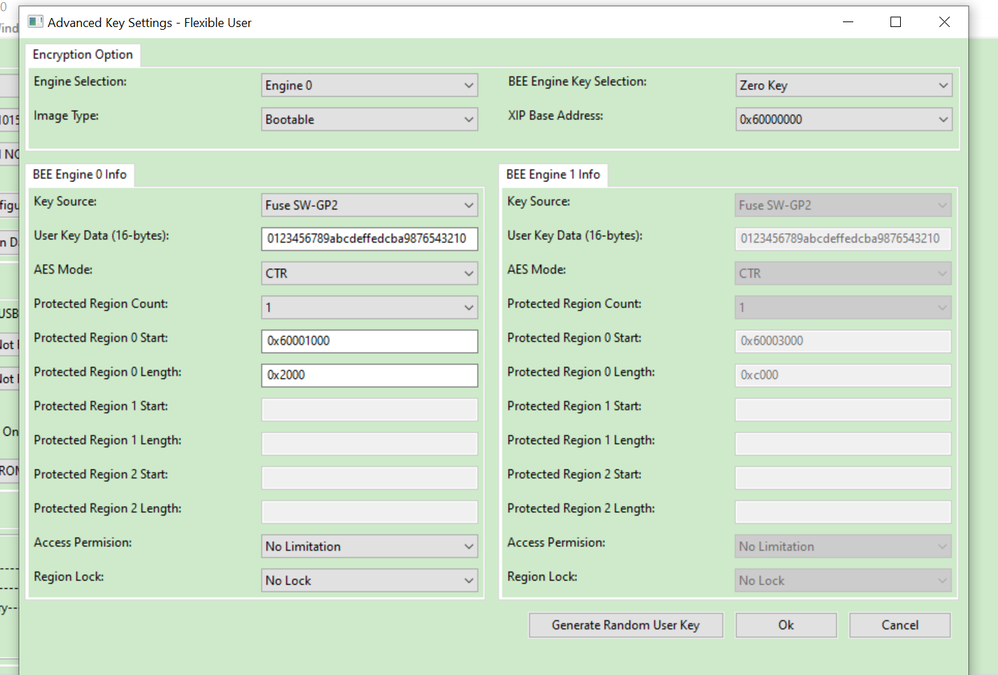
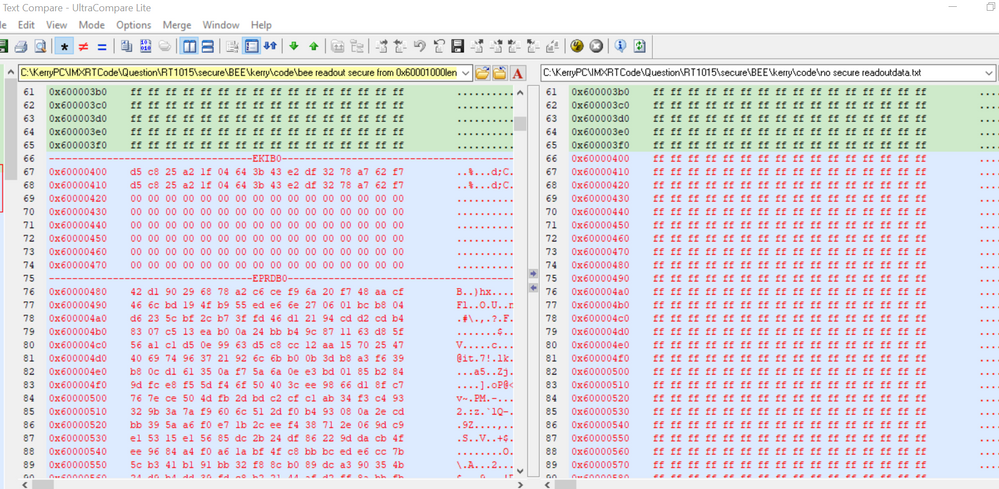
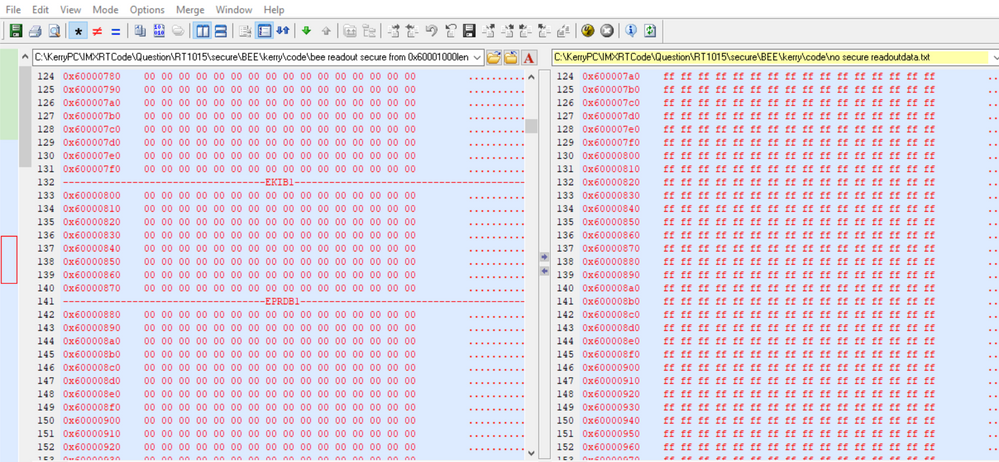
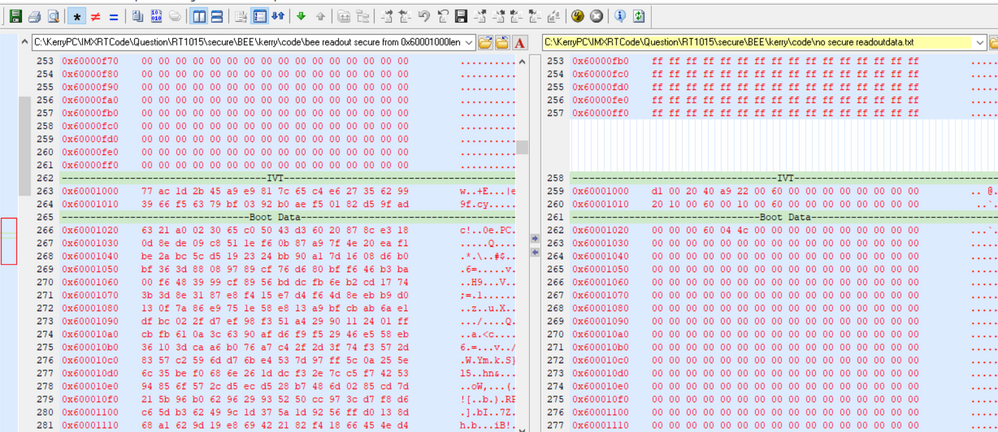
从加密区域可以知道,从0X60001000开始,长度为0X2000,image之后将会无加密,所以我这边分别把同样的代码做加密烧录和无加密烧录,并且把flash空间地址数据读出来对比。
可以看到BEE加密比无加密的代码多了EKIB0, EPRDB0数据,因为我只是使用了region0加密,没有用region1
可以发现,IVT, boot data区域也是加密了,后面0X60001000到0X60002FFFF加密了,再后面数据就一致了。
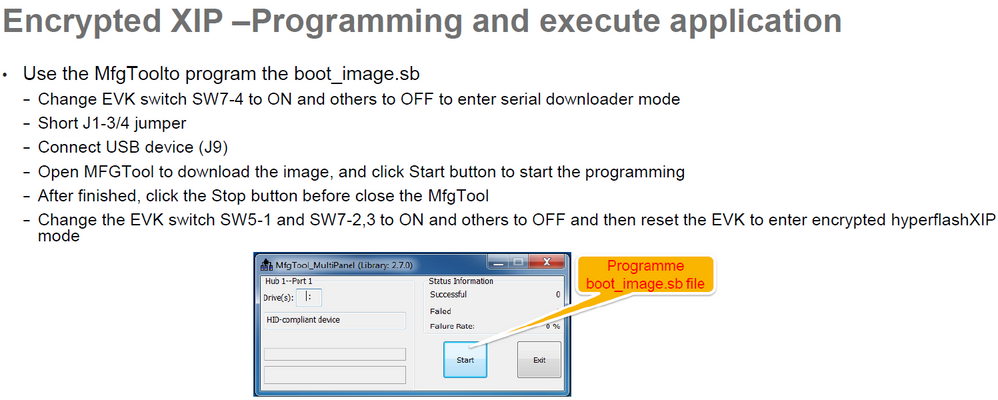
然后退出下载模式,把SW8改为:1-ON,2-OFF, 3-ON,4-OFF.
注意,SW8_1是encrypted XIP,所以做过BEE之后一定要使能:
改过internal boot模式,我烧录的闪灯程序可以成功闪烁小灯。
我这边今天还没来得及做命令行模式,明天我会试试命令行模式,我刚开始没有直接去做命令行,因为我看了你的文档之后,我对i的image_enc的具体命令还不是非常把握,所以我打算用MCUBootUtility方式做成功,然后我再找下该工具的作者,看看我目前配置情况对应的image_enc具体命令情况,然后再尝试会比较保险,这样最后我至少能保证命令行和工具方式都可以使用。
我今天看了下image_enc的命令相关,还在研究:
PS C:\KerryPC\IMXRTCode\Question\RT1015\secure\BEE\kerry\tool> .\image_enc.exe
Usage:
image_enc ifile=<ifile> ofile=<ofile> base_addr=<base_addr> [Options]
Options
hw_eng=otfad/bee/iee
region0_key=<key string> 16 bytes hex string
region0_arg=<0/1>,[start,length,permission]
0 - AES ECB mode, 1 - AES CTR mode
start and length must be 1KB aligned
permision: 0 - No limitation, 1 - Debug disabled
2 - ExecuteOnly, Debug allowed
3 - ExecuteOnly, Debug disabled
Maximum [] pairs is 3
region0_lock=<0/1/2/3> 0 - NoLock, 1 - Lock Region1
2 - Lock Region0 3 - Lock both regions
region1_key=<key string> 16 bytes hex string
region1_arg=<0/1>,[start,length,permission] See region0_arg usage
region1_lock=<0/1/2/3> See region0_lock usage
use_zero_key=<0/1> 0 - Random key, 1 - Zero key, default: 0
is_boot_image=<0/1> 0 - Non-bootable image, 1-bootable image, default:1
kek=<16-byte key string> 16 bytes hex string, default values are 0x00s
otfad_arg=[<16-byte key string>,<8-byte ctr string>,start,length]
Maximum [] pairs is 4
scramble_arg=<4-byte scramble hex string>,<1-byte sramble_align>
otfad_ctx_lock=<0/1>,<0/1>,<0/1>,<0/1>
ikek1=<32-byte key string> IEE Key Blob Encryption Key1, default values are 0x00s
ikek2=<32-byte key string> IEE Key Blob Encryption Key2, default values are 0x00s
iee_arg=[<16/32-byte key string>,<16/32-byte key/ctr string>,<start>,<end>,<aes mode>,<key size>,<lock>]
<16/32-byte key string>: 16-byte - 128-bit-AES-CTR Key, or 256-bit-AES-XTS Key1
32-byte - 256-bit-AES-CTR Key, or 512-bit-AES-XTS Key1
<16/32-byte key/ctr string>: 16-byte - 128-bit-AES-CTR Counter, or 256-bit-AES-XTS Key2
32-byte - 256-bit-AES-XTS Key2(AES-CTR Counter always is 16-byte)
<start>,<end>: 32-bit start address and end address(not included) for IEE Encryption region
<aes mode>: 1 - AES-CTR mode, 2 - AES-XTS mode
<key size>: 128 or 256 for AES-CTR mode, 256 or 512 for AES-XTS mode
<lock>: 0 - Lock, 1 - Lock
-------------------------------------------------------------------
Example:
image_enc ifile=plain_img.bin ofile=enc_img.bin base_addr=0x60000000
region0_key=00112233445566778899aabbccddeeff
region0_arg=1,[0x60001000,0x5000,0]
image_enc ifile=plain_img.bin ofile=enc_img_otfad.bin base_addr=0x60000000
kek=00112233445566778899aabbccddeeff otfad_arg=[00112233445566778899aabbccddeeff,0020406001030507,0x60000000,0x10000]
image_enc ifile = plain_img.bin ofile = enc_img_iee.bin base_addr = 0x30000000
ikbek1 = 000102030405060708090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f
ikbek2 = 202122232425262728292a2b2c2d2e2f303132333435363738393a3b3c3d3e3f
iee_arg = [00112233445566778899aabbccddeeffffeeddccbbaa99887766554433221100,
0123456789abcdeffedcba9876543210efcdab89674523011032547698badcfe,
0x30001000, 0x40000000, 2, 512, 1]
后面我这边有更新,还会第一时间告诉你。
另外,查看过你的fuse map,你没有使用HAB,所以我认为你还是可以使用,不过你已经烧过fuse了,所以你后面做sb的时候,可以把相关的bd文件里面的烧fuse的代码给去掉,直接生成BEE的代码并且烧录即可。
等我命令行调通,我会给出具体详细步骤。
也感谢你的耐心等待与包容。因为BEE加密的测试,也意味着我要烧掉一块板子的fuse,所以我这边也会比较谨慎操作。
Best Regards,
Kerry