- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- Product Forums
- :
- Wireless Connectivity Knowledge Base
- :
- [802.11] Wi-Fi Security Concepts
[802.11] Wi-Fi Security Concepts
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
[802.11] Wi-Fi Security Concepts
[802.11] Wi-Fi Security Concepts
802.11 Security
This post covers the following topics:
- 802.11 authentication processes
- Open System Authentication
- Shared Key Authentication
- Encryption methods
- Wired Equivalent Privacy (WEP)
- Temporal Key Integrity Protocol (TKIP)
- Cipher Block Chaining Message Authentication Code (CBC-MAC) Protocol or CCM mode protocol (CCMP)
- WPA/WPA2/WPA3
- Robust Security Network (RSN)
- 802.1X authorization framework
- Extensible Authentication Protocol (EAP)
- 4-way handshake process
Authentication
Authentication is the second step required for connecting to the 802.11 Basic Service Set (BSS). Authentication and association must occur between Access Point (AP) and client.
The 802.11 authentication establishes an initial connection between the client and the access point, basically validating or authenticating that the station (STA) is a valid 802.11 device for AP.
The 802.11 standard specifies two methods for the authentication: Open System authentication and Shared Key authentication.
Open System authentication: In this type of authentication, client and AP exchange authentication frames, total two frames exchange in this process. It occurs after a client STA detects an Access Point (AP) by either passive or active scanning.
The client node that wants to join the network initiates the authentication process by sending first message. The first message contains the sending node’s 802.11 capabilities. In the response, authentication result is received. If the authentication is successful, then the client and AP will be declared mutually authenticated.
The client cannot make the association request if it is not authenticated. Once the Open System authentication and association is successful, the client becomes a member of the BSS.
Figure 1. Open System authentication
Wired Equivalent Privacy (WEP) encryption is optional with Open System authentication. For data privacy, WEP encryption can be used with Open System Authentication. In other words, WEP is not used as part of the Open System authentication process, but WEP encryption can be used to provide data security after a successful authentication and association.
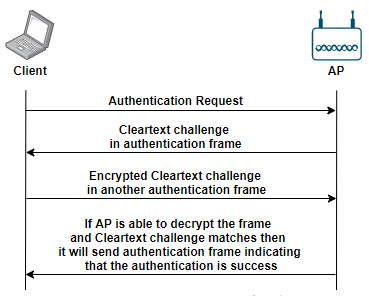
Shared Key Authentication: Shared Key authentication utilizes four authentication messages exchange between client and AP. Shared Key authentication uses WEP encryption to authenticate the client. The four authentication messages are described below.
- The client sends the authentication request to the AP.
- The AP sends a clear-text challenge to the client station using an authentication response frame.
- The client station then encrypts the clear-text challenge and sends it back to the AP by using the frame body of the authentication frame.
- The AP decrypts the station’s response and compares it to the challenge text. If it matches, the AP will send the final authentication frame to the client and confirms the successful authentication.
Once the Shared Key authentication is successful, the same static process will be used to encrypt the 802.11 data frames.
This Shared Key authentication has security risks. If someone captures the clear-text challenge phrase and then captures the encrypted challenge phrase in the response frame, then could potentially derive the static WEP key. If the static WEP key is compromised, now all the data frames can be decrypted.
Figure 2. Shared Key Authentication
WLAN Encryption Methods
The 802.11 standards define three encryption methods. These methods are used to encrypt the MAC Service Data Unit (MSDU) payload of the data frame. 802.11i specification divides security algorithm in two types that are Robust Security Network Association (RSNA) and Pre-RSNA.
- RSNA: This type of security algorithm consists of two protocols for the data confidentiality, as mentioned below.
- Temporal Key Integrity Protocol (TKIP)
- Counter Mode with Cipher Block Chaining Message Authentication Code (CBC-MAC) Protocol or CCM mode Protocol (CCMP)
Both of these protocols are discussed in detail in later section of this post.
- Pre-RSNA: This type of security consists of authentication methods as mentioned below.
- Wired Equivalent Privacy (WEP)
- 802.11 entity authentication
WEP: Wired Equivalent Privacy protocol works on second layer of the OSI model. It utilizes RC4 algorithm for the encryption.
Originally in 802.11 standard, 64-bit WEP and 128-bit WEP were defined as supported encryption methods.
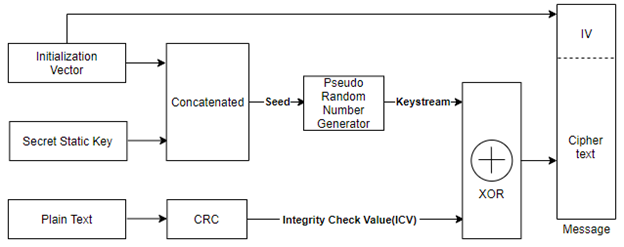
Figure 3. WEP Encryption Process
WEP encryption process is explained below.
- WEP Concatenates Initialization Vector (IV) and Secret Static key, the combination of the same is used as seed to Pseudo random number generator, as a result of this the keystream is generated.
- WEP runs Cyclic Redundancy Check (CRC) on plain-text that generates Integrity Check Value (ICV).
- Cipher text is generated after applying RC4 c to the generated Key stream and ICV. The final encrypted message is made by attaching the IV in front of the Cipher text.
TKIP: As the security failures found in WEP, enhancement of WEP is introduced and that is known as TKIP. As per the 802.11i specification, TKIP uses 128 bits long key for encryption. TKIP is a combination of various algorithms wrapping WEP to offer the best security that can be obtained for the WEP-based devices. Below algorithms are added to WEP:
- New Initialization Vector sequencing to protect against replay attacks.
- A cryptographic 64-bit Message Integrity Check (MIC also called Michael) for the integrity of data.
- Per-packet key mixing (secret key and IV) function to de-correlate IVs from weak keys.
- Rekeying mechanism to provide fresh encryption.
In WEP, Secret Static key has to be set manually so refreshing/rekeying is not the scope there, but in TKIP key rekeying mechanism is there, and that is why it can dynamically modify the keys within wireless LANs.
This dynamic key is Pairwise Transient Key (PTK) for unicast traffic and Group Temporal Key (GTK) for multicast/broadcast traffic generated through 4-way handshake. Refer section 4-way handshake for more details.
CCMP: Counter mode with Cipher-Block Chaining Message Authentication Code protocol (CCMP) is mandatory for RSN compliance.
The AES Counter with CBC-MAC (CCM) process uses the same key for encrypting the MSDU payload and provides for a cryptographic integrity check. WEP and TKIP use RC4 and CCM uses the AES block cipher. Although AES is capable of using different key sizes, but when it is implemented as part of the CCMP encryption method,
CCM combines the Counter mode (CTR) and Cipher-Block Chaining Message Authentication Code (CBC-MAC) for data confidentiality and for authentication and integrity respectively.
New temporal key for every session, and a unique nonce value for each frame protected by a given temporal key is required by CCM, it also uses a 48-bit packet number (PN) for this purpose. Reusing the PN with the same temporal key nullifies all security guarantees.
WPA/WPA2/WPA3: Wi-Fi Protected Access (WPA) is the evaluation of WEP. Wi-Fi Protected Access 2 (WPA2) is improvisation for WPA, and same way WPA3 is improvised version of WPA2. WPA is introduced by Wi-Fi alliance in order to achieve better security in network.
WPA: When WEP was used, it was relatively easy to break the security, so the Wi-Fi Alliance developed WPA to give network connections an additional layer of security.
The WPA certification only required support for TKIP/RC4 dynamic encryption key generation, but the numbers of attacks were done on TKIP. The Beck-Tews attack can recover the MIC and the plain text from an encrypted packet; it can also inject forged frames. These attacks are not used to recover the encryption key but instead are used to recover the MIC checksum that is used for packet integrity.
These exploits can usually be prevented by changing TKIP settings as keying intervals on a WLAN controller or AP, or the better solution is to stop using TKIP and upgrade to CCMP with AES.
WPA2: The Wi-Fi Alliance revised the previous WPA specification to WPA2, to ensure better security incorporated the CCMP/AES cipher. So, the only practical difference between WPA and WPA2 has to do with the encryption cipher.
WPA and WPA2 both use the Pre-Shared Key (PSK) authentication method; however, WPA specifies TKIP/RC4 encryption, and WPA2 specifies CCMP/AES. WPA2 integrates the AES algorithm in CCMP, providing more reliable security compared to previous encryption methods.
WPA2 is backward compatible with WPA and it supports 802.1X/EAP authentication or pre-shared keys. WPA and WPA2 have two options for authentication, the personal mode and the enterprise mode.
- Personal Mode: The personal mode is based on key-sharing to avoid installing an authentication server, so it’s used for Small Office Home Office (SOHO) cases.
- Enterprise Mode: The enterprise mode is based on using an authentication server (802.1X/EAP frameworks) such as RADIUS in order to offer access control.
Note: WPA is vulnerable to attacks in both, personal and enterprise modes.
WPA3: WPA3 is the latest generation of Wi-Fi security and provides cutting-edge protocols for security. It has been built on the bases of the WPA2, to simplify security in Wi-Fi.
Previous versions of WPA uses PSK authentication method but WPA3 uses Simultaneous Authentication of Equals (SAE). Because of SAE WPA3-Personal networks that are configured with weak/simple passphrase are not that easy to crack using attack like brute-force.
In case someone determines/guess the passphrase, it is not possible to examine the exchange and get the session keys; so even if passphrase is guessed, snoop on someone’s WAP3-Personal traffic is not possible.
WPA3 is backward compatible with WPA2 devices, it is a mandatory for Wi-Fi CERTIFIED devices. There are two versions of WPA3:
- WPA3-Personal
- WPA3-Enterprise
WPA3-Personal: This version provides password-based authentication, even when users choose short or weak passwords good security is maintained. It doesn’t require an authentication server and is the basic protocol for home users and small businesses use.
- Uses 128-bit encryption.
- Makes use of a Simultaneous Authentication of Equals (SAE) handshake that protects against brute force attacks.
- Incorporates Forward Secrecy means that a new set of encryption keys are generated every time a WPA3 connection is made, so if the initial password is compromised, security won’t be compromised.
WPA3-Enterprise: WPA3 Personal and WPA3-Enetrprise don’t have much difference but the Enterprise version is more secure compared to Personal version. As the enterprise version is focused on large enterprises and protect more sensitive data compare to SOHO cases.
- 192-bit security mode, this optional mode specifies configuration for cryptographic component to maintain overall network security.
- WPA3 Personal is not the most secure option but it is easier to deploy and use than the WPA3 Enterprise.
Robust Security Network (RSN)
Robust security network association requires two 802.11 stations to establish procedures to authenticate and associate with each other and create dynamic encryption keys through the 4-Way Handshake process.
Any two stations must share dynamic encryption keys that are unique between those two stations. CCMP/AES encryption is the mandatory encryption method, and TKIP/RC4 is an optional encryption method.
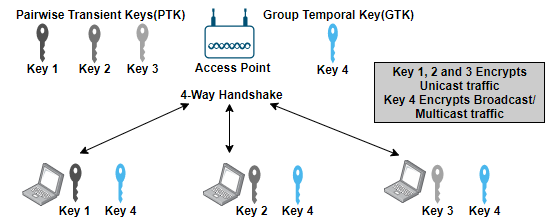
When RSN security associations are used within a BSS, there are two keys that both the devices install.
- Each client has unique encryption key that is shared with the access point. That key is Pairwise Transient Key (PTK) used to encrypt unicast traffic.
- There is a Group Temporal Key (GTK) shared between all the associated devices with the AP. It is used to encrypt multicast and broadcast traffic.
All the client stations have undergone a unique RSNA process called the 4-Way Handshake, this process will be discussed in detail later in this post. Refer Figure 4 below for the better understanding of key sharing between the AP and clients.
Figure 4. RSN security in BSS
RSN security in IBSS
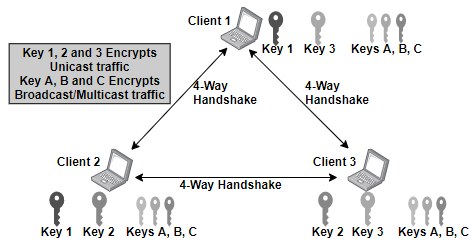
The 802.11 standard also defines a WLAN topology known as an Independent Basic Service Set (IBSS). In this topology multiple client stations in one physical area communicating in an ad-hoc pattern.
All the stations within the IBSS goes through the 4-Way Handshaking process with each other, because of peer to peer communication within the IBSS.
Each station has the unique dynamic TKIP/RC4 or a CCMP/AES PTK; when the station connects to another station within the IBSS the same key is shared between them. Each stations defines its own GTK, the same is used for broadcast/multicast transmissions within the IBSS. Each station will use the 4-Way Handshake process or the Group Key Handshake to generate GTK and distribute it to the peer stations.
To seed the 4-way handshake, PSK authentication is used within the IBSS. So, whenever a client joins the IBSS, (for both the traffic types, unicast and multicast/broadcast). Refer to Figure 5 below that represents RSN in an IBSS.
Figure 5. RSN security in IBSS
RSNIE: Robust Security Network Information Element (RSNIE) is a field present in 802.11 management frame, this field is used to identify RSN security.
An information element is an optional field of variable length that can be found in like beacon management frames, probe response frames, association request frames, and re-association request frames. For details on different frames refer the [802.11] Wi-Fi Basic concepts.
The RSN information element indicates if the authentication used is 802.1X/EAP or pre-shared key (PSK).
802.1X authorization framework
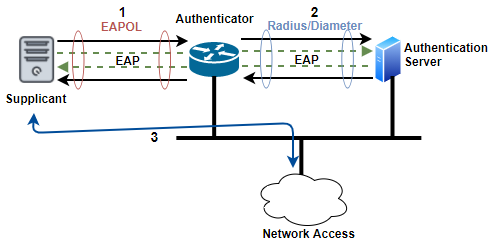
The 802.1X is a port based access control standard which provides an authorization framework. The Authorization Framework involves three components to ensure only valid users and devices can access the network: Supplicant, Authenticator, and Authentication Server. In 802.1X framework, Extensible Authentication Protocol (EAP) is used to validate users at layer 2 (of OSI model).
Supplicant: A host with software requests authentication and access to network. Authentication server verifies authentication credentials that are unique for each supplicant.
Laptop or wireless handheld device trying to access the network is used as supplicant in WLAN.
Supplicant can communicate with authentication server using EAP protocol. The supplicant is not allowed to communicate with the upper layers (layer 3 to 7 of OSI model) until authentication server (at layer 2) validates supplicant’s identity.
Authenticator: Traffic is allowed or blocked to pass through Authenticator’s port. Authenticator allows Authentication traffic to pass through it, while all other traffic is allowed after supplicant’s identity is verified.
The authenticator maintains two virtual ports.
- Uncontrolled port: Used for EAP traffic.
- Controlled port: Used for all other traffic.
Initially, only port that is open and passing traffic is the uncontrolled port. A successful 802.1X authentication opens controller port so that other traffic can traverse the network. Usually, AP or a WLAN controller is used as the authenticator in WLAN.
The authenticator plays intermediator role by passing messages between supplicant and the authentication server.
Authentication server provides guest list services to authenticator. When AP or WLAN controller is configured as authenticator, one should consider authenticator as authentication server.
Authentication Server: Credentials of the supplicant (requesting access and notifies the authenticator) is validated by Authentication server.
User database is maintained by authentication server, or external user database(s)can be requested to authenticate user credentials. EAP authentication protocol is used to communicate between the authentication server and the supplicant.
The 802.1X standard defines the authentication server as a RADIUS server, when configuring a RADIUS server, you need to be able to point the authentication server back in the direction of the authenticator.
Figure 6. Components of 802.1X
EAP
Extensible Authentication Protocol(EAP) is a layer 2 (of OSI model) protocol. Some EAP are proprietary and others are standards. EAP-MD5 provides only one-way authentication, while EAP TLS, EAP-LEAP provide two-way authentication (also called mutual authentication).
Mutual authentication requires that the client credentials are validated by authentication server and that the validity of the authentication server is authenticated by supplicant.
EAP protocol is used within an 802.1X framework. The EAP messages are encapsulated in EAP over LAN (EAPOL) frames. EAPOL is used between the supplicant and the authenticator, but the EAPOL encapsulation is translated to EAP in RADIUS between the authenticator and the authentication server, as described in Figure 6.
EAPOL messages are described below.
Table 1. EAPOL Message Description
|
Packet type |
Name |
Description |
|
0000 0000 |
EAP-Packet |
This is an encapsulated EAP frame. The majority of EAP frames are EAP-Packet frames. |
|
0000 0001 |
EAPOL-Start |
This is an optional frame that the supplicant can use to start the EAP process. |
|
0000 0010 |
EAPOL-Logoff |
This frame terminates an EAP session and shuts down the virtual ports. Hackers sometimes use this frame for denial-of-service (DoS) attacks. |
|
0000 0011 |
EAPOL-Key |
This frame is used to exchange dynamic keying information. For example, it is used during the 4-Way Handshake. |
|
0000 0100 |
EAPOL- Encapsulated - ASF- Alert |
This frame is used to send alerts, such as Simple Network Management Protocol (SNMP) traps to the virtual ports. |
Supplicant and the authentication server use the EAP protocol to communicate with each other at layer 2.
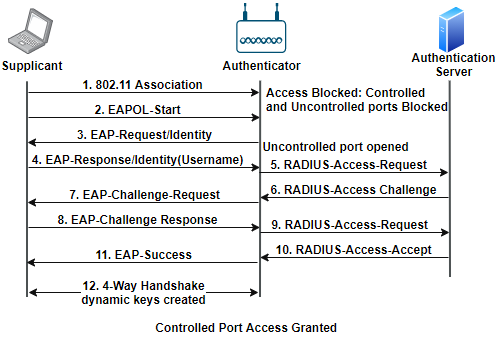
An is between the Supplicant and Authentication server devices. When the controlled port is open, upper layers 3–7 of the OSI model can pass the traffic through it. Once the controlled port is open DHCP is used for Dynamic IP addressing. Figure 7 shows generic EAP message exchange process.
Figure 7. Generic EAP messages exchange flow
4-Way Handshake
The 4-Way Handshake exchange four EAPOL-Key frame messages between authenticator and supplicant, that is used to generate Pairwise Transient Keys (PTK) for encryption of unicast transmissions and a Group Temporal Key (GTK) for encryption of broadcast/multicast transmissions.
Terminologies used in 4-way handshake are listed below.
- AP/Authenticator Nonce (Anonce): Random number generated by authenticator.
- Station/Supplicant Nonce (SNonce): Random number generated by supplicant.
- Master Session Key (MSK): First key that is generated during the 802.1X/EAP authentication or derived from PSK authentication.
This key information is sent via a secure channel from Authenticating Server to Authenticator.
- Pairwise Master Key (PMK): This key is generated based on MSK (PMK is first 256bits (0-255) of MSK) and will be used as one of the input to generate the PTK.PSK (Pre-Shared Key) will be the PMK for the WPA2/PSK security.
- Group Master Key(GMK): This key is also generated from the MSK and is used to generate the GTK.
Authenticator device creates this key and refreshes it at the configured time interval to reduce the risk of GMK being compromised.
- Pairwise Transient Key(PTK): This key is used to encrypt unicast traffic between the AP and a client station.
This key is unique between a client and AP. It is generated using below equation.
PTK = PRF (PMK + ANonce + SNonce + MAC Address of Authenticator + MAC Address of Supplicant)
Here, PRF is a pseudo-random function that applies to all the input.
- Group Temporal Key(GTK): As PTK is used to encrypt unicast traffic, GTK is the key used to encrypt multicast and broadcast traffic between clients and AP.
For each access point different GTK will be there, and with be shared with devices connected to AP.
This key is derived on Authenticator and shared with supplicant during 4-way handshake (Message 3).
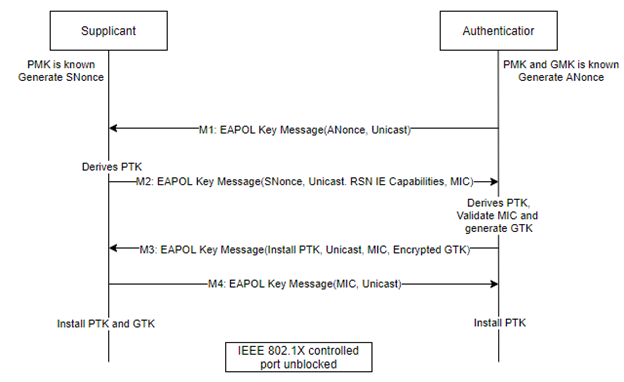
Figure 8 below shows message exchange in 4-way handshake.
Figure 8. 4-Way Handshake message exchange
In the case of PSK, 4-Way handshake starts just after Open System Authentication and if it is 802.1X/EAP, 4-way handshake starts once EAP authentication is completed.
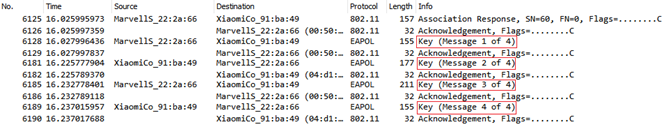
Figure 9 shows the sniffer log of the 4-Way Handshake process, here Marvell device is authenticator, and Xiaomi device is supplicant. Each message exchanged in this process is described below in detail.
Figure 9. Key Exchange Procedures in 4-Way Handshake
Message 1: This message is sent from authenticator to supplicant. It carries ANonce. Once supplicant receives this message it can generate the PTK.
Message 2: This message is sent from supplicant to authenticator. As the supplicant generated the PTK, now it will send SNonce to AP(authenticator), so this second message carries SNonce, RSN information element capabilities and Message Integrity Check (MIC) is set. The MIC is used to check that the received message is not corrupted.
Once authenticator receives this message it will generate the PTK, validate MIC and generate GTK.
Message 3: This message is sent from authenticator to supplicant. It carries ANonce, Authenticator’s RSN information element capabilities and MIC is set. GTK is also delivered and it is encrypted using PTK. This message is for supplicant to install temporal keys.
Message 4: This message is sent from supplicant to authenticator. Final EAPOL-Key frame is sent to authenticator to confirm that temporal keys have been installed.
Once this process gets completed all the messages after that will be encrypted using PTK or GTK (based on unicast or broadcast message).