- NXP Forums
- Product Forums
- General Purpose MicrocontrollersGeneral Purpose Microcontrollers
- i.MX Forumsi.MX Forums
- QorIQ Processing PlatformsQorIQ Processing Platforms
- Identification and SecurityIdentification and Security
- Power ManagementPower Management
- MCX Microcontrollers
- S32G
- S32K
- S32V
- MPC5xxx
- Other NXP Products
- Wireless Connectivity
- S12 / MagniV Microcontrollers
- Powertrain and Electrification Analog Drivers
- Sensors
- Vybrid Processors
- Digital Signal Controllers
- 8-bit Microcontrollers
- ColdFire/68K Microcontrollers and Processors
- PowerQUICC Processors
- OSBDM and TBDML
-
- Solution Forums
- Software Forums
- MCUXpresso Software and ToolsMCUXpresso Software and Tools
- CodeWarriorCodeWarrior
- MQX Software SolutionsMQX Software Solutions
- Model-Based Design Toolbox (MBDT)Model-Based Design Toolbox (MBDT)
- FreeMASTER
- eIQ Machine Learning Software
- Embedded Software and Tools Clinic
- S32 SDK
- S32 Design Studio
- Vigiles
- GUI Guider
- Zephyr Project
- Voice Technology
- Application Software Packs
- Secure Provisioning SDK (SPSDK)
- Processor Expert Software
-
- Topics
- Mobile Robotics - Drones and RoversMobile Robotics - Drones and Rovers
- NXP Training ContentNXP Training Content
- University ProgramsUniversity Programs
- Rapid IoT
- NXP Designs
- SafeAssure-Community
- OSS Security & Maintenance
- Using Our Community
-
-
- Home
- :
- Product Forums
- :
- Other NXP Products Knowledge Base
- :
- Implementation Attacks - Live Demos
Implementation Attacks - Live Demos
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Implementation Attacks - Live Demos
Implementation Attacks - Live Demos
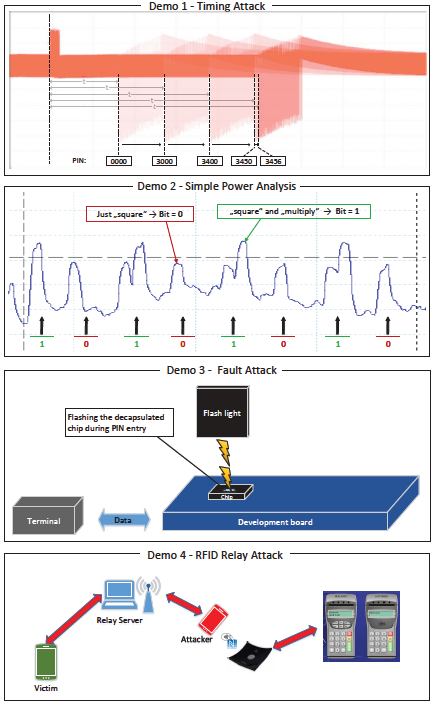
Four live demonstrations are presented: Timing Attack; Simple Power Analysis; Fault Attack, and finally an RFID Relay Attack demo.
- Timing Attack demo
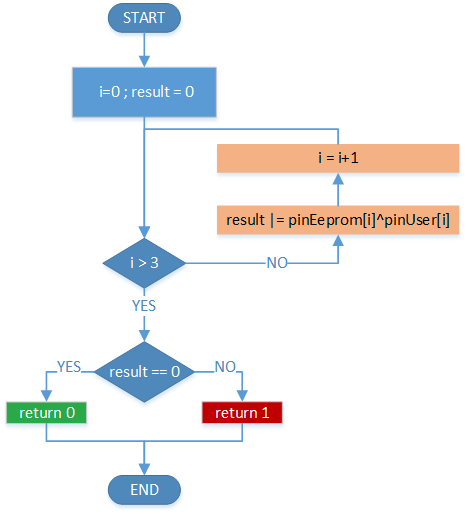
The Timing Attack demo shows the importance of securely implementing a PIN
verification. If a PIN verification is implemented with operations which are
not time-invariant - for example an if-else construction - it is possible to identify
when an incorrect PIN digit is being compared by observing the timing information
of the corresponding EM side-channel measurement. By iterating through all possible
values of a PIN digit the correct character will be identified in a maximum of 10 attempts.
To make the PIN query secure, a time-invariant comparison has to be implemented.
For example, a bitwise XOR comparison and subsequent OR operation for all PIN digits,
ensures the same time is taken for all possible comparisons. This scheme is illustrated in
the block diagram.
- Simple Power Analysis demo
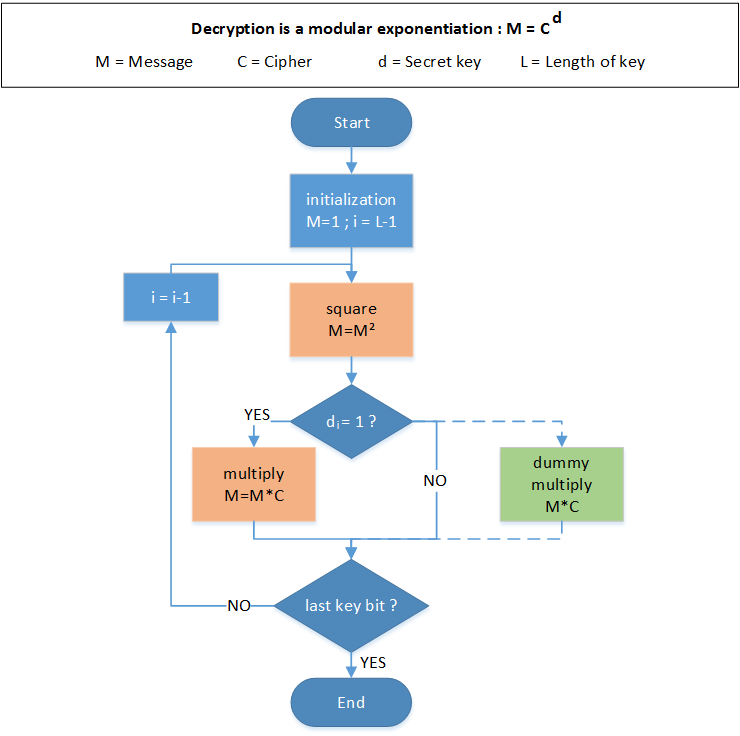
The RSA-Algorithm implemented in the Simple Power Analysis demo application is reduced
to a simple 8-Bit implementation for illustrative purposes. The physical smart card interface
used is contact-based.
By monitoring the voltage drop across a shunt resistor it is possible to measure the power
consumption of an RSA operation on a digital oscilloscope. Observation of the resulting
measurements reveal that it is possible to visually distinguish single square operations
from square and multiply operations. By iteratively logging this sequence of operations,
the bits of the exponent, that is the secret key, can be directly identified.
By using countermeasures like the square and always multiply algorithm, the decoding
of the exponent bits can be prevented and the key protected. The square and always
multiply algorithm is illustrated in the block diagram.
- Fault Attack demo
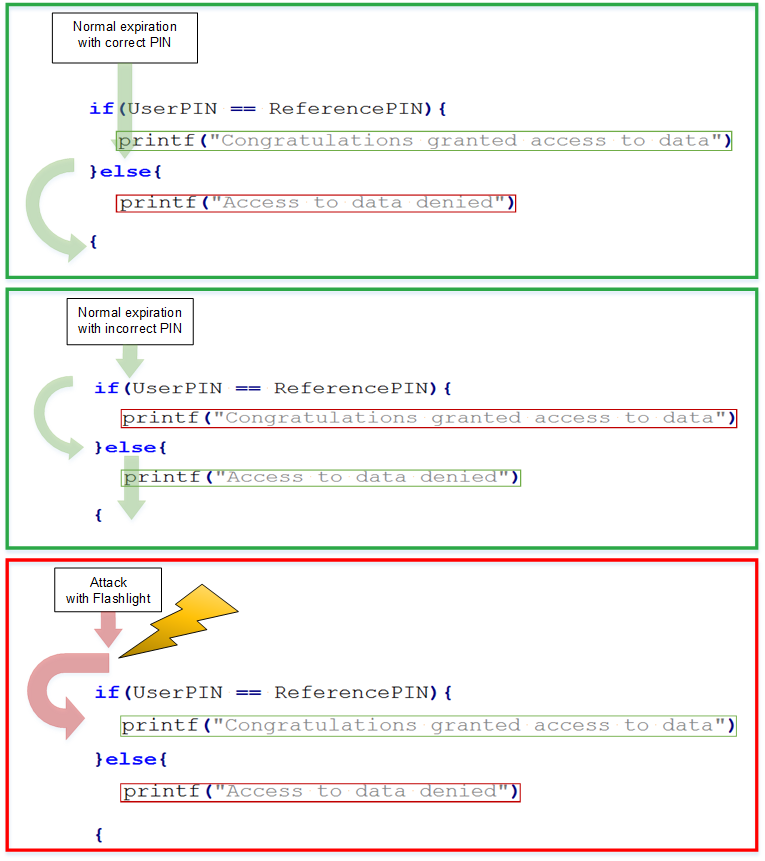
The Fault Attack demo shows what can happen at software execution, if a flashlight is
fired on a decapsulated chip which has no security measures.
With simple tools – a mechanical grinding tool and some chemical etchant - it is
possible to expose the surface of the chip and crudely inject photons into the
sensitive silicon substrate.
In this case the flashlight causes a skip in the execution of the PIN verification
code if the flash is discharged close to the surface at the correct moment.
In normal function expiration the UserPin is either correct or incorrect and access
to the data is granted or denied accordingly. With a successful flashlight
attack it doesn’t matter which value for UserPin is entered - after several tries
the attacker skips the query and has access to the secret data.
- RFID Relay Attack demo
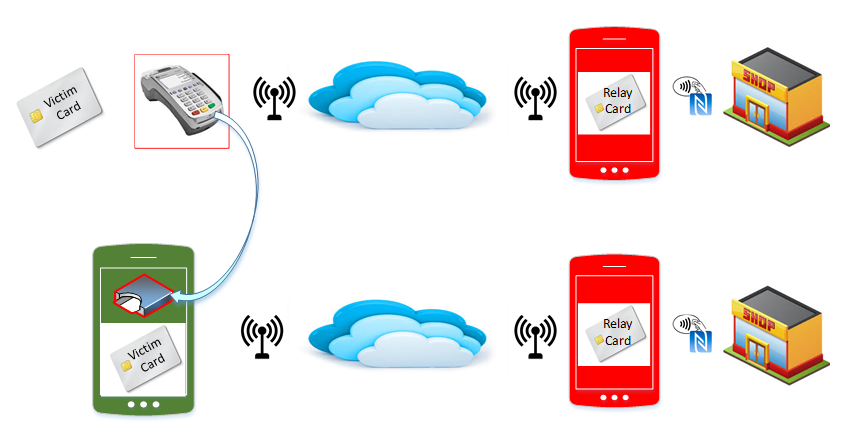
The RFID Relay Attack demo demonstrates a new paradigm in
relay attacks in the context of software emulated smartcards on mobile devices.
Previous conditions about proximity of the attacker to the victim and the time
when the victim is approached, are negated. With a software emulated smartcard
on a mobile device an attacker can intercept and relay the transaction of a
potential victim remotely. This new attack paradigm greatly enhances the value
of this attack for criminals, and consequently will result in greater malware development efforts.
- Additional Information on the individual attacks